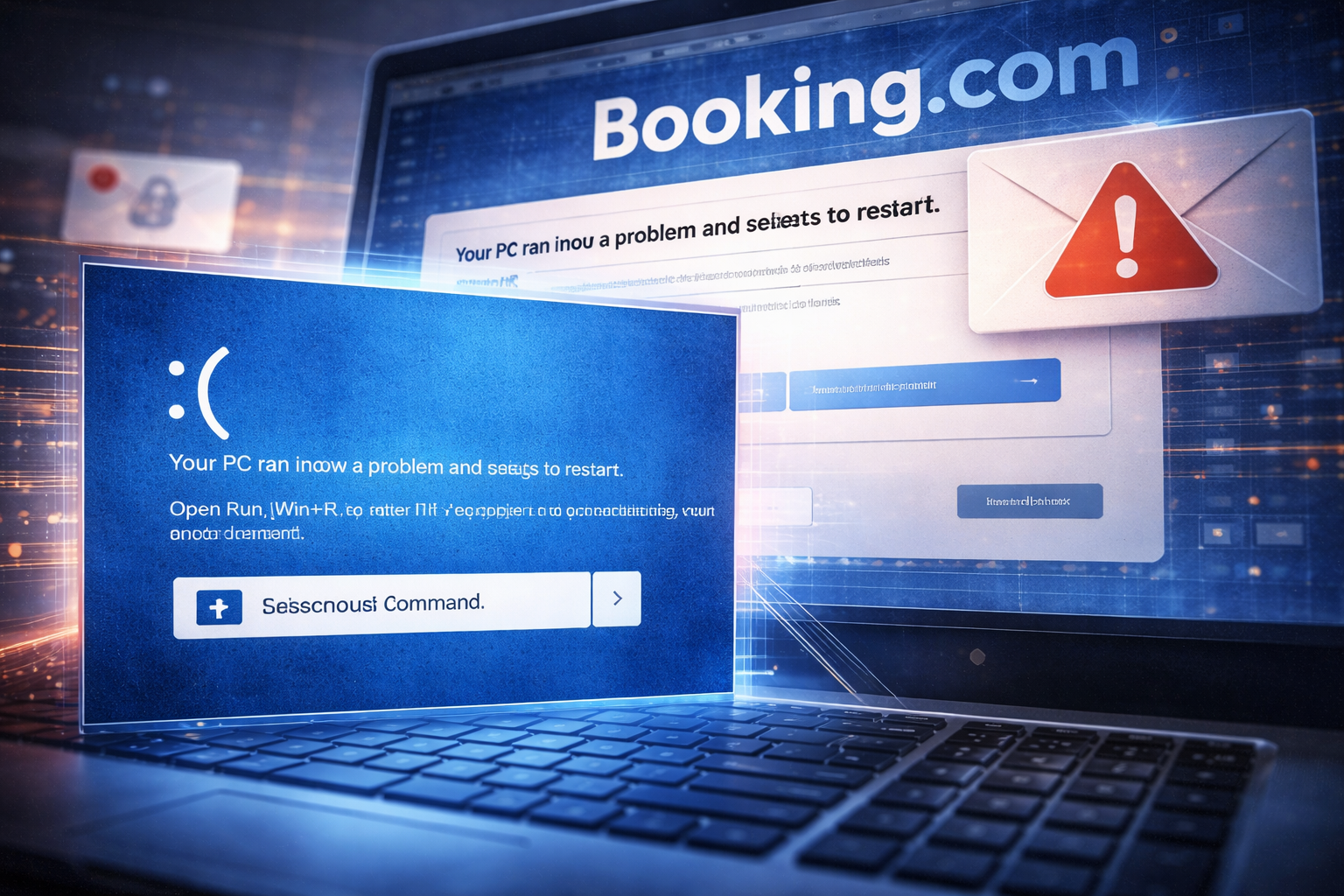
Booking.com is being impersonated in a social engineering campaign that uses fake error messages and simulated system failures to trick users into installing malware. The activity involves a technique known as ClickFix, which relies on user interaction rather than software exploits to compromise systems.
According to cybersecurity researchers, the campaign begins with phishing emails that appear to come from Booking.com. The messages typically claim that a reservation has been cancelled or that a payment issue has occurred, sometimes showing a high charge to prompt urgency. Recipients are directed to click a link to review the supposed problem.
The link leads to a fraudulent website designed to resemble Booking.com. The page displays what appears to be a loading or verification issue and prompts the user to take action to resolve it. After interacting with the page, the browser displays a fake Windows Blue Screen of Death intended to convince the user that a serious system error has occurred.
The screen displays step-by-step instructions that guide the user to open the Windows Run dialog and paste a command to resolve the issue. If followed, the command launches a PowerShell script that downloads and executes additional malicious code. This process allows the attackers to install malware while making the user believe they are restoring their system.
Researchers said the malware deployed in the campaign includes a remote access trojan that allows attackers to maintain control of the infected system. The infection process also attempts to weaken security settings to reduce the chance of detection or removal.
The campaign has been observed targeting organisations that regularly interact with Booking.com, particularly in the hospitality sector. Staff members responsible for reservations or payments are more likely to engage with the messages, increasing the likelihood of successful infection.
The ClickFix technique avoids direct exploitation by persuading users to run commands themselves. This approach can bypass some automated security controls, since the actions appear to be initiated by the user rather than by malicious software.
Researchers advised users to treat unexpected emails about bookings or payments with caution and to avoid following instructions that require running commands or fixing alleged system errors. They said legitimate companies do not ask users to resolve issues by executing scripts or pasting commands into system tools.
The campaign highlights how social engineering continues to evolve by combining trusted brand impersonation with realistic technical deception to gain access to systems.