“I am a professional hacker and have successfully managed to hack your operating system” is a generic sextortion scam. It threatens to release a nonexistent private video of you watching pornography unless you agree to pay the requested sum of money. If you receive this sextortion email, you can just remove it from your inbox. There is no malware on your computer, nor is there a private video of you.
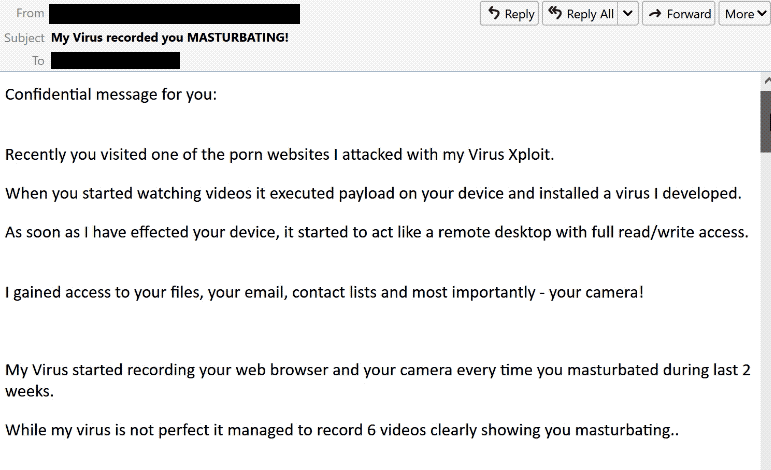
“Your personal data has leaked due to suspected harmful activities” is the subject line of this particular sextortion scam. The email itself is pretty generic and the way it operates is the same as every other sextortion scam we’ve seen before. To catch users’ attention, sextortion emails use eye-catching subject lines, such as the above-mentioned one. The sender, who is actually a scammer, tries to alarm users further by saying that they have infected the users’ computers with malware and have basically taken it over after hacking it.
Then they claim that they were able to turn on the camera and microphone of the infected computer in order to make a video of users watching pornography. By continually using derogatory words, the scammer seeks to humiliate the victim and affect them psychologically. Regardless of whether users have actually watched pornographic content or not, this sort of strategy might nevertheless have an impact on them.
The scammer threatens to post the nonexistent video online and distribute it to all contacts if the victim declines to pay $850 in Bitcoin.
You can just delete this sort of email from your inbox if you get it. You can be sure that there is no malware on your computer operated by this scammer, nor is there a video of you. You certainly do not need to pay the requested sum of money.
Subject: Your personal data has leaked due to suspected harmful activities.
Hi there!
I am a professional hacker and have successfully managed to hack your operating system.
Currently I have gained full access to your account.In addition, I was secretly monitoring all your activities and watching you for several months.
The thing is your computer was infected with harmful spyware due to the fact that you had visited a website with porn content previously. ╭ ᑎ ╮Let me explain to you what that entails. Thanks to Trojan viruses, I can gain complete access to your computer or any other device that you own.
It means that I can see absolutely everything in your screen and switch on the camera as well as microphone at any point of time without your permission.
In addition, I can also access and see your confidential information as well as your emails and chat messages.You may be wondering why your antivirus cannot detect my malicious software.
Let me break it down for you: I am using harmful software that is driver-based,
which refreshes its signatures on 4-hourly basis, hence your antivirus is unable to detect it presence.I have made a video compilation, which shows on the left side the scenes of you happily masturbating,
while on the right side it demonstrates the video you were watching at that moment..ᵔ.ᵔAll I need is just to share this video to all email addresses and messenger contacts of people you are in communication with on your device or PC.
Furthermore, I can also make public all your emails and chat history.I believe you would definitely want to avoid this from happening.
Here is what you need to do – transfer the Bitcoin equivalent of 850 USD to my Bitcoin account
(that is rather a simple process, which you can check out online in case if you don’t know how to do that).Below is my bitcoin account information (Bitcoin wallet):
Once the required amount is transferred to my account, I will proceed with deleting all those videos and disappear from your life once and for all.
Kindly ensure you complete the abovementioned transfer within 50 hours (2 days +).
I will receive a notification right after you open this email, hence the countdown will start.Trust me, I am very careful, calculative and never make mistakes.
If I discover that you shared this message with others, I will straight away proceed with making your private videos public.Good luck!
How did scammers obtain your email address?
Different scammers may operate these sextortion scam campaigns but they always work and look the same. If you have already received one sextortion scam email, you will probably continue to receive them in the future because scammers likely purchased your email address from a hacker forum. Email addresses are frequently leaked by services with poor security. For this reason, it’s not recommended to sign up for services like mobile apps and random websites using your primary email account. When an email address is leaked, it will start appearing in various data dumps that can be found on hacker forums. You can check whether your email address has been leaked on haveibeenpwned.
It’s important to note that some sextortion emails also reveal users’ actual passwords. It is an effective tactic because it convinces people that a virus is present on their computer. Users may believe there is no other way the sender could know their password. But the reality is that the same hacker forums that sell email addresses also sell leaked passwords. Some services have poor security and do not properly secure passwords. If such a service becomes the target of a cyber attack, malicious actors could steal passwords. The stolen information is subsequently sold to other malicious actors on hacker forums.
If you get a sextortion email that contains your password, you need to change it right away. You should be aware that passwords need to be difficult to guess and complex. Ideally, they would be made up of random combinations of capital and lowercase letters, numbers, and symbols. The password for each account has to be unique. If you have trouble remembering your passwords, you should use a password manager.
Site Disclaimer
2-remove-virus.com is not sponsored, owned, affiliated, or linked to malware developers or distributors that are referenced in this article. The article does not promote or endorse any type of malware. We aim at providing useful information that will help computer users to detect and eliminate the unwanted malicious programs from their computers. This can be done manually by following the instructions presented in the article or automatically by implementing the suggested anti-malware tools.
The article is only meant to be used for educational purposes. If you follow the instructions given in the article, you agree to be contracted by the disclaimer. We do not guarantee that the artcile will present you with a solution that removes the malign threats completely. Malware changes constantly, which is why, in some cases, it may be difficult to clean the computer fully by using only the manual removal instructions.