What is ransomware?
If you are fortunate enough to not have encountered ransomware, know that it’s a type of malware that encrypts files and essentially takes them for hostage by demanding a payment for their decryption. It encrypts all personal files, which then become unopenable unless they are run through a special decryptor program. However, the only people with a decryptor are often the cyber criminals operating the ransomware. If users refuse to pay the ransom, it’s not uncommon for files to remain lost for good. Unless, of course, victims have backup. 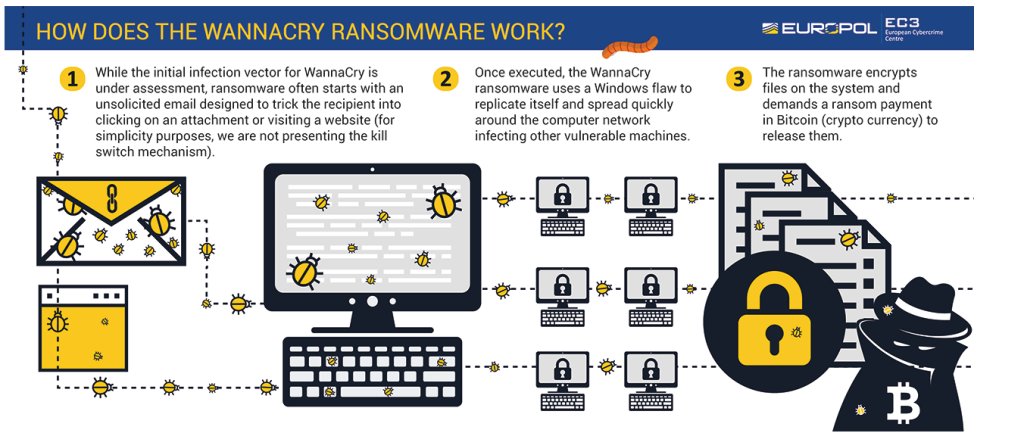
In the last five years, ransomware has become one of the biggest cyber security threats not only for individual users but for businesses and organizations as well. Every year, ransomware causes billions of dollars in damages, and the sum is increasing significantly. In 2020 alone, ransomware caused $20 billion worth of damages. In just two years, damages caused by ransomware doubled.
Over the years, targets have shifted from individual users to small businesses and companies, as well as government facilities. Even the healthcare sector is being targeted. Unlike individual users, larger targets can pay hundreds of thousands of dollars in ransom, which is why they’re such a favored target for cyber criminals, ransomware gangs in particular.
If you want to familiarize yourself with ransomware, how it spreads, the way it works and how to protect yourself, continue reading as we will explain in more detail.
How does ransomware work
- Infection
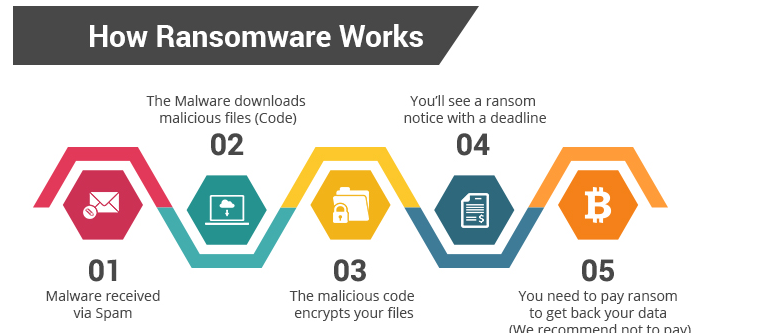
The first step of a ransomware attack is getting into the target system. In the case of individual users, the ransomware usually gets in when users open malicious files, which they obtain from malspam emails, torrent sites, etc. Once the malicious file is opened, the ransomware begin its encryption process.
To infect larger targets such as companies and government agencies, cyber criminals use different tactics, such as misusing the Remote Desktop Protocol, which essentially allows them to get into the target system and initiate the ransomware on it themselves.
- File encryption
When users initiate the ransomware, it will start encrypting files. All ransomware mainly target personal files, including photos, documents and videos. The list of targeted file types is usually very extensive but it depends on the ransomware which files exactly it targets. But overall, the majority of personal files will be encrypted.
Files will become unopenable as soon as they are encrypted. Victims can determine which files have been encrypted by the extension added to encrypted files. Different ransomware add different extensions, which is usually how victims can determine which one they are dealing with if the name is not mentioned in the ransom note.
- The ransom
Once files are done being encrypted, the ransomware will drop a ransom note. Generally, ransomware families use the same notes over and over again, demanding the same sum. For example, the notorious Djvu ransomware family always uses the same identical ransom note every time. The notes usually explain that files have been encrypted and offer a decryptor for a price. The ransom sum is different, depending on which ransomware is responsible.
For individual users, the ransom sum usually ranges from $100 to $2000. However, for businesses and organizations, the demanded sum may be in the hundreds of thousands range, or even millions of dollars.
The thing about paying the ransom is that it does not always guarantee file decryption. While cyber criminals promise to provide a working decryptor, they don’t always make good of those promises, choosing instead to just take the money and not send anything in exchange. Even law enforcement encourage victims to not pay the ransom. However, in the end, whether users pay the ransom is every victims’ decision.
- Blackmail
This is a relatively new practice and usually is employed against bigger targets, such as companies or organizations. Many companies that become victims of ransomware attacks have backups and would be able to restore data and regular operations quite quickly, meaning there would be no need to pay the ransom. However, to try and force targets to pay the ransom, cyber criminals have started essentially blackmailing them by threatening to publicly release data they’ve stolen. How effective this new tactic may be is difficult to tell because not all victims report the attacks. And the majority of those that do, do not pay the ransom.
Ransomware gangs do make good of their promise to release the data, however. One example is the ransomware attack against CD Projekt, developer of popular video games Witcher 3 and Cyberpunk 2077. The company was targeted by a ransomware gang that stole the source codes for said games. The requested ransom sum has not been revealed but CD Projekt refused to pay it. Multiple security analysts later reported that the source code was being auctioned on the dark web for a price starting with $1 million. The code was later shared on social media, and CD Projekt started using DMCA takedown notices to remove it.
Most common ransomware distribution methods
- Email attachments
Malspam campaigns are very effective when it comes to infecting users, especially individual ones. Malicious actors buy thousands of emails addresses from hacker forums and launch malicious spam campaigns using them. It’s not uncommon for the malicious emails to look like they’re official correspondence from some company or government agency. The emails usually have a small amount of text saying that opening the attached file is very important. If users open the attached files, they essentially allow the ransomware to initiate.
- Torrents and other pirating platforms
Forums and torrent websites are often badly regulated, which allows malicious actors to upload malicious content without much difficulty. This is especially common on torrent sites and forums that have software cracks. Users would accidentally download ransomware and other malware, thinking the torrent would contain a movie, TV show, video game or software.
- Exploit kits
It’s pretty common for ransomware gangs to use exploit kits to get into users’ systems. Exploit kits are tools that essentially look for vulnerabilities on a system that they could use to deliver an exploit and download ransomware and other malware. Exploit kits can be encountered in malicious advertising (malvertising) and compromised/malicious websites. The way this works is users are tricked into visiting a malicious or compromised website that has an exploit kit, which then checks for vulnerabilities in software installed on the device. It then takes advantage of that vulnerability to drop a malicious payload, aka malware.
- Remote Desktop Protocol (RDP)
RDP (Remote Desktop Protocol) is a tool that allows users to connect to another computer/server using a network connection. Because of the way it works, it created an opportunity for cyber criminals to use it to distribute their ransomware. It has become one of the most used malware infiltration methods, in particular when targeting big companies and organizations. Dharma ransomware family is one example of a malware family that uses this method.
When a RDP port is open to the Internet, anyone can try to connect to it. And cyber criminals have tools that scan for these open ports. If they find one, they attempt to connect to it using either stolen login credentials or by guessing them. If the password is weak, it can be incredibly easy to guess. Once an attacker successfully logs in, they can access the server/computer and do anything on it, including initiating ransomware.
Ways to protect yourself from ransomware/data loss
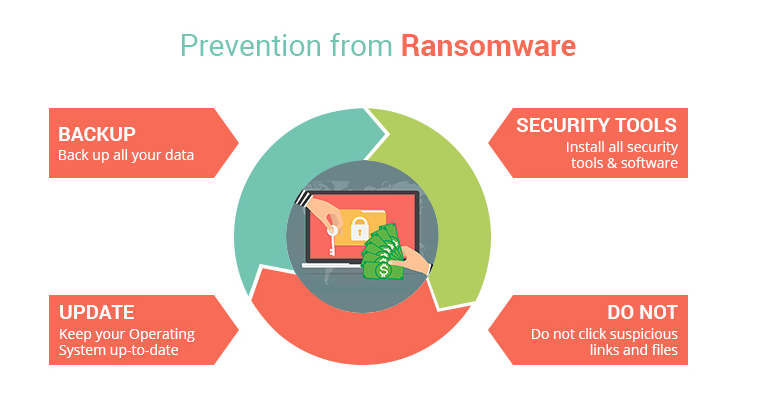
Regularly back up any important files
The best way to prevent serious consequences from a ransomware infection is to regularly back up files, at least the ones you do not want to lose. There are various ways to back up files, and all users will be able to find the most convenient method for them.
Have anti-virus software installed
It will come as no surprise that reliable anti-virus software with ransomware protection is the first line of defence when it comes to malware. To adapt to the rising threat of ransomware, many anti-virus programs now offer some type of protection against ransomware. If you have anti-virus software installed, check whether it has such a feature. If you do not have a security program but are planning on getting one, research the ones that offer the best protection against ransomware.
Install updates regularly
We already mentioned that malware can use vulnerabilities on your device to get in. Whenever vulnerabilities are identified, particularly if they’re serious, an update will be released to patch it. Not installing these updates leaves the system vulnerable. Enabling automatic updates is recommended.
The WannaCry ransomware is a great example that showcases the importance of installing updates regularly. The ransomware exploited a known EternalBlue vulnerability, which was patched by Microsoft 2 months before the attack in a number of updates for all Windows versions that were supported at the time, starting from Windows Vista. More than 300,000 computers that either did not have the patch installed or were running unsupported versions of Windows (e.g Windows XP) were infected all over the world. The WannaCry ransomware demanded a ransom of $300-$600 to be paid in Bitcoin. The majority of victims were companies and organizations that did not have adequate security practices.
Develop good browsing habits
For regular users, avoiding ransomware often means developing better browsing habits. That mainly means not opening unsolicited email attachments, not clicking on ads when browsing high-risk websites, and avoiding pirating (especially via torrents).
- Email attachments
All email attachments should be scanned with anti-virus software or VirusTotal before they are opened. Scanning with VirusTotal may even be better as it would show whether any of the anti-virus programs that are partnered with it detect the file as potentially malicious. In general, you should avoid opening email attachments that come from unknown senders.
Malicious emails carrying malware are usually quite generic, meaning you should be able to identify them as long as you know what to look for. The sender’s email address is often a big giveaway, for example. If the sender has a random email address that’s made up of random letters and numbers, or it just generally does not look professional, you should be very careful about opening the email attachment.
Another easy-to-notice sign of a potentially malicious email is they way you are addressed in the email. For example, if a company whose services you use sends you an email (especially if it’s generic), you will be addressed by your name. For example, if your bank was to send you official correspondence, they will always address you by some form of your name, usually your last name. Inserting the name is done automatically, so there is no chance that you will be addressed by something as generic as “Customer”, “Member”, “User”, etc. So if you ever receive an email that claims you need to urgently open the attachment but you’re addressed using generic terms, take extra precautions if you decide to open the attached file.
Other signs of a malicious email include grammar and spelling mistakes, and awkward phrasing that just seems off.
- Pirating
If you are someone who prefers to get paid content for free via pirating, you are at increased rink of picking up a ransomware infection. Never mind the moral issues of essentially stealing someone’s hard work, pirating is highly discouraged because of how easy it is to encounter malware. This is particularly the case with torrents. A lot of torrent platforms are very badly regulated, of which cyber criminals take full advantage of by uploading malware disguised as torrents. Malware is especially common in torrents for popular movies, TV series, video games and software. When highly popular shows like Game of Thrones air, the majority of episode torrents (especially new episodes) will contain malware.