New year brings us a new type of ransomware called Ransom32. This would not be that noteworthy if not for one thing: Ransom32 is the first of its kind, because it is based on Javascript. The malicious program uses the NW.js platform, which makes it a cross-OS ransomware. So far it has only targeted Windows operating systems, however, that can easily change as the NW.js framework allows it to be written for Mac OS X and Linux. This framework is also responsible for granting the ransomware with more control over the affected system and enabling JavaScript to function in almost the same manner as such programming languages as C++ and Delphi.
Another problem with the malicious application is that it is sold as a service. Ransom32 can be downloaded from an underground TOR website by anyone who has a Bitcoin address. The so-called buyer does not have to pay anything for the executable, but the developers of the ransomware take a 25% cut of all ransom payments that are sent to the buyer’s Bitcoin address. Once a user signs up for the malware, he is presented with an Affiliate Console, which shows statistics of the distribution campaign including Installs, Lockscreens, Paids, and Paid BTC. The console also contains a settings configuration section, where the affiliate can set the amount of Bitcoins to be asked from computer users, choose whether or not the infected computer should be locked, and so on. Once the affiliate downloads the customized version of the parasite, he can start its distribution.
The encryption process starts soon after the threat infiltrates the computer system. The malicious file enters the system in the form of a 22MB RAR file that self-extracts and adds several files to the C:\Users\User\AppData\Roaming\Chrome Browser folder. It also creates a shortcut in the Startup Folder called ChromeService, which allows the ransomware to launch automatically every time the user turns on the PC. The shortcut itself is linked to a chrome.exe file, which is actually a NW.js package containing Javascript code that encrypts the files that are stored on the computer. The types of files that can be affected by the encryption include .jpg, .docx, .pdf, .xls, .pptx, .mp4, .avi, .3gp, .asf, .mpeg, .wma, .dat, and many more.
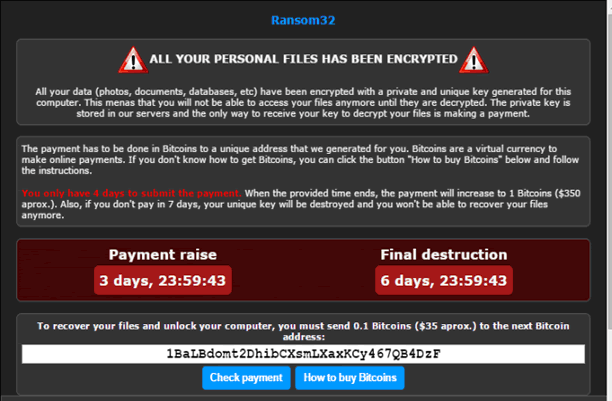
Once the malware is done with the encryption, it displays a message on the desktop. This message informs the user that his data has been encrypted and that in order to get it back, he needs to purchase a private decryption key. The user is given a 4 day deadline before the amount of the payment is increased, and a 7 day deadline before the key is destroyed. The default language of the message is English, however, it may be presented in Spanish as well. The screen also offers the possibility of decrypting one file free of charge to prove that the files can actually be recovered.
Unfortunately, at this moment there are no possible options to decrypt the files in any alternative way, other than restoring them from backup. That is why it is so important to have backup copies of your most relevant data. We also urge you to be more careful online, especially when downloading files onto your PC, and to have a powerful malware prevention and removal tool installed and updated at all times.