Mztu ransomware is a file-encrypting malware, released by the same cybercriminals operating the Djvu/STOP malware family. It’s one of the most recent releases. This malicious infection will encrypt your personal files and demand money in exchange for their decryptor. You will be able to recognize encrypted files because they will have .mztu added to them. If you have a backup, you will have no issues recovering files. However, if you don’t have files backed up somewhere, your options are much more limited. The malware operators will try to sell you the decryptor for $980 but paying the ransom is very risky.
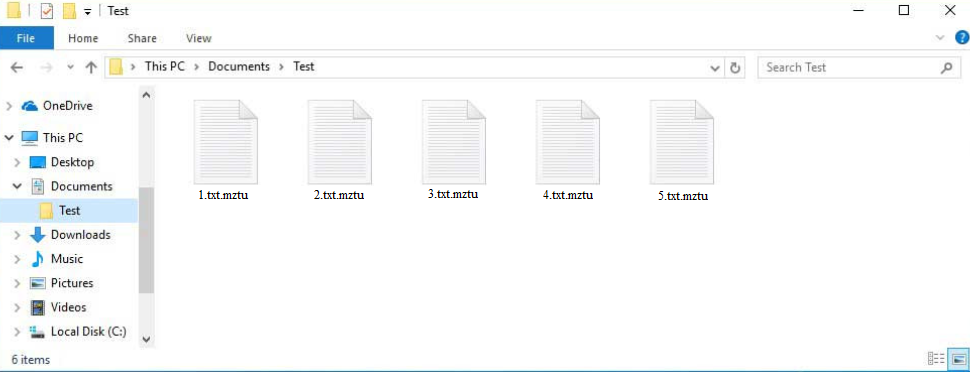
The cybercriminals operating this malware family release new versions on a regular basis, with Mztu ransomware being one of the more recent ones. It can be identified by the .mztu extension it adds to encrypted files. For example, text.txt would be changed to text.txt.mztu if encrypted. All your personal files will have this extension, including photos, videos, and documents. Files with the .mztu extension will essentially be locked until you use a specific decryptor on them.
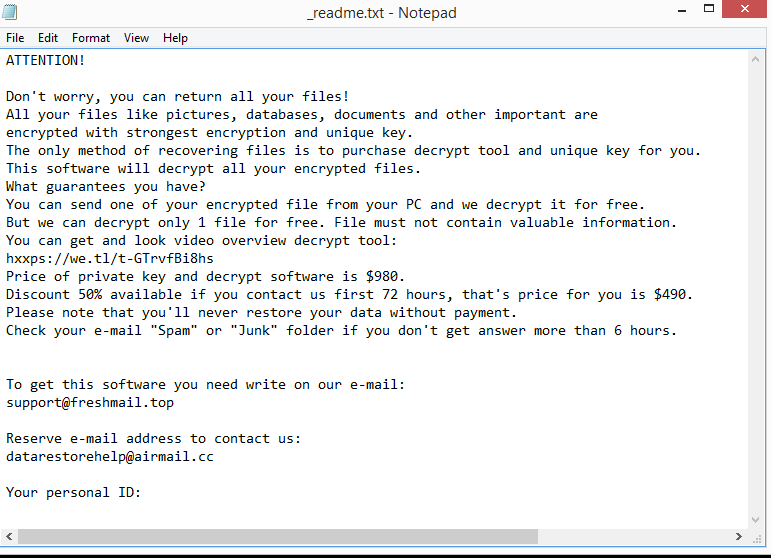
The ransomware will drop a _readme.txt ransom note in all folders that contain encrypted files. The note (displayed above) is very generic but it does have all the necessary information. According to the note, to get the decryptor, you need to pay $980. The note does mention that victims who make contact with the cybercriminals within the first 72 hours will receive a 50% but that is not necessarily true. Although paying the ransom could seem like a good option, it is rather risky. The main risk of paying the ransom is that there is no assurance that you will receive the decryptor. You are dealing with cyber criminals, and there is nothing to stop them from just taking your money. Unfortunately, many victims who paid in the past have not received their decryptors.
Your files can be recovered easily if you have a backup. However, you need to first ensure that you fully delete Mztu ransomware from your computer. Do not try to remove it manually; instead, use anti-malware software. You can safely connect to your backup and begin restoring files once the infection has been completely removed.
If you don’t have a backup, your options are very limited. The only option you have is to wait for a free Mztu ransomware decryptor. There currently is no free Mztu ransomware decryptor but you should nonetheless back up your encrypted files and wait for one to be released. However, when, or rather if the decryptor will be released is not certain. The ransomware versions from this malware family use online keys to encrypt files, which means they are unique to each victim. Unless those keys are released to malware researchers, a free Mztu ransomware decryptor is not very likely. There is a free Djvu/STOP decryptor by Emsisoft that is worth a try but it’s unlikely to work on files encrypted by Mztu ransomware.
Ransomware distribution methods
Users frequently acquire malware infections when opening unsolicited email attachments. If your email address has ever been leaked, it likely ended up being sold on some hacker forum. Malicious actors buy those leaked email addresses for their malware campaigns. For example, a ransomware-carrying malicious email campaign. Malicious files are attached to emails, and when users open the files, the malware is permitted to initiate.
Fortunately for users, malicious emails are typically not difficult to identify. Before opening an unsolicited attachment, you should carefully examine the email itself. Keep an eye out for grammar and spelling mistakes in particular. Senders frequently claim to be from legitimate businesses whose services users use. However, it is immediately clear that the senders are not who they claim to be when the emails are full of grammar and spelling mistakes. You should also pay attention to how emails address you. When a company whose services you use sends you an email, you will always be addressed by name (or the name you have given the company) because it makes the email seem more personal. Distributors of malware, however, would refer to you as a Member, User, Customer, etc. because they do not have access to personal information in most cases and target users on a very large scale.
Since torrent sites are typically poorly monitored, malicious actors also often spread malware via torrents. Malicious torrents can stay up for a long time, infecting large amounts of users. Malware is especially common in torrents for entertainment content, particularly for movies, TV series, and video games. Not only is it dangerous to download copyrighted content for free, but it’s also essentially stealing content.
It’s worth mentioning that malicious spam campaigns can occasionally be far more advanced. In general, you shouldn’t open any attachments from unsolicited emails unless you are certain they are secure. Before opening any attachments, we advise using a virus checker like VirusTotal or performing a scan with anti-virus software.
How to remove Mztu ransomware
Do not try to remove Mztu ransomware manually because you could end up causing more damage to your computer. Ransomware is a sophisticated infection that requires a professional program to get rid of. If you try to do it manually and not remove all ransomware files, the infection may be able to recover. If that were to happen when you were connected to your backup, your backed-up files would become encrypted as well. The files would then be permanently lost.
Once you fully delete Mztu ransomware using anti-virus software, you can connect to your backup if you have it. If you do not have a backup, your only option is to back up encrypted files and wait for a free Mztu ransomware decryptor to be released. If it does get released, it would become available on NoMoreRansom.
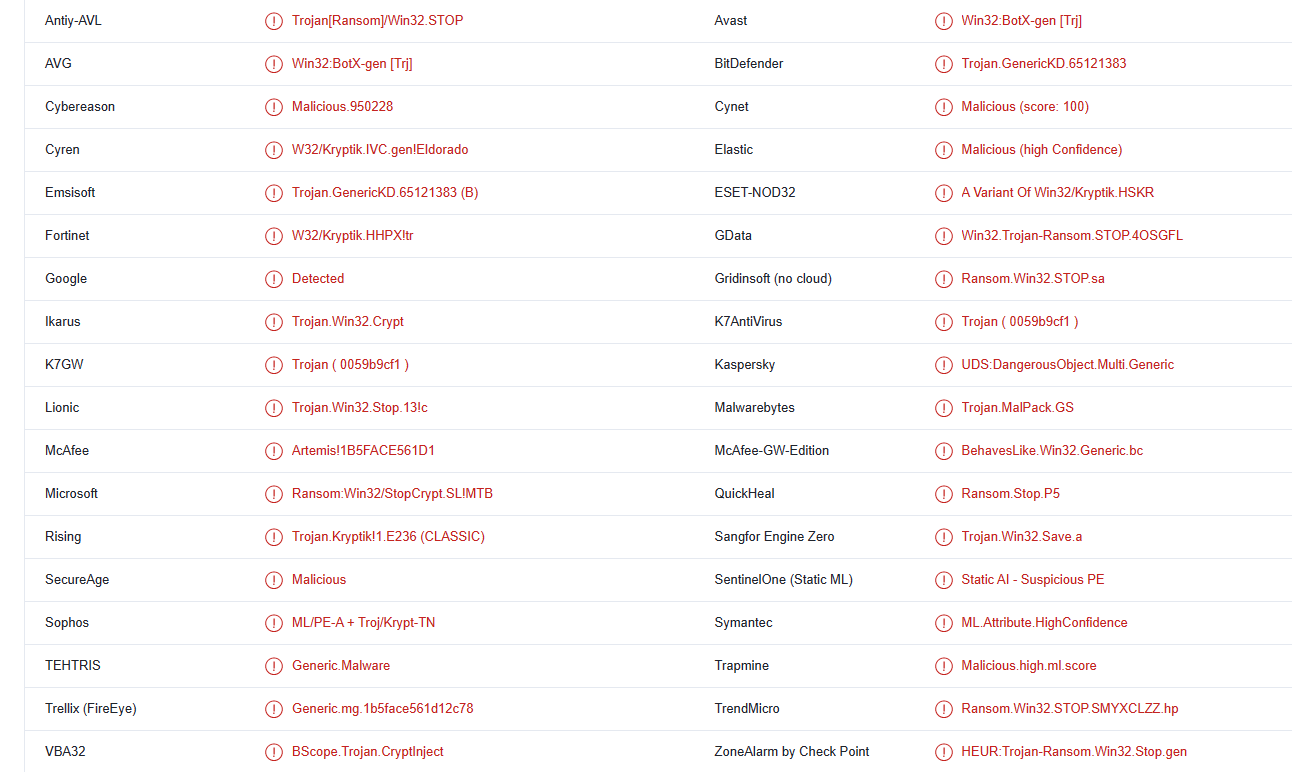
Mztu ransomware is detected as:
- Win32:BotX-gen [Trj] by AVG/Avast
- Ransom:Win32/StopCrypt.SL!MTB by Microsoft
- Trojan.GenericKD.65121383 by BitDefender
- A Variant Of Win32/Kryptik.HSKR by ESET
- Trojan.MalPack.GS by Malwarebytes
- UDS:DangerousObject.Multi.Generic by Kaspersky
- Ransom.Win32.STOP.SMYXCLZZ.hp by TrendMicro
Site Disclaimer
2-remove-virus.com is not sponsored, owned, affiliated, or linked to malware developers or distributors that are referenced in this article. The article does not promote or endorse any type of malware. We aim at providing useful information that will help computer users to detect and eliminate the unwanted malicious programs from their computers. This can be done manually by following the instructions presented in the article or automatically by implementing the suggested anti-malware tools.
The article is only meant to be used for educational purposes. If you follow the instructions given in the article, you agree to be contracted by the disclaimer. We do not guarantee that the artcile will present you with a solution that removes the malign threats completely. Malware changes constantly, which is why, in some cases, it may be difficult to clean the computer fully by using only the manual removal instructions.