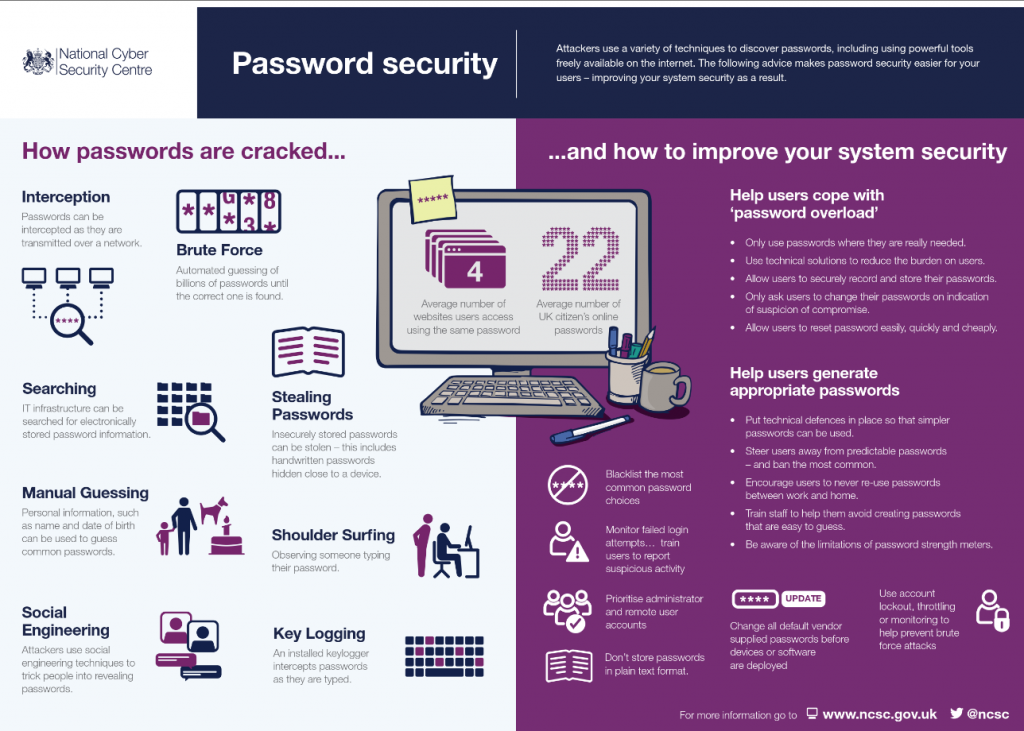
Passwords are a major headache for all of us. We are always advised to never reuse passwords, and include various combinations of lower and uppercase letters, numbers and symbols. Sure, it can sometimes be difficult to come up with one but those rules are there for a reason.
 source: https://www.ncsc.gov.uk/guidance/password-guidance-simplifying-your-approach
source: https://www.ncsc.gov.uk/guidance/password-guidance-simplifying-your-approach
The more complex the password is, the more difficult it is to guess it. Unfortunately, quite a lot of users still stick to the most basic passwords, whether because they cannot be bothered to make more complex ones or because they do not think they will ever have their account stolen. In order to help users when they do not want to help themselves, cyber security specialists are advising that organizations create password blacklists that would prevent users from using the most common, already exposed, passwords. But what passwords should be included?
A list of 320 million passwords already seen in a breach released
An Australian web security expert, Troy Hunt, released a collection of 320 million unique hashed passwords that have appeared in past data breaches. With this release he aims to help fight against cyber crooks who go through known usernames and passwords to find a fit that would allow them to gain access to an account. He is the creator of the service Have I Been Pwned where users can check whether their email address or username has appeared in a data leak. With the release of the collection of passwords, he also introduced a new service Pwned Passwords. This service allows users to check whether their password has appeared in a data leak before, and whether it now has a higher chance of getting guessed.
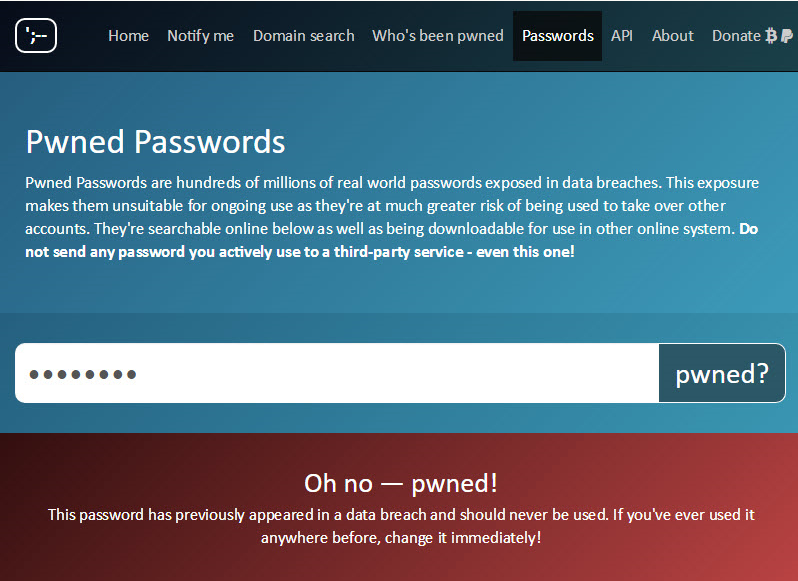
When the 320 million hashed passwords were released, CynoSure Prime managed to crack the passwords and analyze the information acquired. According to them, the longest password was 400 characters, and the shortest was merely 3. The data also reveals that 26% of passwords were only lower case, and only a small 2% of passwords were a mix of upper and lowercase letters, numbers and symbols.
Creating a blacklist of passwords
The above mentioned services are great but let’s face it, not many users are going to go there and check whether their created password has been pwned before. So organizations need to provide similar services when someone is creating an account with them. And in addition to blocking passwords that contain sequences of digits and dictionary words, it is suggested to include passwords that have appeared in a data breach before. However 320 million passwords being blocked would cause a lot of trouble.
“A block list of 320-something million passwords would IMHO be madness in almost any situation,” security expert Per Thorsheim tells Information Security Media Group (ISMG) in their article.
“While blacklisting 320m leaked passwords might sound like a good idea to further improve password security, it can have unforeseeable consequences on usability (i.e, the level of user frustration),” CynoSure agrees.
Blacklist that would work
So how does one create a blacklist that does not frustrate users but prevents them from using the most common passwords?
“A blacklist of the top 1,000 to 10,000. More than that won’t add much extra security, but may severely impact usability and annoy people with repeated messages of ‘password not allowed’,” Thorsheim says to ISMG.
Hunt also suggests that it would be a good idea to block only the very top passwords that commonly appear in leaks, and in addition, warn users about the other ones. That way, users will not get frustrated because 320 million passwords are blocked, and those who care about their cyber security will be encouraged to create stronger passwords.
 source:
source: