When it comes to hacking ATMs, we are used to criminals psychically tampering with the machine in order to steal money but a recent report, a collaboration between Trend Micro, a security software company, and Europol’s EC3 (European Cybercrime Center), reveals that network-based ATM attacks are becoming more and more common. While in the past, criminals would need to have psychical access to an ATM in order to infect it with malware, now they can do it remotely, by hacking the bank’s network and taking control over the cash machines.
 Physically infecting ATMs with malware has always been rather risky, as it requires tinkering with the machine quite obviously in public. That is why crooks preferred to use more remote ATMs rather than those in shopping malls, busy streets, etc. The so called “skimming” devices would be attached, a bogus pad could be put over the real one, but they are quite noticeable to those who are familiar with it. And as people are becoming more and more careful about ATMs, it is no longer so easy to steal money this way. This is where network-based ATM attacks come in. Crooks no longer have to risk getting caught attaching something to an ATM because they do not need physical access.
Physically infecting ATMs with malware has always been rather risky, as it requires tinkering with the machine quite obviously in public. That is why crooks preferred to use more remote ATMs rather than those in shopping malls, busy streets, etc. The so called “skimming” devices would be attached, a bogus pad could be put over the real one, but they are quite noticeable to those who are familiar with it. And as people are becoming more and more careful about ATMs, it is no longer so easy to steal money this way. This is where network-based ATM attacks come in. Crooks no longer have to risk getting caught attaching something to an ATM because they do not need physical access.
“As banks are starting to realize how much at risk they are from physical ATM attacks and therefore take steps to protect their machines accordingly, the attackers are catching up with alternative infection vectors. Enter network-based ATM attacks,” the report explains.
Network-based ATM attacks
Although there are very significant differences, an ATM is essentially a Windows computer with a safe full of money. And the main thing to note here is that the majority of ATMs run Windows XP or Windows Embedded. Support for both versions has been discontinued in 2014 and 2016 respectively, which means they no longer get their vulnerabilities patched. And the recent WannaCry and NotPetya attacks just go to show how much of a problem unpatched systems are.
“Such systems no longer receive critical security updates, so in the most basic sense, system vulnerabilities are not addressed, let alone resolved,” Trend Micro explains. This allows hackers to take advantage of those security gaps to gain access to an ATM.
In order to carry out a network-based ATM malware attack, hackers need to get into a bank’s network. The report explains that the most common method used to access the network is phishing.
“In our observation of the different attacks that have been reported, the criminals hack into the bank’s corporate network through ways as simple as phishing emails directed at the bank’s employees. This is by no means the only way to accomplish such a hack but it is the easiest and therefore the most common one.”
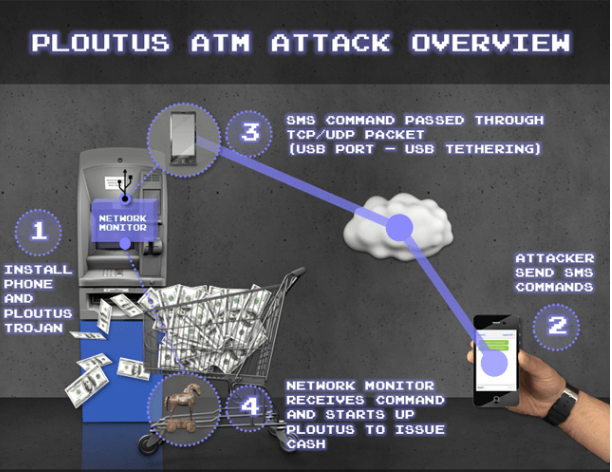
When the malware gains access to an ATM’s network, it can have the ATM dispense cash, which would then be picked up by standby criminals.
Trend Micro notes that even though network-based attacks are much more sophisticated and thus need more work, they are appealing to crooks because they allow them to steal money without physically tampering with an AMT.
“In the past, banks might have thought that network segregation was enough to keep their ATM networks safe from cyber crooks. This is no longer the case. Law enforcement agencies should be well-informed that criminals have ATMs firmly in their crosshairs, and financial organizations need to take more steps to secure their ATM installations by deploying more security layers,” the report concludes, although it notes that banks take the threat seriously and are deploying solutions to fill in the security gaps.