DUCKTAIL malware is a malicious infection that aims to steal Facebook Business accounts. The malware is mostly used in targeted attacks, with attackers targeting high-profile Facebook pages.
The malware has been active for several years now and mainly targets high-profile Facebook Business pages. The main goal of this malware is to give the operators access to targeted Facebook Business pages. Thus, users who have full control over Business pages are targeted. If attackers are successful, they can hijack Facebook Business pages to use for their malicious purposes.
When the targetted user initiates the malware on their device, DUCKTAIL malware begins by checking whether Google Chrome, Mozilla Firefox, Microsoft Edge, or Brave are installed. The malware looks for specific cookies that contain data that would allow it access to the target’s Facebook account. It also searches for other sensitive data.
DUCKTAIL malware checks whether two-factor authentication is enabled on the target’s Facebook account. If it is, the malware attempts to steal recovery codes that would allow it to bypass the two-factor authentication. If the malware is successful in stealing the necessary information, it can hijack the Facebook account. To prevent the target from regaining access to the account, login information is changed. The malware can then steal data from the Facebook Business account. The information it’s after includes linked emails, names, connected account numbers, ad spending, account permission, client data, etc.
Compromised accounts can be quite difficult to get back because the malware changes all the information. To make it more difficult for accounts to get hijacked, enabling two-factor authentication is highly recommended.
How is DUCKTAIL malware distributed?
DUCKTAIL malware distribution depends on who the target is as infections are tailor-made. However, phishing techniques and social engineering are used to trick users into initiating infections.
According to researchers, DUCKTAIL malware has been found on platforms like Linkedin, Dropbox, MediaFire, and iCloud. Users may be contacted through platforms like Linkedin and Facebook and sent files that, if opened, would result in an infection.
Furthermore, DUCKTAIL malware is distributed via email, with malicious files attached to tailor-made emails. When cybercriminals target specific people/companies, their malicious emails often look very convincing, with specific information mentioned to give the emails credibility. Users managing social media pages should be trained to identify potentially malicious emails, and security measures should be put in place to prevent users from opening malicious files. While targeted social engineering attacks are more sophisticated, they are not impossible to recognize. If users know what to look for, they should be able to recognize malicious emails.
DUCKTAIL malware removal
These types of infections are quite complex, which is why it’s always recommended to use reputable security programs. Many anti-malware programs detect and remove DUCKTAIL malware. Manual DUCKTAIL malware could lead to additional issues.
If the DUCKTAIL malware is detected on a computer, it’s essential that the user changes their Facebook password immediately after malware removal to prevent unauthorized access. 2FA should also be enabled to prevent easy access.
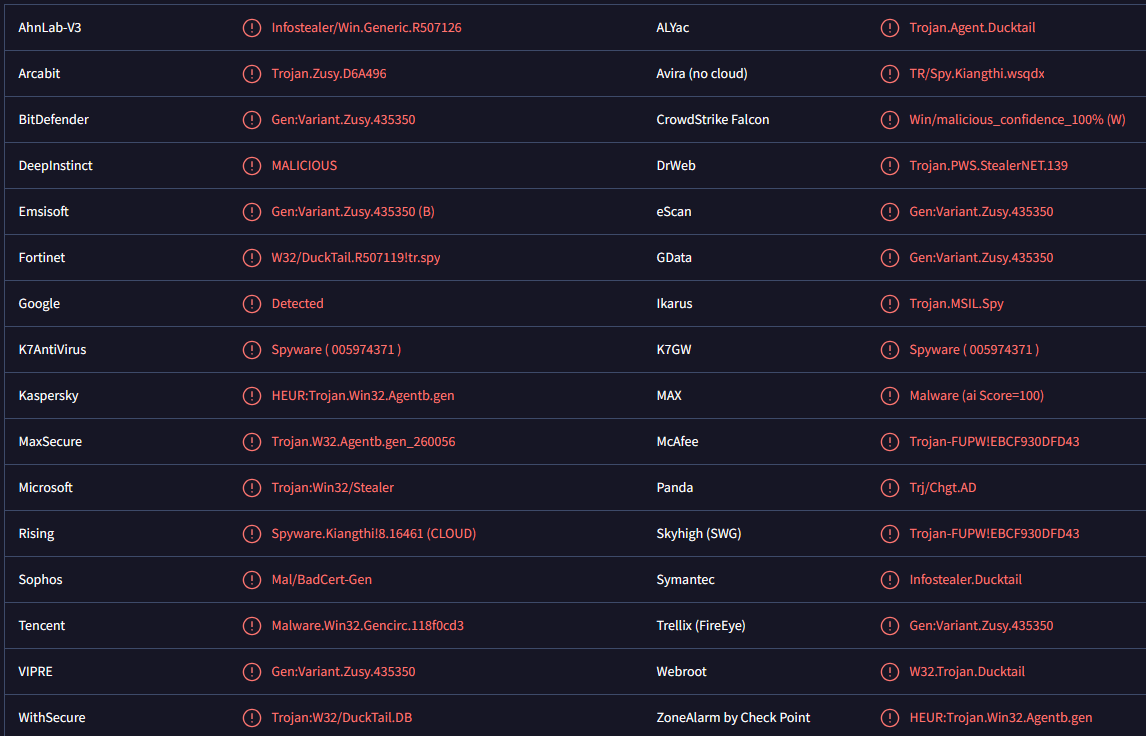
DUCKTAIL malware is detected as:
- Gen:Variant.Zusy.435350 by BitDefender
- HEUR:Trojan.Win32.Agentb.gen by Kaspersky
- Trojan:Win32/Stealer by Microsoft
- Trojan-FUPW!EBCF930DFD43 by McAfee
Site Disclaimer
2-remove-virus.com is not sponsored, owned, affiliated, or linked to malware developers or distributors that are referenced in this article. The article does not promote or endorse any type of malware. We aim at providing useful information that will help computer users to detect and eliminate the unwanted malicious programs from their computers. This can be done manually by following the instructions presented in the article or automatically by implementing the suggested anti-malware tools.
The article is only meant to be used for educational purposes. If you follow the instructions given in the article, you agree to be contracted by the disclaimer. We do not guarantee that the artcile will present you with a solution that removes the malign threats completely. Malware changes constantly, which is why, in some cases, it may be difficult to clean the computer fully by using only the manual removal instructions.