2017 has been the year many people realized how serious of a threat ransomware really is. Before that, a lot of people seemed to believe, and some still do, that ransomware is not really something they should be concerned about, but WannaCry, NotPetya and now BadRabbit were a good wake up call for many.
 Chances are, most people did not even know what ransomware was until then. But does that mean people are more cautious and are more likely to implement proper security measures? We would like to hope it means exactly that, but unfortunately, even after three global ransomware attacks, the mindset that it will not happen to me could still be lingering. How many people around you have backed up their files? Have you? How many open every single attachment they get in their email? How many do not update their programs? Cyber crime is a very real threat, and if people do not take it seriously, it may come back to bite them someday. And when it comes to ransomware, people being careless is exactly why ransomware is succeeding.
Chances are, most people did not even know what ransomware was until then. But does that mean people are more cautious and are more likely to implement proper security measures? We would like to hope it means exactly that, but unfortunately, even after three global ransomware attacks, the mindset that it will not happen to me could still be lingering. How many people around you have backed up their files? Have you? How many open every single attachment they get in their email? How many do not update their programs? Cyber crime is a very real threat, and if people do not take it seriously, it may come back to bite them someday. And when it comes to ransomware, people being careless is exactly why ransomware is succeeding.
The evolution of Ransomware
One of the earliest examples of ransomware is the so called AIDS Trojan. Back in 1989, an American evolutionary biologist, Joseph L. Popp, distributed about 20,000 floppy disks containing the AIDS Trojan to AIDS researchers. Initially, nothing happened and computers acted as usual. However, after a system was powered 90 times, a message appeared on the screen, explaining that a ransom of $189 needs to be paid. It was later discovered that it did not encrypt files, merely altered file names, thus full decryption was possible.
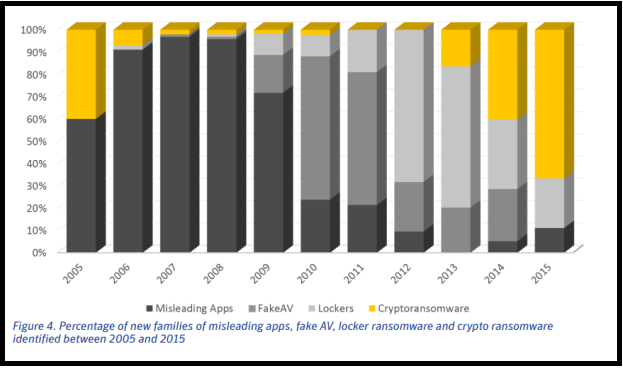
AIDS Trojan is perhaps the earliest known ransomware type of attack, and until mid-2000s, ransomware was not really a relevant threat. According to an article written by Fast Company, back in the old days, cyber criminals wrote their own encryption codes so not everyone could successfully carry out an attack. Nowadays, less-experienced cyber crooks can easily access sophisticated toolkits, made by very skilled hackers, to deploy their own ransomware. Ransomware-as-a-service (RaaS) became a thing, and this has led to an increase in ransomware numbers.
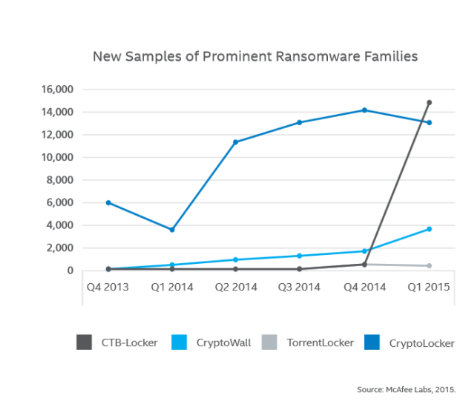
Then, in 2013, CryptoLocker happened. A botnet was used to spread the ransomware to around 250,000 system, and while the botnet was eventually taken down, by that point, the creators of CryptoLocker managed to make more than $3 million from victim payments.
After that, more and more ransomware variants started appearing, including Scatter, CTB-Locker and TeslaCrypt, which dominated in 2015-2016. Then, the infamous Locky ransomware made itself known, hospitals became leading targets, first Apple OS X ransomware emerged, and by the end of 2016, ransomware made crooks a whopping $1 billion.
2017 saw three global ransomware attacks. First came WannaCry. It used a rumored leaked NSA exploit to infect hundreds of thousands computers all over the world but failed to make a huge profit. Reportedly, the creators of WannaCry made around $130,000. Fast forward a month, ransomware is in the spotlight again with NotPetya wreaking havoc. But again, it failed to make creators a lot of money. The recent BadRabbit ransomware attack has not made such an impact, and it is still too early to say how much money the hackers made, but one thing is becoming clear, ransomware is showing no signs of becoming a thing of the past.
Cure for Ransomware?
So if ransomware is not going away, how do we protect ourselves from it? Prevention measures can go a long way when it comes to ransomware, and something as simple as an update can save you a lot of trouble. And prevention is what individual users and businesses alike should focus on. Because if you manage to prevent one infection in a chain, you may break the chain and possibly stop ransomware from spreading. Here are a couple of ways you can help stop ransomware:
– Software updates
Certain ransomware, like WannaCry and NotPetya, can infect via a vulnerability in software or the system. Those vulnerabilities are constantly discovered by researchers and patched by software vendors, but the problem is that users sometimes do not implement those patches. Updates are released for a reason, and if Windows is recommending an important update, you should install it.
– Educating yourself about cybersecurity
If you learn how to differentiate between malicious and safe emails, you could avoid opening an infected email attachment and thus infecting your computer with ransomware. Malicious emails are not difficult to notice, unless they are targeting you specifically. In both cases, it is possible to check whether the attachment is malicious, you just need to be more careful. Educate yourself about cyber security and spread the knowledge.
– Backup
While not exactly a preventive measure, it can still help stop ransomware in the long run. When ransomware strikes, rarely can users decrypt files, whether they choose to pay the ransom or to wait for malware researchers to release a free decryptor. If you have backup, you do not need to worry about loosing files, thus you would not pay the ransom. The less people pay the ransom, the less profitable ransomware will become, which would eventually make it not worth the hassle. So if you do not already have it, invest in reliable backup right now.
– Anti-malware
Anti-malware is not perfect. It is not always going to pick up on all threats but it is still a useful tool to have. So while you should not blindly trust anti-malware to prevent ransomware attacks and not be careful yourself, security programs should still be employed.
We would also like to note that real-time protection against ransomware is currently in development for WiperSoft, and the feature should roll out by the end of the year.
– Controlled folder access
This long-awaited and recently released Windows feature basically locks your files and prevents changes from being made to them. This feature was made available with the Windows 10 Fall Creators Update, but is not enabled by default. We would recommend enabling it because it could prevent ransomware from encrypting your files.
Ransomware has been around for a while now with many notable infections, and it is not showing signs of stopping. The best we can do right now is try to protect ourselves, which, in the long run, could make ransomware a less profitable business. We are probably a long way from ransomware not being a threat anymore, and the unfortunate reality is, even if there ever is such a thing as a cure for ransomware, a new type of malware will just take its place.