Ransomware is one of those nasty viruses that you really do not want to have on your computer. It encrypts files and then demands money if victim want to get them back. However, users are increasingly becoming aware of how ransomware infects computers. Due to this, less computers get infected, and developers get less money. Therefore, ransomware developers have thought of a different way to achieve their goal. A new ransomware, known as Popcorn Time, is making headlines all over Internet because of its new way of spreading itself, and it is quite nasty.
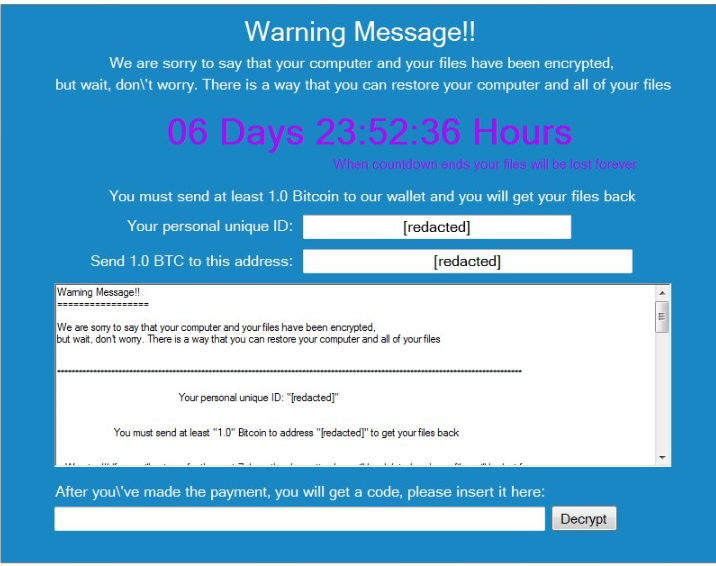
Popcorn Time (not to be confused with the application with the same name that allows you to stream films and TV shows) has been discovered earlier this month and at first glance, it seems just like any other ransomware. It encrypts files using the AES-256 encryption algorithm and then demands that victims pay money to restore the files. It asks for 1 Bitcoin (around $780) and supposedly, victims who pay would receive the decryption key. However, a closer look at the ransom note reveals that there is a second way to decrypt files.
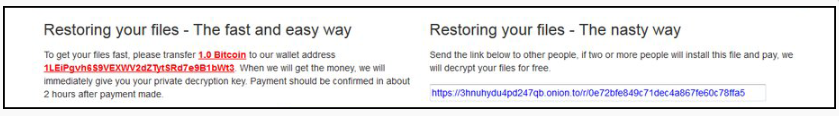
The developers behind Popcorn Time refer to it as the “nasty way” and it is, indeed, quite nasty. If a victim was to infect two other computers, whose owners would pay the ransom, he/she would get the decryption key for free. The victims are given a link, which they are supposed to send to other users so they could get infected. Once the developers confirm that the two users the victim infected have paid the ransom, the original victim would get the decryption key. Currently, there is no other way to restore the files, a decryption key is needed. Unless, of course, you have backup. It has also been reported that if the victim enters the wrong decryption key 4 times, the ransomware will start deleting files.
Usually, users get infected with ransomware when they open malicious email attachments. This is why it is very important that users are careful and make sure attachments are safe to open. Once the virus downloads onto the computer, it encrypts files. Until some days ago, Popcorn Time ransomware was still in development mode and only encrypted some files but now it seems to be able to reach files in My Documents, My Pictures, My Music, as well as the desktop. Users will know which files have been encrypted because they will have the .filock file attachment. A ransom note will then appear and inform the victims that their files have been encrypted. The developers also explain why they did what they did. According to them, they wish to take matters into their own hands and raise money for Syria. They go on to explain that the ‘world has remained silent’ and that they need to take action to keep living. They also assure victims that the money will go to helping people, as well as apologize for making them pay. While this could be a completely legitimate story, there is also a chance that it is made up. Such a story, especially since the developers claim to have lost their family members, would pull the heartstrings of many victims and encourage them to pay. However, one must also consider the possibility that it is a ploy to make more users pay.
Files associated with the Popcorn Time Ransomware
- restore_your_files.html
- restore_your_files.txt
- popcorn_time.exe
Registry entries associated with the Popcorn Time Ransomware
- HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run “Popcorn_Time”
- [path_to]\popcorn_time.exe
Network Communication associated with the Popcorn Time Ransomware
- https://3hnuhydu4pd247qb.onion
- http://popcorn-time-free.net
Installer Hashes
- SHA256: fd370e998215667c31ae1ac6ee81223732d7c7e7f44dc9523f2517adffa58d51
Getting infected with ransomware can have awful consequences. And victims who are thinking of spreading the ransomware need to understand that not only will they be helping ransomware developers, but they will also be essentially doing the same thing as the cyber criminals.