The “Plesk – Resource Usage Limits” email scam is a phishing email that pretends to be an automated hosting alert. It claims that a hosting account has hit its limits and that immediate action is required to prevent service disruption. The email is not a real system notification. It is designed to push recipients into clicking a link and entering account credentials on a fake sign-in page.
The email usually presents the situation as urgent and technical. It may state that resource usage has exceeded the allowed limits and that services could be restricted if the issue is not addressed promptly. The message is written to worry recipients who manage websites, business email, or hosting services. Even if the recipient does not use Plesk, the email can still create uncertainty because the wording sounds like a standard hosting warning.
A link or button is typically included, framed as the step needed to review the problem. In the “Plesk – Resource Usage Limits” email scam, that link does not lead to a legitimate hosting provider page. It opens a fraudulent website that imitates a hosting control panel login. The page is built to capture usernames and passwords. Any credentials entered are collected by scammers rather than being used to fix anything.
This scam can lead to serious damage if the recipient enters valid hosting credentials. Access to a hosting control panel can allow scammers to manage website files, modify settings, create new email accounts, and change domain-related configuration. It can also be used to interfere with website content, redirect visitors to unsafe pages, or use the hosting environment to send additional scam emails.
Some versions of the scam attempt to collect more than a login. The fake page may request extra details such as billing information, account identifiers, or payment card data. These requests are presented as part of an “upgrade” or “resource increase” process. They are not legitimate. They exist to expand the theft beyond credentials and into financial fraud.
The “Plesk – Resource Usage Limits” email scam works because hosting alerts are a familiar concept. Real hosting platforms do send notifications about limits, but legitimate warnings do not require signing in through a random link in an unexpected email. Hosting status should be checked by signing in through the known control panel address used by the hosting provider, not through a page reached from an unsolicited message.
The full “Plesk – Resource Usage Limits” phishing email is below:
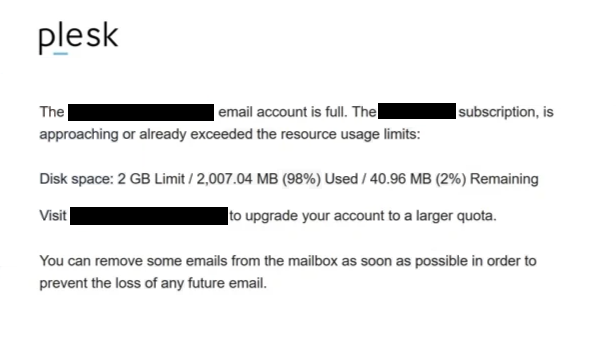
Subject: Notification: Resource usage by subscription has exceeded the allotments
plesk
The – email account is full. The – subscription, is approaching or already exceeded the resource usage limits:
Disk space: 2 GB Limit / 2,007.04 MB (98%) Used / 40.96 MB (2%) Remaining
Visit – to upgrade your account to a larger quota.
You can remove some emails from the mailbox as soon as possible in order to prevent the loss of any future email.
Facebook LinkedIn Twitter YouTube
The system generated this notice 21.1.2026 11:52:04 UTC.WebPros International GmbH Vordergasse 59 Schaffhausen, CH 8200 Switzerland
How this phishing email is sent and how to recognize it
The “Plesk – Resource Usage Limits” email scam is distributed through spam campaigns. Scammers send large volumes of emails to many recipients, including businesses and individuals. The message does not need to confirm that the recipient uses Plesk or manages hosting. It relies on the fact that the topic sounds credible and can trigger a quick response from someone who does not want their website or email services interrupted.
The sender’s details are one of the first things that can reveal the scam. The display name may reference Plesk or a hosting support team, but the actual sending address often comes from an unrelated domain. Some emails also use reply-to addresses that do not match the claimed organization. This mismatch is a common sign that the email was not sent by a real service provider.
The content of the email is often vague. The “Plesk – Resource Usage Limits” email scam may mention limits being reached without identifying a specific server, account name, or hosting plan. Real alerts usually include details that match the hosting environment or direct the recipient to log in through the normal hosting dashboard they already use.
The link in the email is another strong indicator. Phishing emails often hide the real destination behind a button that suggests a safe action, such as reviewing usage or restoring service. If the link points to an unfamiliar domain, or one that does not match the recipient’s hosting provider, it should not be trusted. A page that imitates a control panel login can look convincing, but the domain name and lack of trusted context can reveal that it is not genuine.
The request itself is also suspicious. A real hosting provider does not require immediate login through an email link to avoid instant suspension. Threats that push urgent action are common in phishing because they discourage verification.
Site Disclaimer
2-remove-virus.com is not sponsored, owned, affiliated, or linked to malware developers or distributors that are referenced in this article. The article does not promote or endorse any type of malware. We aim at providing useful information that will help computer users to detect and eliminate the unwanted malicious programs from their computers. This can be done manually by following the instructions presented in the article or automatically by implementing the suggested anti-malware tools.
The article is only meant to be used for educational purposes. If you follow the instructions given in the article, you agree to be contracted by the disclaimer. We do not guarantee that the artcile will present you with a solution that removes the malign threats completely. Malware changes constantly, which is why, in some cases, it may be difficult to clean the computer fully by using only the manual removal instructions.