Ransomware is one of the most talked about cyber security issues these days, and not without reason. So far, we had three major ransomware attacks that affected hundreds of thousands of users all over the world, and thousands of smaller scale attacks. Ransomware can have pretty harsh consequences.
 If you are a business with backup, you are looking at at least a couple of hours of downtime and chaos while system functionality is restored. If you are without backup, that could mean thousands of important files lost. Same with individual users. Whether you have backup or not, a ransomware attack is highly stressful, but in a lot of cases, it can be avoided. And in this article, we will discuss what methods ransomware uses to infect systems.
If you are a business with backup, you are looking at at least a couple of hours of downtime and chaos while system functionality is restored. If you are without backup, that could mean thousands of important files lost. Same with individual users. Whether you have backup or not, a ransomware attack is highly stressful, but in a lot of cases, it can be avoided. And in this article, we will discuss what methods ransomware uses to infect systems.
Most common ransomware spread methods
Phishing (via email, SMS and instant messages)
Why waste time coming up with elaborate methods to infect systems when you could trick users into infecting their computers with ransomware by themselves. Infection via social engineering is probably the most common method used by hackers. And despite many warnings to be careful, users still find themselves falling victim to an attack. Let’s take a look at the most widely used social engineering attacks.
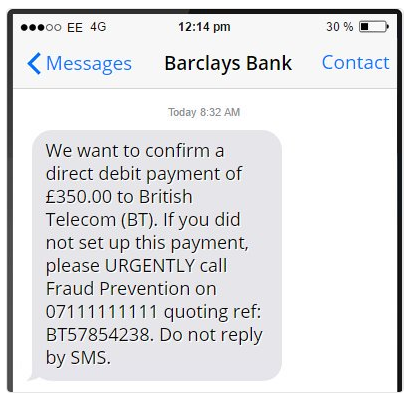
A lot of ransomware infections happen via phishing. And the consequences of falling for a phishing attempt are not just ransomware, users can get their login details stolen, which could lead to serious data breach incidents. If you are wondering what phishing is, it is a technique that involves a legitimate-looking bogus email/message and you opening an attachment/clicking on a link in it. In the case of ransomware, cyber crooks attach an infected file to an email, send it out to hundreds, even thousands of people, and wait for someone to open it. These kinds of fake emails are pretty easy to notice, unless you are individually targeted by someone and they know a lot about you. You need to be on the look out for grammatical mistakes in the text and the unknown sender prompting you to open the attachment. In order to look more convincing and to pressure the users into opening the attachment, the sender might claim to come from a legitimate company, like Amazon, or the government. If you do indeed use the service or if the government is trying to contact you, your full name will be used. Ransomware-carrying emails use general greetings, such as Dear Customer/Sir or Madam. You should refrain from opening emails from unknown senders, and definitely avoid the spam folder, where most of those malicious emails will end up.
The same could happen via instant messages or SMS. You are sent a weird link, and if you were to press on it, you could be take to a site that will trigger ransomware to download onto your system. Facebook seems to be a favored means of spreading malware, Messenger in particular. The are a number of instances where compromised accounts started sending messages to all contacts, asking them to ‘check out’ a video or a photo, and when users click on the link, they are asked to install an extension, which turns out to be some kind of malware.
Bottom line is, when it comes to emails and instant messages, unless you were expecting the attachment/link or are completely sure it is safe, do not open or click on it. And if you get a link via SMS message from some random number, delete it right away.
Vulnerabilities in systems
Software is not perfect, it often comes with all kinds of vulnerabilities that criminals, or the government, like to take advantage of. Ransomware is notorious for looking for vulnerabilities in computers to enter. The most famous example being the EternalBlue exploit. The exploit, believed to be created by NSA, used a vulnerability in Windows to infect hundreds of thousands of computers with WannaCry ransomware.
The vulnerability was discovered and Microsoft released a patch two months prior to the attack but many did not install the update. Those who did not, allowed WannaCry to enter. Vulnerabilities are constantly discovered by security researchers, and they are constantly patched by vendors, but if users do not allow those updates to install, what is the use. So if you want to avoid ransomware taking advantage of a vulnerability on your computer, make sure to update your software.
Infection via advertisements and redirects
There is a reason why it is not recommended to click on ads when on adult entertainment or illegal streaming websites. Those ads can be easily infected with malware, and if you were to click on it, you might end up with a nasty surprise. A single click on the wrong ad could trigger ransomware downloads. This is also why you need to be careful of adware. While it is not malicious itself, it could be inserting malicious ads in sites you visit, and if you were to click on one, you would be in trouble.
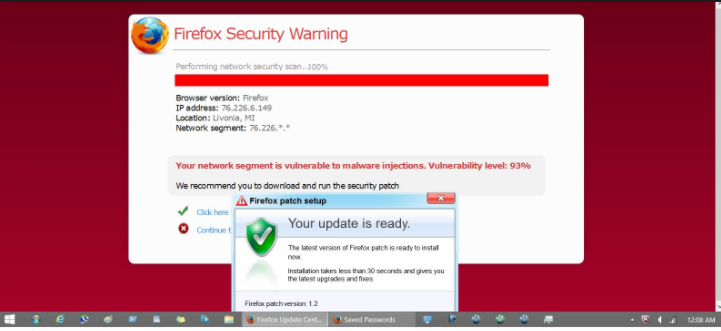
Redirects could also lead to ransomware infections. Again, adult and illegal streaming sites are especially guilty of causing redirects to weird sites, where ransomware download would happen without you even noticing. The downloads may happen immediately upon entering the site, and you would not realize what is going on.
So what can you do?
Do not open suspicious emails or messages, update your software and avoid visiting questionable websites. And backup. Besides being on the lookout for the above mentioned things, have reliable backup. It will save you a lot of trouble.