A new malware outbreak
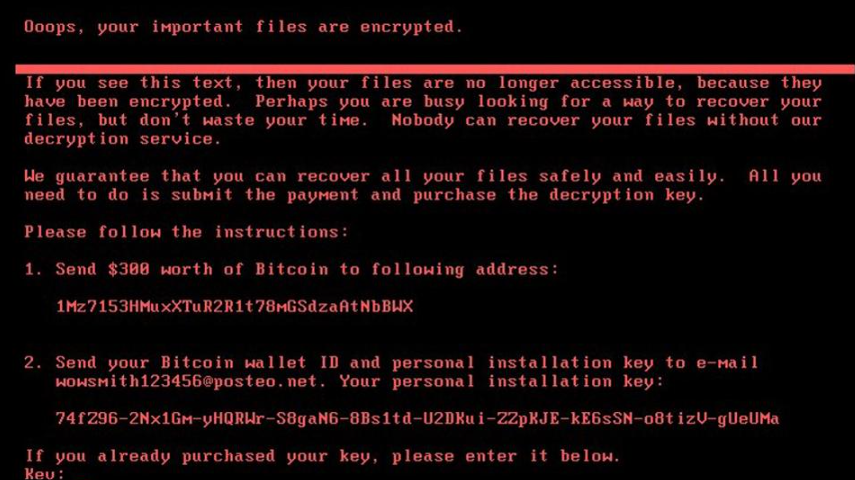
Only last month, WannaCry made headlines all over the world after it managed to infect more than 200 000 computers in over 150 countries using a vulnerability in Windows. In the last couple of days, we saw another wide-spread attack that was first believed to be a ransomware outbreak. It has a variety of different names but is most commonly referred to as Petya or NotPetya. 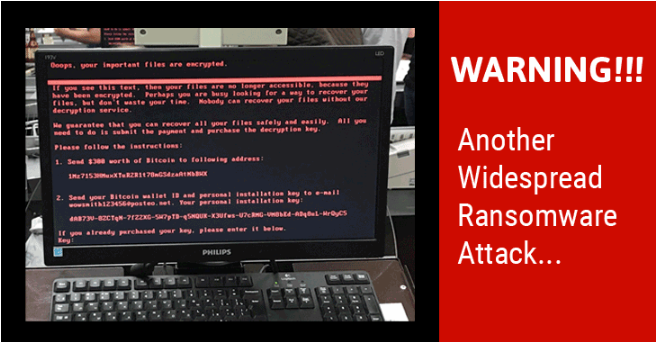 Petya is a known ransomware that has been around for a while but its developer has denied involvement in this new attack, hence why it is called NotPetya by some. At first glance, it acts like the typical ransomware, it encrypts files and then asks that victims pay to restore them. Upon further investigation, the reality is quite different. Researchers have come to the conclusion that NotPetya is not actually ransomware but rather wiper malware. What they suggest is that it is not meant to make money, it is meant to destroy systems.
Petya is a known ransomware that has been around for a while but its developer has denied involvement in this new attack, hence why it is called NotPetya by some. At first glance, it acts like the typical ransomware, it encrypts files and then asks that victims pay to restore them. Upon further investigation, the reality is quite different. Researchers have come to the conclusion that NotPetya is not actually ransomware but rather wiper malware. What they suggest is that it is not meant to make money, it is meant to destroy systems.
Ukrainian company believed to have been the ground zero
Researchers in various security companies believe that an accounting software vendor based in Ukraine, M.E.Doc, has accidentally spread the malware that led to the infection of thousands of computers. Although the company itself has denied this, malware specialists believe that the company was hacked and their servers were compromised. The hackers released a malicious software update and the customers who installed it ended up infecting their computers with NotPetya. The malware then gained credentials to local networks and by using certain tools, it managed to spread to computers on the same network. It has also been reported that the exploit used by WannaCry, EternalBlue, together with Eternalromance is used in this attack as well. The good news is that it does not spread through the Internet, only via LAN. This, however, raises the question of how the malware managed to spread to other countries, where the infected companies had no contact with M.E.Doc.
How does NotPetya work?
Just like the original Petya ransomware, NotPetya does not encrypt files one after the other. What it does is it reboots the computer and encrypts the hard drive’s master file table (MFT) and makes the master boot record (MBR) unable to function properly. Petya replaces the encrypted MBR copy with a malicious code and your computer is unable to boot. Instead, it displays the ransom note. This is where NotPetya differs from Petya. Comae Technologies researcher Matt Suiche, states that the original Petya ransomware encrypts the disk in way so that it could reverse the changes if needed. NotPetya, on the other hand, does permanent and irreversible damage to the disk.
Specialists think NotPetya is not meant to make money, it is meant to destroy
When the whole process is complete, the infected computer will show a ransom note. The message states that files have been encrypted and that you need to pay $300 worth of Bitcoin to the provided address. When the victim pays the ransom, they are supposed to send their payment ID and the personal installation key, which is provided in the note, to wowsmith123456@posteo.net. However, the German email provider has made the decision to close this account, which means that you cannot get in contact with the hackers. Even if you pay, the criminals would have no way of knowing who paid.
This is not the only reason why you should not pay. Further investigation into the malware has uncovered that the people behind the attack have no intention of restoring any files. It simply is not possible. The above mentioned installation key ID is a crucial part of the decryption process. It stores information about the victim and the decryption key. The installation ID you see in the ransom note is just random data, which suggests that NotPetya was not meant to make money.
Malware researchers are now categorizing NotPetya not as ransomware but as a wiper that basically destroys your files with no way to restore them. While it does not actually delete any files on the system, once your files are encrypted, there is no way to decrypt them, which leaves them useless. And this is thought to be intentional. Meaning that going into this, developers behind the infection were not aiming to earn money.
Ukraine seems to have the biggest amount of victims. It has reported that the government organization managing Chernobyl disaster zone had to switch to manual radiation monitoring because they had to shut down all Windows computers. Major Ukrainian energy companies seem to have also been affected. Seeing as Ukraine took the hardest hit and the fact that everything started there, it is believed the the country was the intended target in what some believe to have been a nation state attack.
What you could have done to prevent disastrous outcomes?
Backup. If the WannaCry attack has taught both individual users and business something, it is the importance of having backup. Seeing as there is no way of decrypting files, even if you pay, the only thing that could have saved you a lot of trouble is files stored somewhere else. We live in a world where malware lurks on every corner on the Internet but people are far from being security cautious. This is proven every day when users report that their files have been encrypted and there is no backup.
Cyber threat is real. No matter who the main targets of this attack were, it is important to understand that it is not something that cannot happen to you and therefore you do not need to be cautious. And until people realize that and make sure they are doing everything they can to protect themselves, it is only going to get worse.
References