The “Webmail System Update” email scam is a deceptive email designed to pressure recipients into interacting with a phishing link under the pretense of a required account update. The email is presented as an official notification related to a webmail service and claims that a system update requires immediate action to avoid account disruption. The message frames the situation as time sensitive and warns that failure to comply will result in limited access or suspension of the email account.
The email is not associated with any legitimate service provider. It is distributed by scammers who impersonate email administrators or technical support teams. The content is structured to appear operational rather than promotional. It references system maintenance, security improvements, or compatibility updates and instructs the recipient to confirm or update account details. This framing is intended to reduce suspicion and encourage compliance.
Recipients who follow the link provided in the email are directed to a phishing web page designed to resemble a legitimate webmail login screen. The page requests email credentials, including the email address and password. Any information entered into these fields is transmitted directly to the scammers. The page does not perform any update or verification function. Its sole purpose is to harvest login credentials.
Compromised email accounts present a significant risk. Access to an email inbox allows scammers to reset passwords for other accounts, intercept private communications, and distribute additional scam emails from a trusted address. Business email accounts are particularly valuable because they can be used to impersonate employees, request payments, or access internal systems. Personal email accounts may also contain sensitive information such as financial statements, contact lists, and account recovery messages.
The “Webmail System Update” email scam relies on impersonation rather than technical exploitation. The email does not indicate malware infection or claim that the device is compromised. Instead, it focuses on administrative language and routine maintenance to appear credible. This approach reduces alarms while still creating urgency, making it easier to deceive recipients who regularly receive legitimate service notifications.
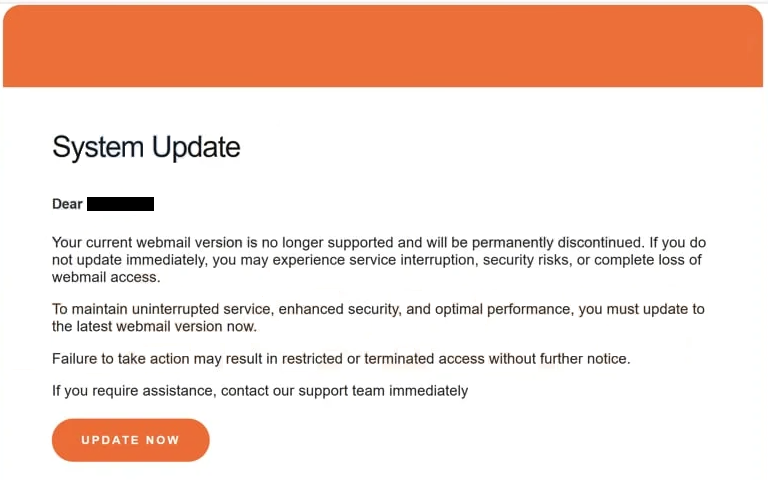
The full “Webmail System Update” phishing email is below:
Subject: URGENT: Immediate Webmail Update Required to Prevent Access Loss.
System Update
Dear -,
Your current webmail version is no longer supported and will be permanently discontinued. If you do not update immediately, you may experience service interruption, security risks, or complete loss of webmail access.
To maintain uninterrupted service, enhanced security, and optimal performance, you must update to the latest webmail version now.
Failure to take action may result in restricted or terminated access without further notice.
If you require assistance, contact our support team immediately
UpDaTe NoWCritical: This update ensures compliance with the latest security standards.
©2026 CPanel Inc
Our Services | Unsubscribe | Contact us
How email scams of this type are delivered
Email scams such as the “Webmail System Update” email scam are distributed through large-scale spam campaigns. Scammers obtain email addresses from data breaches, public directories, marketing lists, and automated address generation. Messages are sent in bulk, often using compromised servers or misused email infrastructure to bypass basic filtering systems.
The emails are crafted to avoid obvious indicators of fraud. Subject lines are short and administrative in tone, often referencing updates, notifications, or required actions. The message body typically avoids excessive formatting or branding to resemble internal system emails rather than marketing communications. This minimal presentation helps the scam blend in with legitimate operational messages.
Sender addresses are often spoofed to resemble real domains. While the underlying email headers may reveal inconsistencies, the visible sender name is designed to look official. In some cases, the displayed domain closely resembles that of a legitimate provider, relying on subtle spelling differences that are easy to overlook. This technique increases the likelihood that the email will be trusted at a glance.
Links embedded in the email commonly use generic anchor text such as “update now” or “verify account.” The destination address may appear shortened or masked behind text that suggests a legitimate webmail site. Once clicked, the link leads to a phishing web page hosted on a compromised website or a domain registered specifically for scam activity. These pages are often removed quickly and replaced with new ones to avoid detection.
The success of this scam depends on exploiting routine behavior. Email users are accustomed to receiving service notices and performing occasional account confirmations. By presenting the request as part of standard system maintenance, the scam avoids raising immediate suspicion. The threat of account restriction or service interruption adds pressure, increasing the chance of impulsive action.
Unlike malware-based threats, this scam does not require the installation of software or interaction with attachments. It relies entirely on credential theft through direct user input. This makes it effective across devices and operating systems, as it does not depend on specific vulnerabilities. Any device capable of opening the email and loading the phishing page can be affected.
Site Disclaimer
2-remove-virus.com is not sponsored, owned, affiliated, or linked to malware developers or distributors that are referenced in this article. The article does not promote or endorse any type of malware. We aim at providing useful information that will help computer users to detect and eliminate the unwanted malicious programs from their computers. This can be done manually by following the instructions presented in the article or automatically by implementing the suggested anti-malware tools.
The article is only meant to be used for educational purposes. If you follow the instructions given in the article, you agree to be contracted by the disclaimer. We do not guarantee that the artcile will present you with a solution that removes the malign threats completely. Malware changes constantly, which is why, in some cases, it may be difficult to clean the computer fully by using only the manual removal instructions.