What is GitHub email scam
GitHub email scam refers to a phishing email currently going around trying to steal users’ login credentials for GitHub. The emails part of the current phishing campaign are claiming that users need to verify their email addresses by clicking on the displayed button, which if pressed would redirect users to a phishing site that imitates GitHub.com. Apart from the URL, the site may look completely identical, and unsuspecting users may try to log in, only to give away their login credentials to cyber criminals. If the account is not protected with two-factor-authentication, the login credentials would allow malicious actors to access the account.
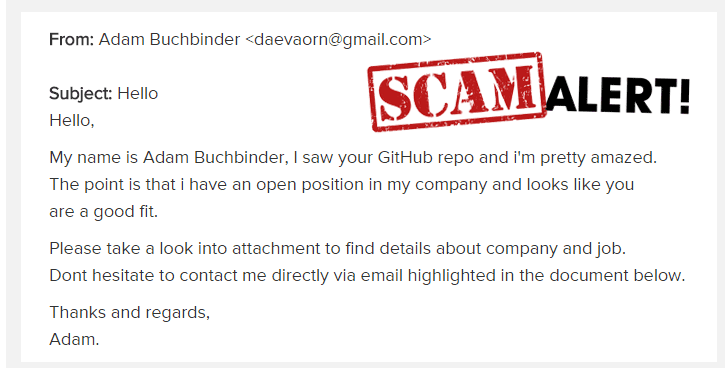
These kinds of phishing emails are incredibly common but fortunately, they are rarely sophisticated enough to actually look convincing. Most of the time, they are full of grammar and spelling mistakes, make little sense and are sent from obviously spam email addresses. This makes phishing emails easy to recognize majority of the time.
If you become target of a phishing attack, more likely than not your email address was part of data breach. Data dumps containing millions of email addresses are constantly sold on the dark web, and those addresses are taken from data leaks and breaches. You can check whether your email has been compromised on haveibeenpwned.
How to recognize a phishing email
As we wrote before, phishing emails are often very obvious and low-effort, meaning as long as you read the contents, you should be able to tell it’s a phishing attempt. For example, one of the GitHub phishing emails going around claims that you need to review your account because a file has been downloaded from your repository. The email states that “a file has been download”, with “download” obviously being in the wrong tense. The word is even highlighted in the email. Obviously, if GitHub were to email you about suspicious activity in your account, the email would not have any grammar or any other kind of mistake as it would look very unprofessional. These kinds of phishing emails are easiest to recognize.
However, some phishing attempts are more sophisticated than others. One of the phishing emails asking users to verify their email addresses looks quite legitimate, at least at first glance. Besides less obvious mistakes like a missing apostrophe or a comma, the email doesn’t have any glaring grammar or spelling errors. The email’s design also greatly resembles GitHub. The email asks that users validate their email addresses in order to straighten security of an account and allow GitHub staff to better assist users in case they forget their passwords. If users press the displayed button to supposedly verify their email, they would be taken to a website that looks almost identical to the legitimate GitHub login page. But if users were to check the site’s URL, they should notice that something’s not right. Instead of github.com/login, the site’s address would be gltnub.com/login, gitnub.com/login, or something similar. It looks similar enough to not be noticed at a fleeting glance but it’s still pretty obvious.
As a general rule, you should always be cautious if you receive unsolicited emails with links. Even if it looks legitimate, you need to be suspicious. If possible, avoid clicking on links in emails, and if you need to access your account, always do so manually. If for whatever reason you need to click on a link and log in to one your accounts, check the URL carefully. Be on the lookout for minor differences such as the letter “m” being replaced with “rn”, or “h” and “n”, and so on. While obviously different now, it may be a less glaring difference when you’re glancing at it quickly.
GitHub email scam removal
If one lands in your inbox, report and delete GitHub email scam. If you haven’t clicking on any links, you don’t need to do anything else. However, if you have clicked on the button/link in the email and put in your login credentials into the phishing site, you need to change your GitHub password immediately. You should also turn on two-factor-authentication for extra security, and consider getting a password manager.