What is Conhost.exe?
Conhost.exe is a process or a file you might find on your computer. Unfortunately, its presence indicates that there is a malicious application installed on your computer. Specialists say that it should be a Trojan miner named Conhost Miner. It is one of those malicious applications that are used to mine cryptocurrency. 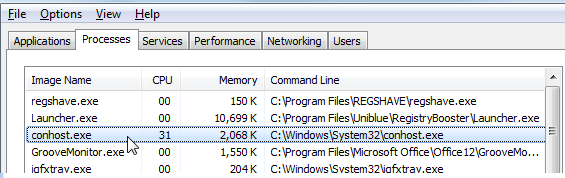
They enter computers without permission, and it is usually hard to spot them because they create a randomly-named folder with files in a random location and perform all their activities only behind the user’s back. Of course, it does not mean that users cannot find out about the entrance of such an infection without scanning their computers with an anti-malware scanner. Talking about Conhost Miner, you can easily find out whether or not it is active on your computer by checking Task Manager. If you can locate Conhost.exe, no doubt you have this threat installed on your computer. Most likely, it has more than one component on your system, so it is not very likely that you will disable this Trojan by implementing the Conhost.exe removal.
What does Conhost.exe do?
Since Conhost.exe is one of the Conhost Miner components, there is no doubt that it is responsible together with other components for its proper functioning. Trojan miners, as has been mentioned in the first paragraph, are used to mine cryptocurrency, and Conhost Miner is no exception, we can assure you. It will use your computer’s CPU and GPU power to perform this activity on your computer. Such threats might be used to mine various cryptocurrencies, but Conhost Miner should primarily focus on mining Monero, according to malware experts. This will not go unnoticed. If you use an older computer, you will notice that it produces more heat and uses more electricity. Also, you might notice that programs run slower or even crash immediately. Finally, your computer might start freezing from time to time. If you do not uninstall Conhost.exe soon, you might notice that it is impossible to use it normally. If you leave malware active on your computer, it might install more threats on your PC without your knowledge too.
Where does Conhost.exe come from?
Conhost.exe is one of the components used by the malicious application called Conhost Miner, so if you can locate it in Task Manager or in a random directory, it must be active on your computer. In this case, you need to implement the Conhost.exe removal as soon as possible. Do not forget to take care of other malicious components too to disable the infection. To prevent infections similar to Conhost Miner from entering your system in the future, use a trustworthy anti-malware scanner.
How do I remove Conhost.exe?
You will delete Conhost.exe normally after killing its process in Task Manager, but it does not mean that you will completely erase malware from your computer by implementing the Conhost.exe removal. Therefore, it would be best to use an anti-malware scanner. It will delete Conhost.exe together with other malicious files within seconds. Of course, you cannot use the first scanner you find to remove Conhost.exe. There are hundreds of untrustworthy scanners that only pretend to be legitimate – they usually wait for users to download them on untrustworthy P2P websites.
Offers
Download Removal Toolto scan for conhost.exeUse our recommended removal tool to scan for conhost.exe. Trial version of provides detection of computer threats like conhost.exe and assists in its removal for FREE. You can delete detected registry entries, files and processes yourself or purchase a full version.
More information about SpyWarrior and Uninstall Instructions. Please review SpyWarrior EULA and Privacy Policy. SpyWarrior scanner is free. If it detects a malware, purchase its full version to remove it.

WiperSoft Review Details WiperSoft (www.wipersoft.com) is a security tool that provides real-time security from potential threats. Nowadays, many users tend to download free software from the Intern ...
Download|more


Is MacKeeper a virus? MacKeeper is not a virus, nor is it a scam. While there are various opinions about the program on the Internet, a lot of the people who so notoriously hate the program have neve ...
Download|more


While the creators of MalwareBytes anti-malware have not been in this business for long time, they make up for it with their enthusiastic approach. Statistic from such websites like CNET shows that th ...
Download|more
Site Disclaimer
2-remove-virus.com is not sponsored, owned, affiliated, or linked to malware developers or distributors that are referenced in this article. The article does not promote or endorse any type of malware. We aim at providing useful information that will help computer users to detect and eliminate the unwanted malicious programs from their computers. This can be done manually by following the instructions presented in the article or automatically by implementing the suggested anti-malware tools.
The article is only meant to be used for educational purposes. If you follow the instructions given in the article, you agree to be contracted by the disclaimer. We do not guarantee that the artcile will present you with a solution that removes the malign threats completely. Malware changes constantly, which is why, in some cases, it may be difficult to clean the computer fully by using only the manual removal instructions.
