Mzqw ransomware is one of the most recent versions of the Djvu/STOP ransomware. It’s a type of malware that encrypts files and demands payment for their recovery. All personal files will be affected by this ransomware. This is why Mzqw ransomware is considered to be a very dangerous infection. The ransomware adds .mzqw to encrypted files, hence why it’s dubbed Mzqw ransomware. Unfortunately, unless you have a specific decryptor, you will not be able to access any files with this extension. And it will be difficult to obtain the decryptor because only cybercriminals currently have it. They will try to sell it to you for $980.
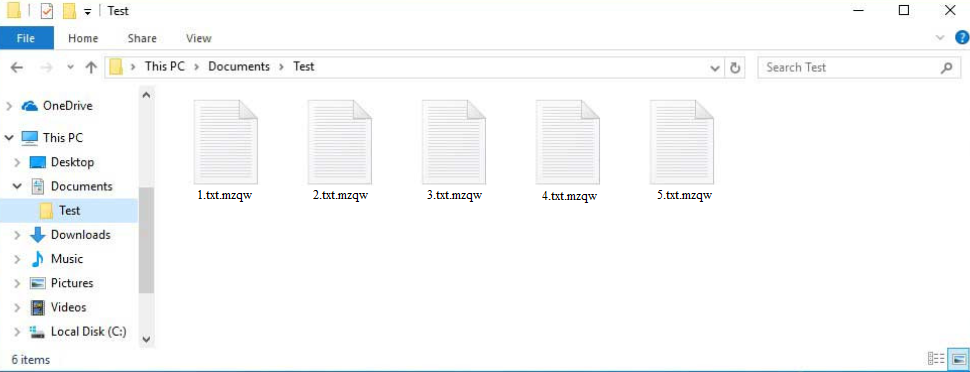
Your files will be encrypted as soon as the ransomware is initiated. To distract the victims from what’s happening to their files, the ransomware will display a fake Windows update window. All personal files—basically everything that users would be prepared to pay for—will be targeted, including photos, videos, and documents. The files will have a .mzqw extension. For instance, text.txt would become text.txt.mzqw if encrypted.
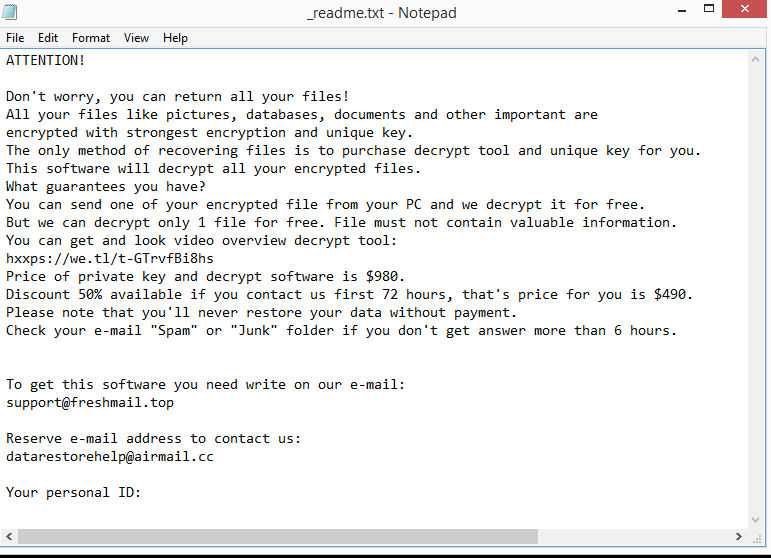
The ransomware will drop _readme.txt ransom notes in every folder that contains encrypted data. The note describes how victims can obtain the decryptors they need. Cybercriminals demand $980 for the decryptor. The note does mention that users who contact malicious actors within the first 72 hours will receive a 50% discount, but you should be skeptical of these claims. Paying the ransom is not advised for several reasons, but the main one is that you will not necessarily get the decryptor. Nothing stops cybercriminals from just taking your money and not sending anything in return. Additionally, the money you pay will be used to fund other malicious activity in the future. Whether to pay or not is your choice but you do need to be aware of the risks.
Do not connect to your backup while ransomware is still active if you have backed up your files before file encryption. You should only access your backup after you remove Mzqw ransomware from your computer. It is strongly recommended to use an anti-virus program because the infection is quite sophisticated.
If you don’t have a backup, your options for file recovery are quite limited. It’s possible that a free Mzqw ransomware decryptor will eventually be released but when or even if that will happen is not certain. The encryption keys used by this malware are specific to each user since it encrypts data using online keys. A free decryptor is unlikely unless those keys are released by the cybercriminals themselves or by law enforcement. However, you should nonetheless regularly search for a free Mzqw ransomware decryptor and back up your encrypted files. It’s worth mentioning that there are many fake decryptors promoted on various questionable forums so you need to be careful. Downloading the wrong decryptor could lead to more malware infections.
How are ransomware infections distributed?
It is well known that having poor online habits greatly increases your chances of getting malware on your computer. It’s mostly because users with poor habits tend to engage in riskier online activities. We strongly recommend taking the time to learn proper browsing practices and familiarize yourself with malware distribution methods.
Torrents are one of the most popular ways for malware to be distributed, and malware is often encountered there. Due to the poor moderation of many torrent websites, cybercriminals are able to upload torrents containing malware. Malware is frequently found in torrents for well-known films, TV shows, video games, software, etc. The more well-known something is, the more likely its torrent will contain malware. Torrenting copyrighted content is essentially theft as well, in addition to being dangerous for computers and users’ data.
Malware, however, is also frequently found in email attachments. Because it requires less work, malicious actors like this technique. From numerous hacker forums, malicious actors purchase email addresses, then spam those addresses with emails that contain malware. As long as the attached file is not opened, the emails themselves are not dangerous. But the infection will initiate as soon as victims open the infected file.
Thankfully, users ought to be able to identify bogus emails quite easily. Usually, malicious senders pose as representatives of legitimate businesses whose services users use. However, the emails are full of spelling and grammar mistakes, which quickly exposes them. Companies will make every effort to prevent mistakes in official correspondence since they look unprofessional. But many malicious actors have very poor English skills, therefore their emails frequently contain mistakes.
Another sign of a potentially malicious email is you being addressed using generic words instead of your name. If you are addressed using “User,” “Member,” “Customer,” etc., when the sender should know your name, it may be a sign of a malicious email. You will always be addressed by your name in emails from businesses whose services you use.
However, it’s important to note that certain malicious emails might be more sophisticated, especially if cybercriminals have access to specific personal data. Before opening any email attachments, it is strongly advised to scan them with anti-virus software or VirusTotal.
How to delete Mzqw ransomware
It is a sophisticated infection, thus we don’t advise attempting to manually remove Mzqw ransomware. Trying to manually remove could cause your computer additional damage. Furthermore, if you miss any parts of the ransomware, it could subsequently be able to recover. And the backed-up data would also become encrypted if the ransomware managed to recover while you were connected to your backup. Using anti-malware software is significantly easier and safer.
You may safely connect to your backup and begin recovering files once you completely remove Mzqw ransomware from your computer. Back up the encrypted files if you don’t have a backup, then wait for a free Mzqw ransomware decryptor to be released.
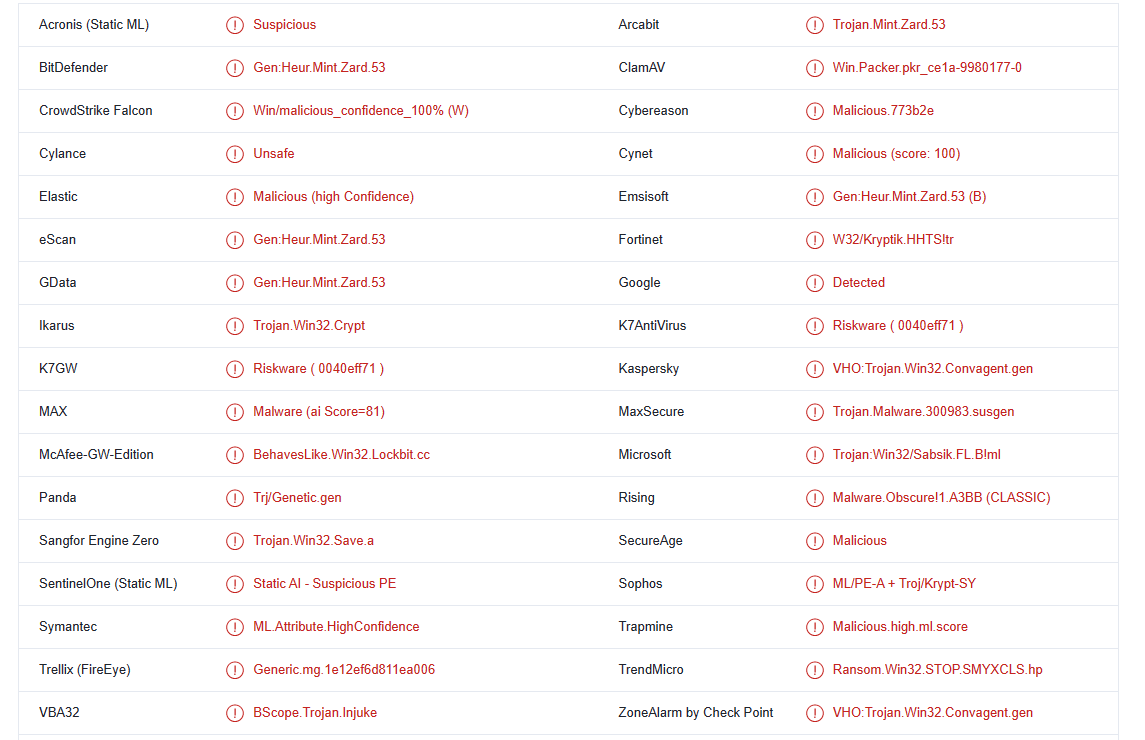
Mzqw ransomware is detected as:
- Gen:Heur.Mint.Zard.53 by BitDefender
- VHO:Trojan.Win32.Convagent.gen by Kaspersky
- Trojan:Win32/Sabsik.FL.B!ml by Microsoft
- Ransom.Win32.STOP.SMYXCLS.hp by TrendMicro
Site Disclaimer
2-remove-virus.com is not sponsored, owned, affiliated, or linked to malware developers or distributors that are referenced in this article. The article does not promote or endorse any type of malware. We aim at providing useful information that will help computer users to detect and eliminate the unwanted malicious programs from their computers. This can be done manually by following the instructions presented in the article or automatically by implementing the suggested anti-malware tools.
The article is only meant to be used for educational purposes. If you follow the instructions given in the article, you agree to be contracted by the disclaimer. We do not guarantee that the artcile will present you with a solution that removes the malign threats completely. Malware changes constantly, which is why, in some cases, it may be difficult to clean the computer fully by using only the manual removal instructions.