What is this message?
Would Like To Use Your Computing Power Scam refers to a pop-up message saying that a website wants to use your computer’s resources to mine for cryptocurrency. If you encounter such a pop-ups, it’s probably because you were visiting a questionable website. It’s unlikely that your computer has been infected with any kind of malware, but it’s recommended to regularly check. And you should also close the window as soon as it appears. 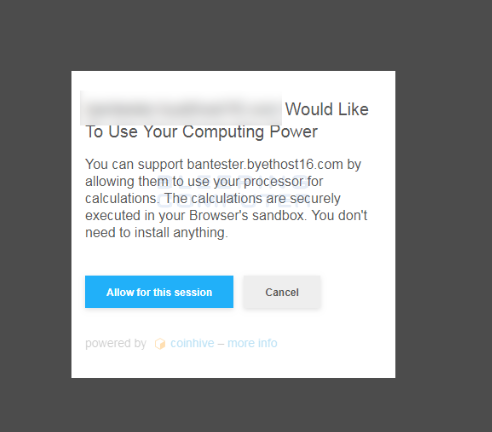
This pop-up is not exactly malicious, although it will definitely have an affect on your computer. Your computer will slow down, your browser will crash or lag, and programs will take ages to load. That is because when the pop-up appeared, a miner was launched and started using your computer to mine. As long as the pop-up is active, or if you pressed “Allow for this session”, this will continue. Since CoinHive appeared, many website owners started using their code to load miners when users enter their websites, and in the majority of cases, users are not informed of this. This pop-up, however, clearly states what it intends to do. Nevertheless, we do not recommend allowing a weird website to use your computer for their own gain. Particularly because your computer will be severely affected. And while it will not do any serious damage, prolonged mining can shorten your CPU’s lifespan.
What does it do exactly?
The so-called in-browser miners aim to use your computer while you are browsing a certain website. As soon as you close the window, the mining should stop. However, during the duration of your stay on the site, your computer will experience severe slowdowns, programs will lag or not respond completely, and you will notice processes in Task Manager using a lot of your computer’s CPU. If a process is using more than 50%, it’s very likely a miner. This is what’s slowing down your computer. While this won’t do serious damage, do keep in mind that your CPU should not run at such high temperatures for a long period of time, otherwise it could be damaged and its lifespan may shorten.
How to remove Would Like To Use Your Computing Power Scam?
All you need to do to delete Would Like To Use Your Computing Power Scam is close your browser. It’s not an actual infection, thus deleting it from the computer is not necessary. However, we do recommend you scan your computer with anti-spyware software to make sure there are not infections present.
Offers
Download Removal Toolto scan for Would Like To Use Your Computing Power ScamUse our recommended removal tool to scan for Would Like To Use Your Computing Power Scam. Trial version of provides detection of computer threats like Would Like To Use Your Computing Power Scam and assists in its removal for FREE. You can delete detected registry entries, files and processes yourself or purchase a full version.
More information about SpyWarrior and Uninstall Instructions. Please review SpyWarrior EULA and Privacy Policy. SpyWarrior scanner is free. If it detects a malware, purchase its full version to remove it.

WiperSoft Review Details WiperSoft (www.wipersoft.com) is a security tool that provides real-time security from potential threats. Nowadays, many users tend to download free software from the Intern ...
Download|more


Is MacKeeper a virus? MacKeeper is not a virus, nor is it a scam. While there are various opinions about the program on the Internet, a lot of the people who so notoriously hate the program have neve ...
Download|more


While the creators of MalwareBytes anti-malware have not been in this business for long time, they make up for it with their enthusiastic approach. Statistic from such websites like CNET shows that th ...
Download|more
Quick Menu
Step 1. Uninstall Would Like To Use Your Computing Power Scam and related programs.
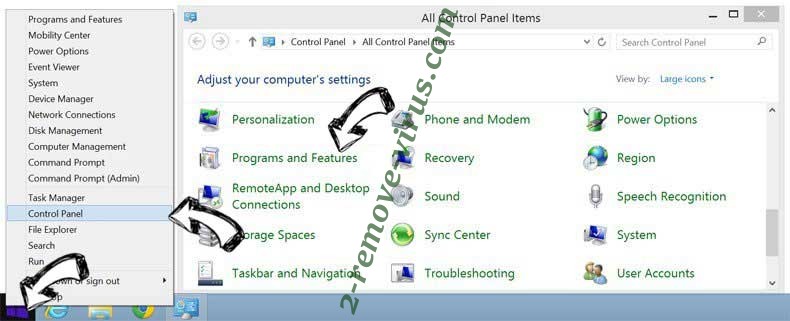
Remove Would Like To Use Your Computing Power Scam from Windows 8
Right-click in the lower left corner of the screen. Once Quick Access Menu shows up, select Control Panel choose Programs and Features and select to Uninstall a software.

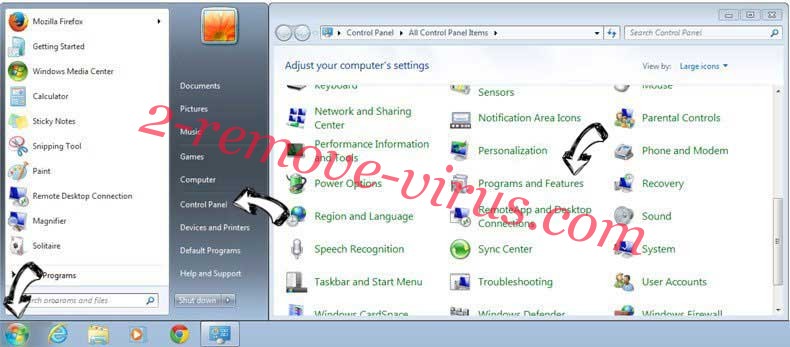
Uninstall Would Like To Use Your Computing Power Scam from Windows 7
Click Start → Control Panel → Programs and Features → Uninstall a program.

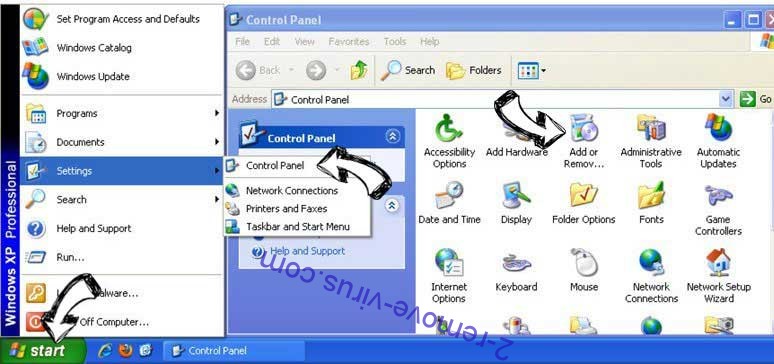
Delete Would Like To Use Your Computing Power Scam from Windows XP
Click Start → Settings → Control Panel. Locate and click → Add or Remove Programs.

Remove Would Like To Use Your Computing Power Scam from Mac OS X
Click Go button at the top left of the screen and select Applications. Select applications folder and look for Would Like To Use Your Computing Power Scam or any other suspicious software. Now right click on every of such entries and select Move to Trash, then right click the Trash icon and select Empty Trash.


Step 2. Delete Would Like To Use Your Computing Power Scam from your browsers
Terminate the unwanted extensions from Internet Explorer
- Tap the Gear icon and go to Manage Add-ons.

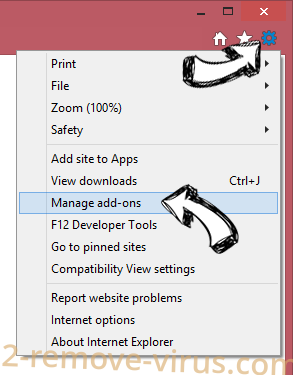
- Pick Toolbars and Extensions and eliminate all suspicious entries (other than Microsoft, Yahoo, Google, Oracle or Adobe)

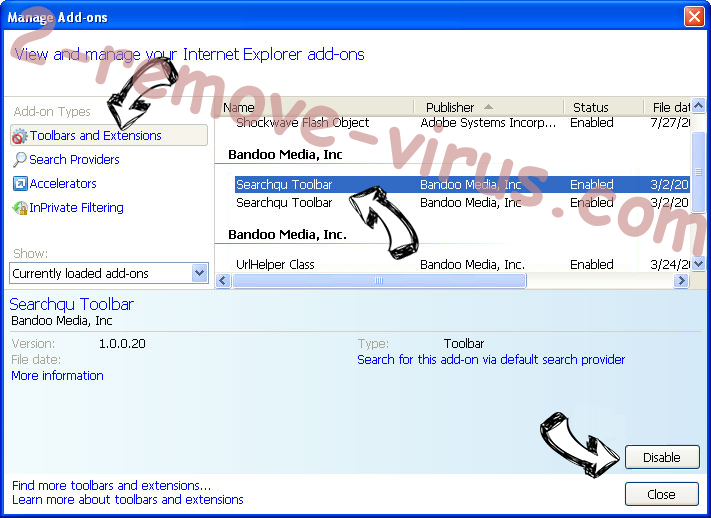
- Leave the window.
Change Internet Explorer homepage if it was changed by virus:
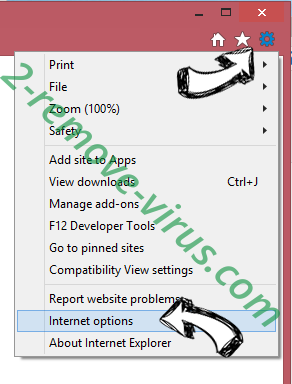
- Tap the gear icon (menu) on the top right corner of your browser and click Internet Options.

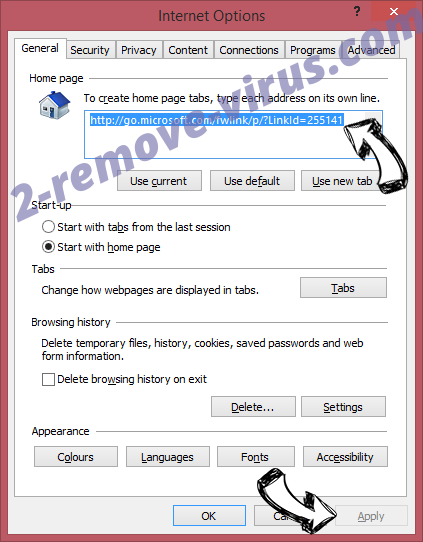
- In General Tab remove malicious URL and enter preferable domain name. Press Apply to save changes.

Reset your browser
- Click the Gear icon and move to Internet Options.

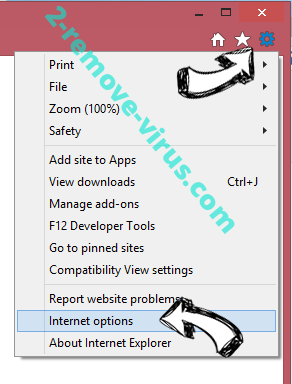
- Open the Advanced tab and press Reset.

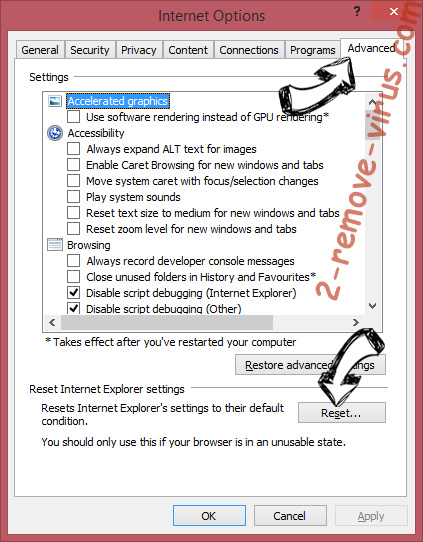
- Choose Delete personal settings and pick Reset one more time.

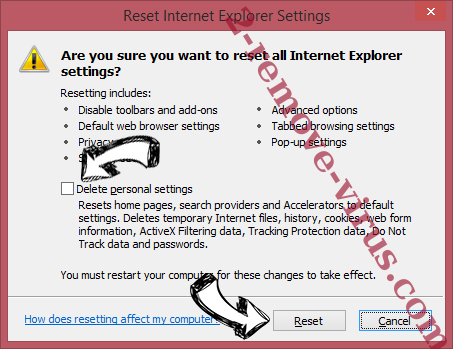
- Tap Close and leave your browser.

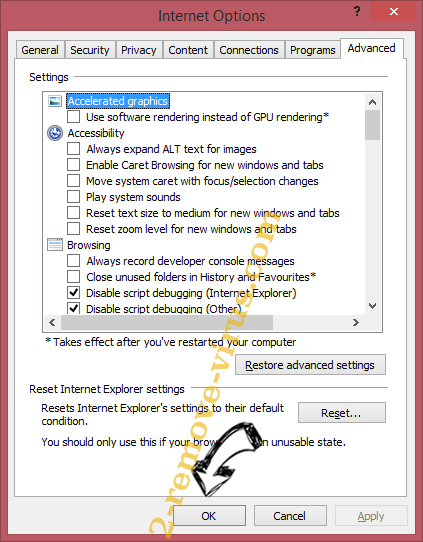
- If you were unable to reset your browsers, employ a reputable anti-malware and scan your entire computer with it.
Erase Would Like To Use Your Computing Power Scam from Google Chrome
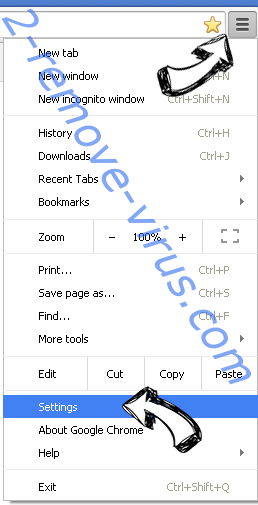
- Access menu (top right corner of the window) and pick Settings.

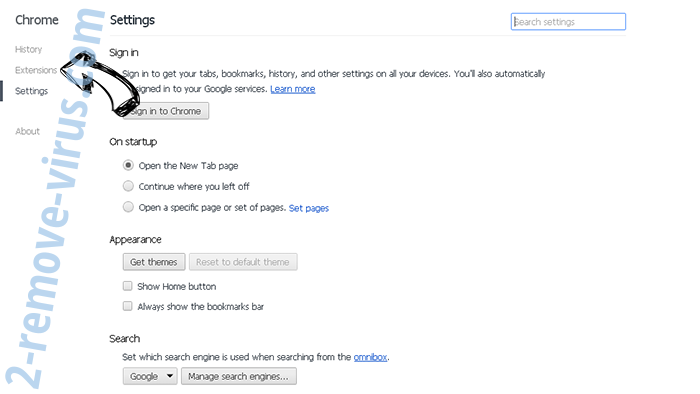
- Choose Extensions.

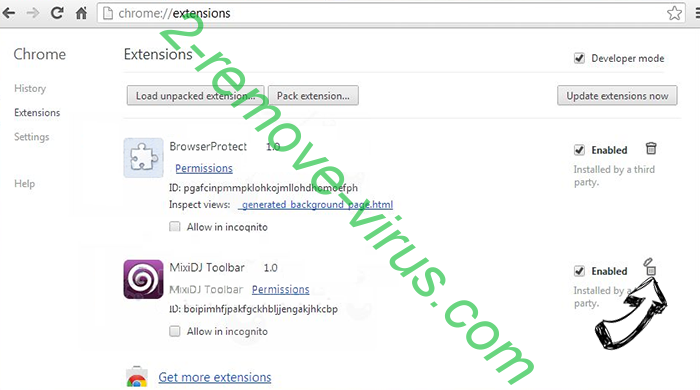
- Eliminate the suspicious extensions from the list by clicking the Trash bin next to them.

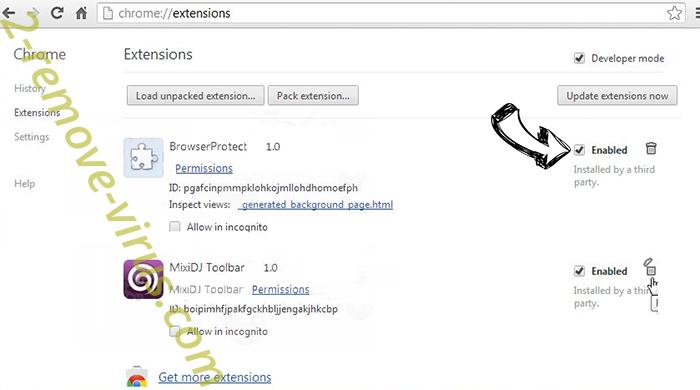
- If you are unsure which extensions to remove, you can disable them temporarily.

Reset Google Chrome homepage and default search engine if it was hijacker by virus
- Press on menu icon and click Settings.

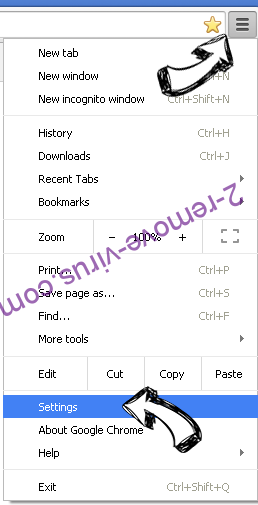
- Look for the “Open a specific page” or “Set Pages” under “On start up” option and click on Set pages.

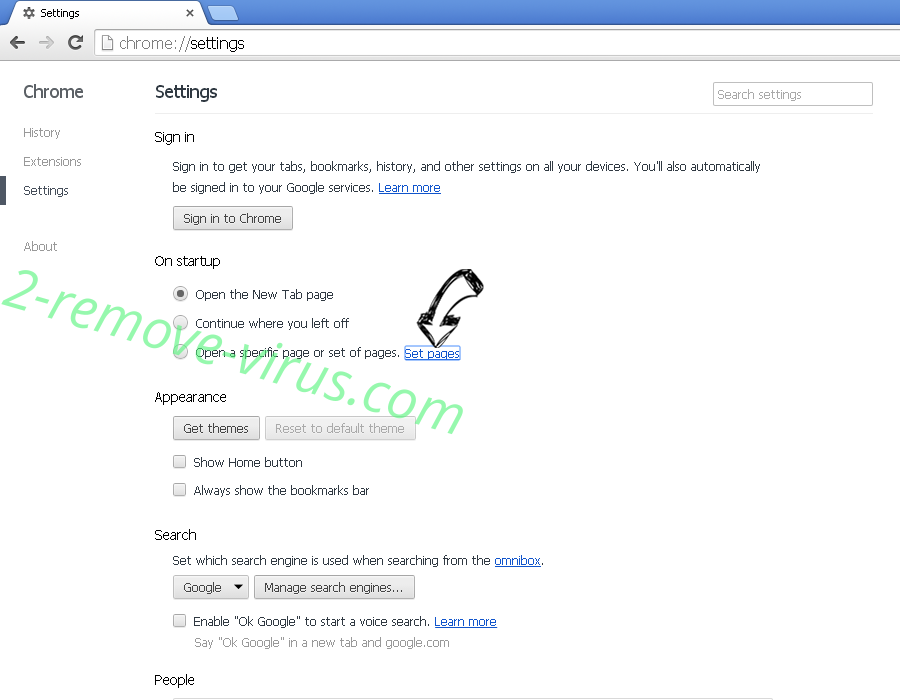
- In another window remove malicious search sites and enter the one that you want to use as your homepage.


- Under the Search section choose Manage Search engines. When in Search Engines..., remove malicious search websites. You should leave only Google or your preferred search name.


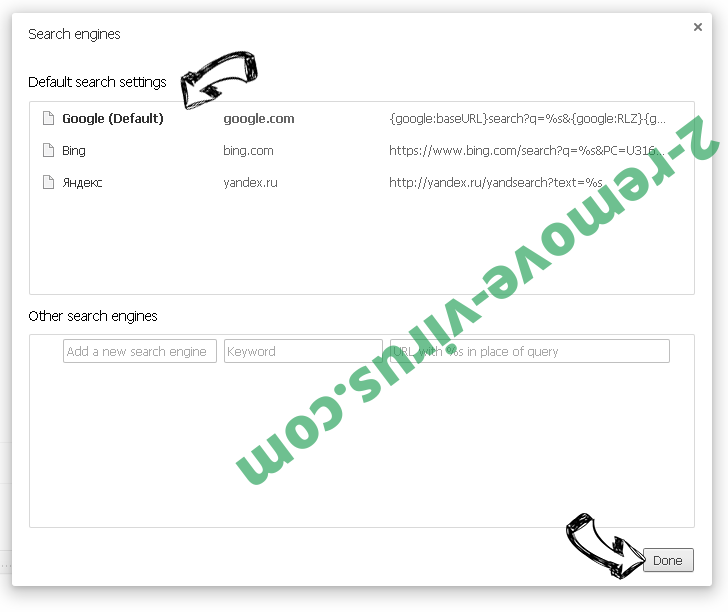
Reset your browser
- If the browser still does not work the way you prefer, you can reset its settings.
- Open menu and navigate to Settings.

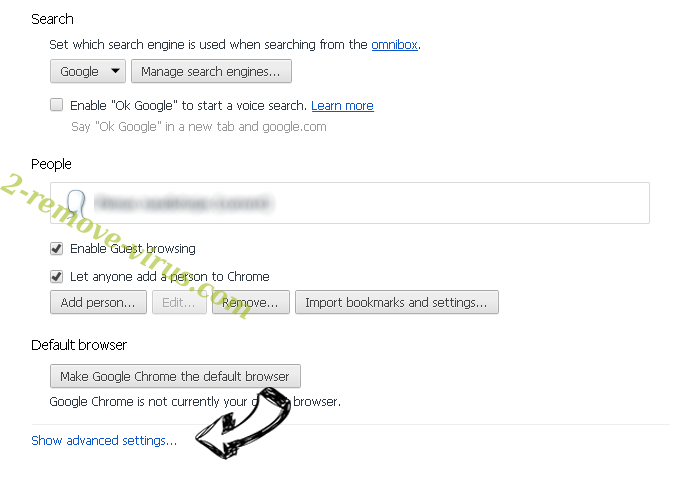
- Press Reset button at the end of the page.

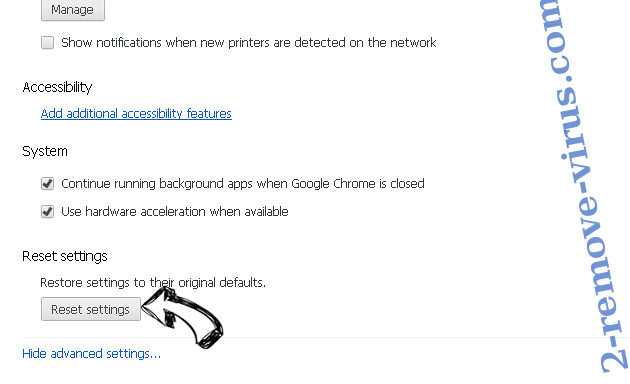
- Tap Reset button one more time in the confirmation box.

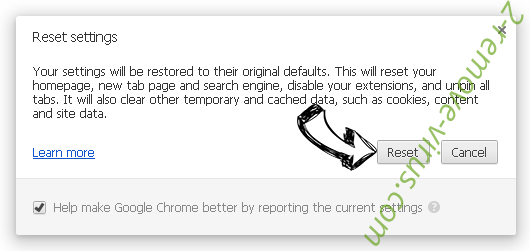
- If you cannot reset the settings, purchase a legitimate anti-malware and scan your PC.
Remove Would Like To Use Your Computing Power Scam from Mozilla Firefox
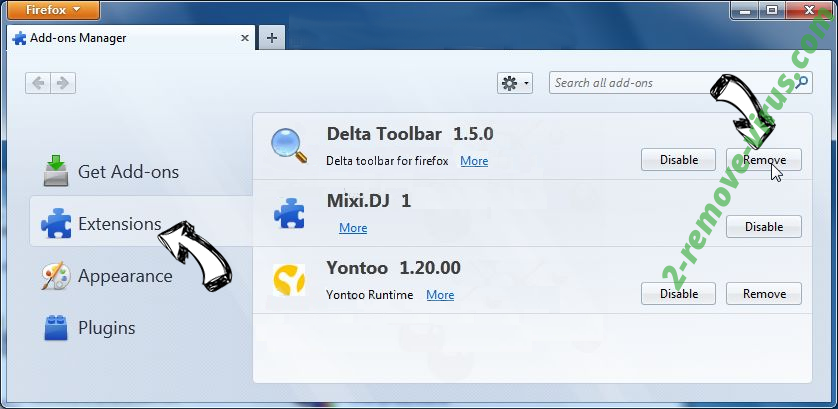
- In the top right corner of the screen, press menu and choose Add-ons (or tap Ctrl+Shift+A simultaneously).

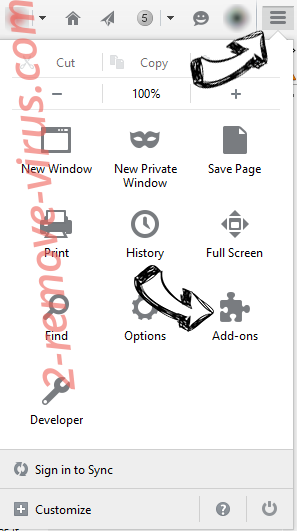
- Move to Extensions and Add-ons list and uninstall all suspicious and unknown entries.

Change Mozilla Firefox homepage if it was changed by virus:
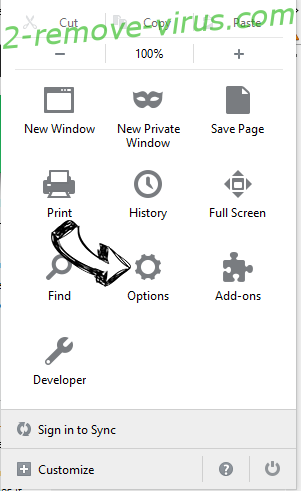
- Tap on the menu (top right corner), choose Options.

- On General tab delete malicious URL and enter preferable website or click Restore to default.

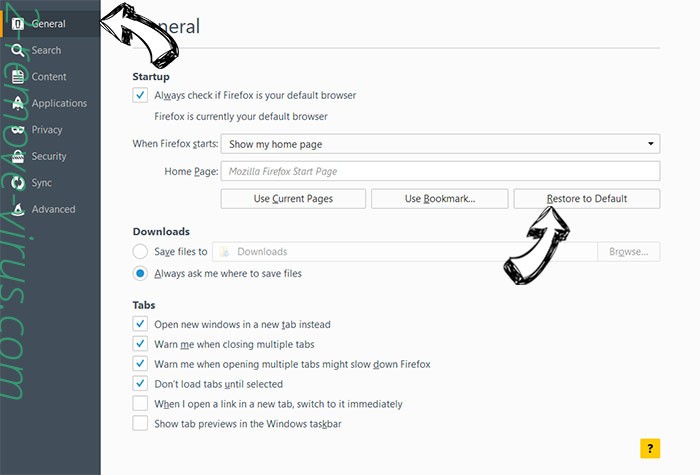
- Press OK to save these changes.
Reset your browser
- Open the menu and tap Help button.

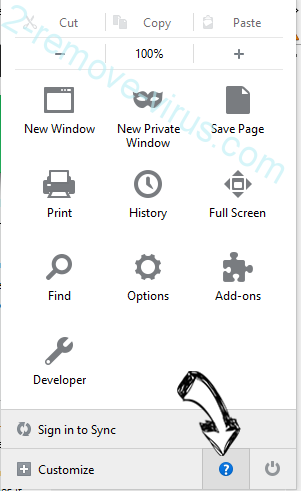
- Select Troubleshooting Information.

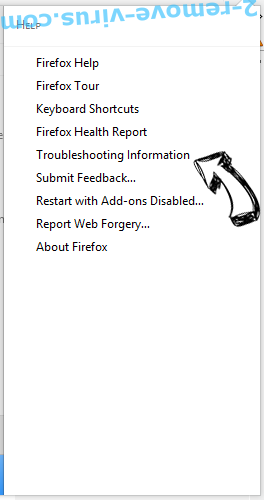
- Press Refresh Firefox.

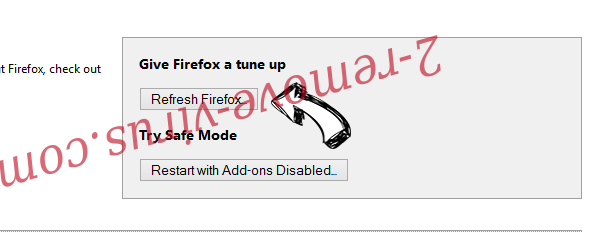
- In the confirmation box, click Refresh Firefox once more.

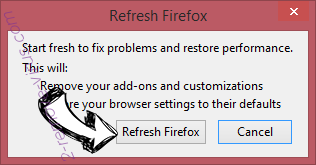
- If you are unable to reset Mozilla Firefox, scan your entire computer with a trustworthy anti-malware.
Uninstall Would Like To Use Your Computing Power Scam from Safari (Mac OS X)
- Access the menu.
- Pick Preferences.

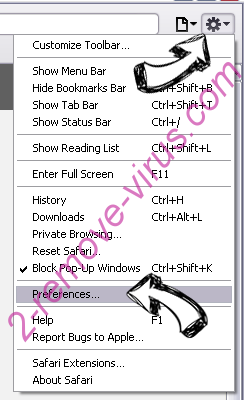
- Go to the Extensions Tab.

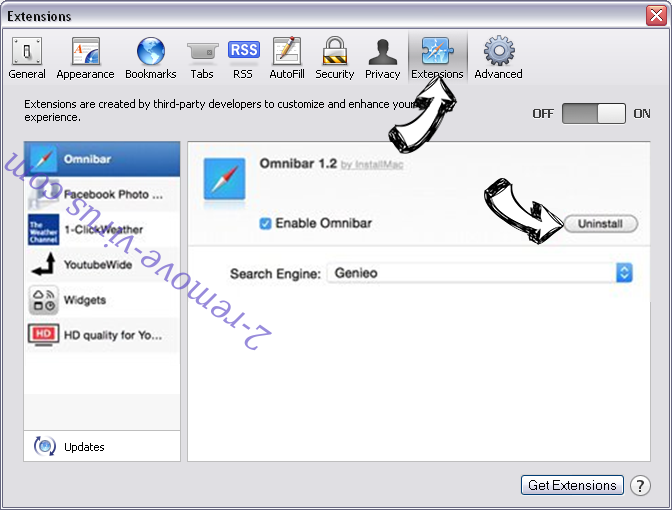
- Tap the Uninstall button next to the undesirable Would Like To Use Your Computing Power Scam and get rid of all the other unknown entries as well. If you are unsure whether the extension is reliable or not, simply uncheck the Enable box in order to disable it temporarily.
- Restart Safari.
Reset your browser
- Tap the menu icon and choose Reset Safari.


- Pick the options which you want to reset (often all of them are preselected) and press Reset.

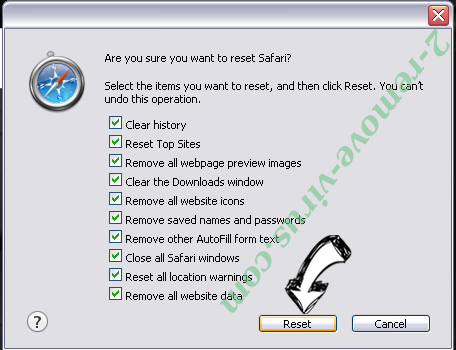
- If you cannot reset the browser, scan your whole PC with an authentic malware removal software.
Site Disclaimer
2-remove-virus.com is not sponsored, owned, affiliated, or linked to malware developers or distributors that are referenced in this article. The article does not promote or endorse any type of malware. We aim at providing useful information that will help computer users to detect and eliminate the unwanted malicious programs from their computers. This can be done manually by following the instructions presented in the article or automatically by implementing the suggested anti-malware tools.
The article is only meant to be used for educational purposes. If you follow the instructions given in the article, you agree to be contracted by the disclaimer. We do not guarantee that the artcile will present you with a solution that removes the malign threats completely. Malware changes constantly, which is why, in some cases, it may be difficult to clean the computer fully by using only the manual removal instructions.
