Emails are one of the most effective ways of distributing malware. Cyber security education, while now needed more than ever, is slow moving, meaning many people are still vulnerable to this form of attack. Businesses and organizations are now better at providing cybersecurity training to employees, but cyber attacks are still very common, and often preventable. Individual users in particular are susceptible to cyber attacks and fall for malware distribution tactics much easier, as they are often unaware that even something as simple as opening an email attachment could result in a serious malware infection. 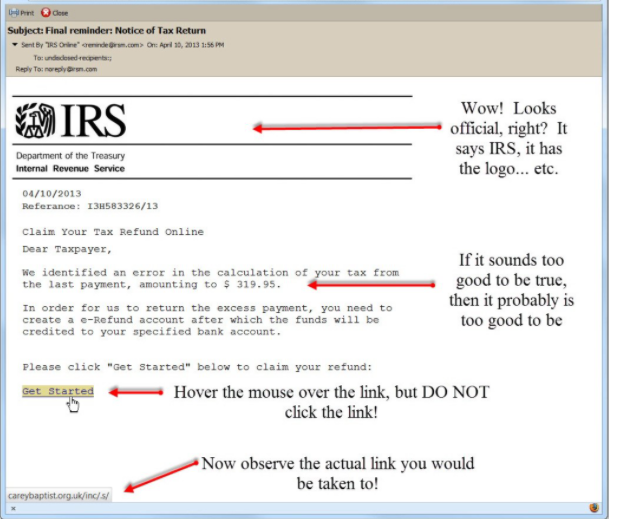
There are likely users who believe that malware and cyber attacks are not going to happen to them because why would they be targeted in particular. But that’s the thing, a lot of cyber attacks are not targeted. Malicious actors launch massive campaigns that distribute malware and target everyone whose information they can get their hands on. So it is essential that even those who do not think they can become victims at least try to understand how malware is distributed, in hopes that the information will be of some help in the future.
Thus, today’s topic is emails, or more specifically, how they are used to distribute malware and how to detect a potentially malicious one.
Emails distributing malware
Using emails to distribute malware is a very popular method because it usually requires very little effort and skill. All malicious actors have to do is compose a semi-legitimate looking email, add a malicious attachment and send it off to thousands of users whose email addresses they bought from hacker forums. If someone opens the attached file, their computers become infected and the malware can start whatever it was created to do.
A common tactic used by malicious actors is to theme malicious emails. A perfect example of this is the COVID-19 themed malicious emails. In the beginning of the pandemic, cyber criminals disguised the malicious email attachments as information about the coronavirus, and once vaccines became available, as registration forms for vaccination. The usual malicious emails are commonly disguised to look like order confirmation emails from Amazon and similar companies, delivery notices from FedEx and other delivery services, as well as tax forms from the government and money-related emails from banks. Most malspam emails are money-related because that’s a topic many users react the strongest and quickest to.
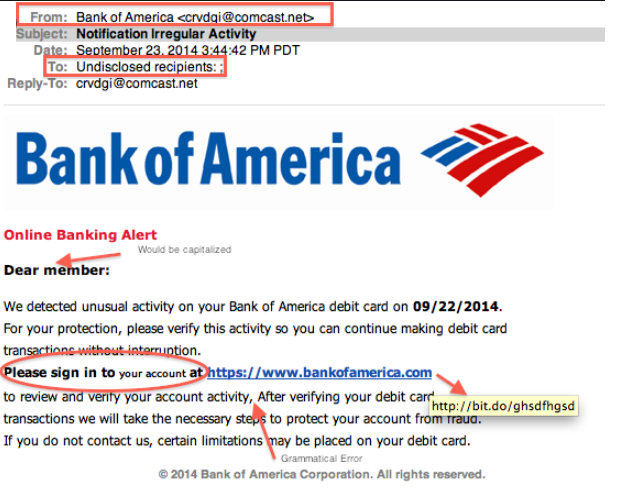
While most malicious emails will be very low-effort, some may look convincing enough to trick some users. Be aware that email addresses, particularly when it’s a targeted attack, may look legitimate. For example, a malicious email disguised to look like it came from Amazon may be sent from an email address that looks like this – amazon@amazon-sales.com. For an unsuspecting user, this may seem like a legitimate email address that Amazon uses, but upon further research, it becomes clear that it’s a malicious address and does not actually belong to Amazon. A good way to determine whether an email address is legitimate is to use a search engine to look into it. If results don’t show that the email address is one that’s used by the company from which the email appears to come from, be very careful about opening the attachment or clicking on a link.
- How do cyber criminals obtain email addresses to launch these malspam campaigns.
If you are among those who receive a lot of spam and malicious emails, your email address has likely been leaked or been part of a data breach. Malicious actors buy the email addresses and other personal information in bulk from various hacking forums, where they end up on after a data breach. Since just about any company can become a victim of a cyber attack, whether your email address falls into the hands of cyber criminals is not something you can control. You can check whether your email has indeed been part of a data breach on haveibeenpwned.
Phishing emails
It’s important to understand that emails can be carrying all kinds of malware, including key-loggers, trojans and file-encrypting ransomware. They’re also not always intended to infect a computer with something, some emails may be trying to phish information, such as login credentials. These emails are as much dangerous as the ones distributing malware, as giving away your personal information to malicious actors can have serious consequences.
- Common phishing email themes.
Depending on what the cyber crooks operating the scam are after, the emails may have a particular theme. For example, if they’re after your Google login credentials, they may send you an email saying someone shared a Google Drive document with you. If you click on the link, you will be taken to a phishing site that’s made to strongly resemble the Google login page and asked to log in to your Google account. The moment you type in the login credentials, you’re essentially giving them away to cyber crooks.
If scammers are after your payment card information, they would send you phishing emails that would require you to type in your card number, expiration date and the CVV. For example, you may receive an email asking to update your payment card information for Netflix. If you do use the streaming service, such an email would not be out of the ordinary, as the company does send emails when problems occur. If you click on the link, you would be taken to a fake Netflix website and asked to type in your login credentials, as well as your payment card information. If you type it in, the cyber crooks will get your payment card details and your Netflix login credentials.
Phishing emails that are after social media accounts like Facebook and Instagram will have similar themes to the above mentioned. You may receive an email saying there was a problem with your account and that you need to click on the provided link to login. Or that you have new messages waiting for you, reading which would require you to click on the link and log in.
How to avoid opening a malicious email
- Scan all email attachments.
We always recommend scanning unsolicited email attachments with anti-virus software or VirusTotal before opening them. This will ensure that you will not be opening some kind of malicious file.
- Pay attention to details.
There are certain signs that point to an email being potentially malicious, and becoming familiar with those signs can help you identify them in the future. One of the most obvious and most noticeable signs is grammar and spelling mistakes. Since malicious emails are often disguised to look like legitimate correspondence from companies and organizations, grammar and spelling mistakes are a dead giveaway. Correspondence from legitimate/official senders will not contain grammar mistakes as they would make the company look unprofessional.
A less noticeable but equally telling signs is the sender’s email address. It’s something you can always use Google to look into. If the email address looks completely random and is made of nonsense combinations of numbers and letters, you are likely dealing with malspam. Even when an email address looks legitimate, always check whether it actually belongs to whomever the senders claims to be. Let’s take the above mentioned fake Amazon email address as an example. amazon@amazon-sales.com may look legitimate at first sight, at least legitimate enough for users to not question it further if the email contents do not raise suspicion. However, if you did a search of the email address with a reliable search engine, there would be no records of the email address ever being used by Amazon to contact customers.
One last thing we ‘d like to mention is that you need to pay attention to how an email addresses you. Whether an email uses generic terms like “Customer”, “Member”, “User”, etc., or does it address you by name. If a company whose services you use sends you an email, they will always address you by name (or the name you have given them when registering). For example, if Netflix sends an email about there being an issue with your account, they will address you by the name of the main profile. If Amazon emails you about your order, they will always address you by the name you used to register. Since most malspam campaigns are random, they will not know your name, thus will not include it. So whenever you are addressed by generic terms, be cautious as you could be dealing with malspam.
- Double-check links in emails before clicking on them.
When you receive an email that asks you to click on a link (particularly if you are then asked to log in), do not immediately do that as it could be a phishing email. Hover over the link with your mouse, and the site’s URL should appear. If the address looks strange, do not click on it. In general, clicking on links in emails is not recommended. If you are asked to log in by an email, always do so manually instead of clicking on a link.
If you do click on a link in an email and are taken to a site that asks you to login, make sure that the site is legitimate. Keep in mind that cyber criminals will try to imitate legitimate sites, so the best way to tell whether it’s legitimate is to check the URL. If a site that looks like a Google login page asks you to log in but the site’s URL does not start with accounts.google.com, it’s not actually a Google website.
Conclusion
Cyber crime is becoming more common and increasingly sophisticated, but for the majority of individual users, having at least minimal knowledge about how malware is distributed can go a long way to prevent an infection. Emails is still a favoured method of distributing malware or phishing for login credentials/personal information, so becoming familiar with the patterns is important. However, in some cases, even when very familiar with malware distribution tactics, it’s difficult to avoid an infection. Thus, it’s very important to have adequate protection installed, such as an anti-virus program.