The notorious TeaBot trojan is back on the Google Play store after managing to bypass Google’s security measures. TeaBot is a well-known trojan that can intercept SMS messages and login credentials, allowing malware operators to access/steal email, social media, and even banking accounts. The trojan itself isn’t anything unusual as all its features are pretty standard. What makes TeaBot stand out is its distribution methods. Instead of spreading via the usual methods like emails, text messages, malicious websites, etc., TeaBot is known to spread using dropper apps. These apps are made to appear legitimate only to deliver a malicious payload once on a device.
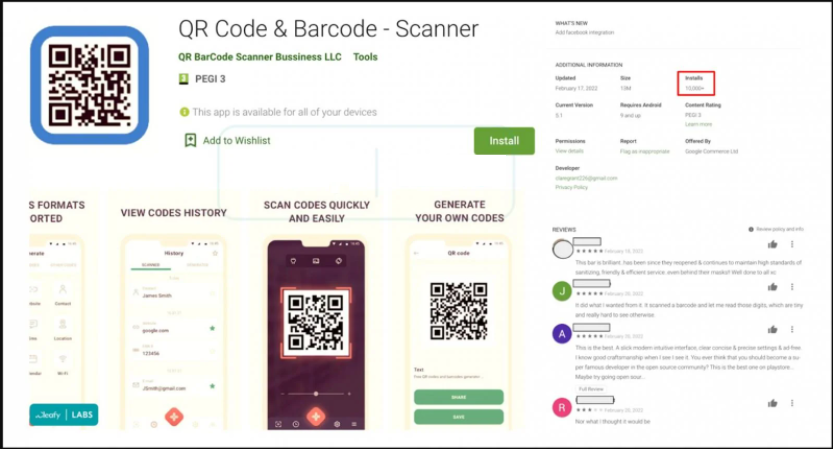
Dropper apps like TeaBot are usually disguised as utility apps like PDF readers, flashlights, QR code scanners, etc. Users who download such tools are usually in a hurry and do not take the time to look into reviews. Furthermore, app stores like Google Play are generally considered to be safe places to get apps from so users let their guard down. But, unfortunately, some malicious actors are able to bypass all security measures and get their malware apps listed on app stores. This time, TeaBot trojan was spotted disguised as a QR Code & Barcode scanner app and was able to infect more than 10,000 devices. Interestingly enough, the malicious app actually does deliver the promised features. This allows the trojan to stay installed for a long time because users will not try to get rid of it since it works as promised.
The Google Play store has numerous security measures in place which help prevent malicious apps from being listed on the app store. Those security measures include regular scans for any kind of malicious behavior by apps on the store. However, once in a while, a dropper app manages to get listen on Google Play. The thing about TeaBot dropper apps is that they aren’t outright malicious. There’s nothing to trigger Google Play’s security measures because the malicious payload is delivered only after the app is already on the device. When users download the app, they are prompted to download a software update, aka the malicious payload. The trojan then attempts to get Accessibility Services permissions. Users have to manually give the app permission. If they were to read the permissions list, it should cause suspicion but many users rush through these steps. Once the payload is dropped and executed, the malicious actors behind it could get remote access to the victim’s device. Ultimately, the malicious app is after sensitive information, mostly login credentials and two-factor authentication tools. Acquiring this kind of information would allow malware operators to access various sensitive accounts without users even noticing until it may be too late.
Generally, it’s still recommended to only download apps from official app stores. However, because some apps are able to bypass security, users should still be extra cautious, particularly when downloading utility apps. It’s a good idea to check the developer, read the reviews, review the permissions, etc. If a PDF reader is requesting access to SMS, there’s something not right about it.