What is Torpig trojan
Torpig trojan is a severe threat, classified as a Trojan. If you don’t have a proper security software on your system, you could not realize that a Trojan is present on your system as it operates in the background. Using the Trojan, cyber criminals may get access to your private data, including bank details. The Trojan may be spying on you in the background, and then releasing your bank details to malevolent parties. Symptoms of a Trojan infection include a sluggish system, lagging programs, slow Internet, and just generally weird computer activity. be aware of the threat. Uninstall Torpig trojan as soon as possible, if it indeed is present on your computer.
How does it spread
Crooks generally attach the Trojan to emails, disguise it as some type of update, or implant it in an advertisement. These are the reasons why malware analysts are cautioning users to be vigilant about what emails they open and how they browse the Internet. If you get an email with an attachment, and the sender is not familiar to you, or you weren’t expecting it, don’t right away open it, first make sure it is not malware-ridden. If you are not careful about what attachments you open, don’t be surprised when you end up with something malicious, such as a Trojan or file-encrypting malware. Never acquire anything from dubious pop-ups or web pages and don’t fall for the classic “You need to install this plug-in to view this video”. Make sure you only use safe pages for your downloads. It could also be a good idea to not click on ads when on gambling, pornographic or illegal streaming pages.
How does the Trojan affect your computer
A Trojan will make your OS exposed so that crooks could access it and take your private information. Crooks could install even more severe threats onto your system, without you knowing. If the Trojan is also used to spy on you your personal data could then end up in the hands of hackers. A Trojan isn’t an insignificant infection, so the longer you delay Torpig trojan termination, the more damage it may bring about to your device. We advise that you have an anti-malware operating in the background at all times as it may identify the threat immediately. If you are notified about the infection in time, there should be no damage done to your system. If your device is displaying the symptoms of a contamination, but there is no security utility installed, get one immediately, and use it to remove Torpig trojan.
Torpig trojan uninstallation
We encourage you act quickly, and remove Torpig trojan as quickly as you are able. In order to fully remove Torpig trojan, malware removal utility may be needed. Use the tool to scan your operating system, and if it is located, delete Torpig trojan. Manual Torpig trojan termination isn’t advised because it may be too hard for the unskilled user.
Quick Menu
Step 1. Uninstall Torpig trojan and related programs.
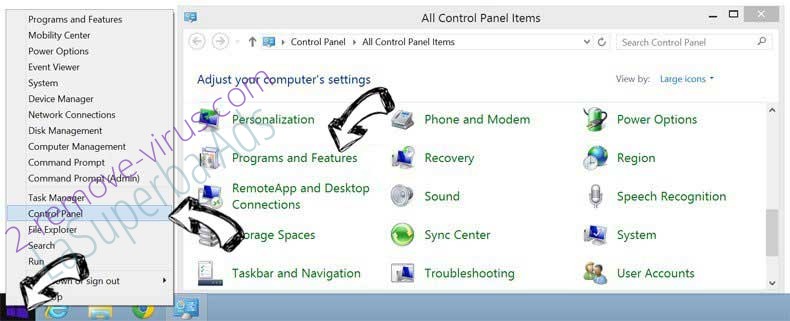
Remove Torpig trojan from Windows 8
Right-click in the lower left corner of the screen. Once Quick Access Menu shows up, select Control Panel choose Programs and Features and select to Uninstall a software.
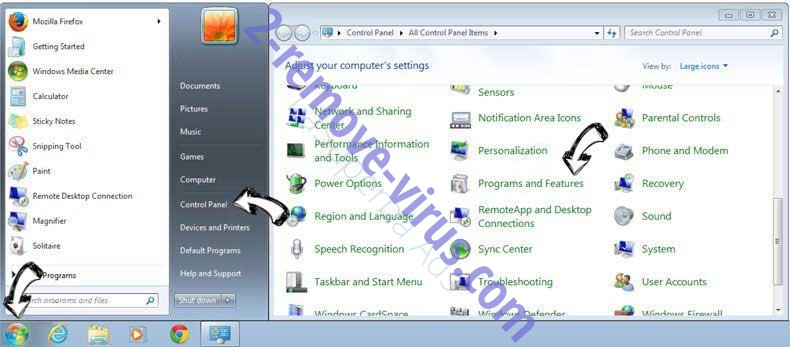
Uninstall Torpig trojan from Windows 7
Click Start → Control Panel → Programs and Features → Uninstall a program.
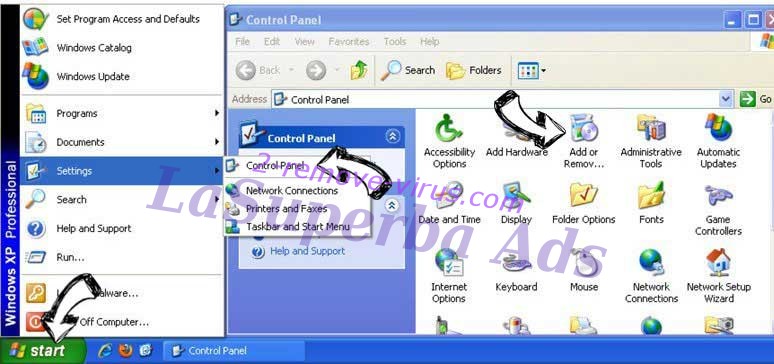
Delete Torpig trojan from Windows XP
Click Start → Settings → Control Panel. Locate and click → Add or Remove Programs.
Remove Torpig trojan from Mac OS X
Click Go button at the top left of the screen and select Applications. Select applications folder and look for Torpig trojan or any other suspicious software. Now right click on every of such entries and select Move to Trash, then right click the Trash icon and select Empty Trash.

Offers
Download Removal Toolto scan for Torpig trojanUse our recommended removal tool to scan for Torpig trojan. Trial version of provides detection of computer threats like Torpig trojan and assists in its removal for FREE. You can delete detected registry entries, files and processes yourself or purchase a full version.
More information about SpyWarrior and Uninstall Instructions. Please review SpyWarrior EULA and Privacy Policy. SpyWarrior scanner is free. If it detects a malware, purchase its full version to remove it.

WiperSoft Review Details WiperSoft (www.wipersoft.com) is a security tool that provides real-time security from potential threats. Nowadays, many users tend to download free software from the Intern ...
Download|more


Is MacKeeper a virus? MacKeeper is not a virus, nor is it a scam. While there are various opinions about the program on the Internet, a lot of the people who so notoriously hate the program have neve ...
Download|more


While the creators of MalwareBytes anti-malware have not been in this business for long time, they make up for it with their enthusiastic approach. Statistic from such websites like CNET shows that th ...
Download|more
Site Disclaimer
2-remove-virus.com is not sponsored, owned, affiliated, or linked to malware developers or distributors that are referenced in this article. The article does not promote or endorse any type of malware. We aim at providing useful information that will help computer users to detect and eliminate the unwanted malicious programs from their computers. This can be done manually by following the instructions presented in the article or automatically by implementing the suggested anti-malware tools.
The article is only meant to be used for educational purposes. If you follow the instructions given in the article, you agree to be contracted by the disclaimer. We do not guarantee that the artcile will present you with a solution that removes the malign threats completely. Malware changes constantly, which is why, in some cases, it may be difficult to clean the computer fully by using only the manual removal instructions.
