If the “Hello My Perverted Friend” email landed in your inbox, know that it’s a scam. Do not believe what’s written in the email as it’s merely a scare tactic to get you pay. You can just delete the “Hello My Perverted Friend” email scam from your inbox.
“Hello, my perverted friend,” is how this scam email starts. It falls into the category of sextortion scams because it threatens to release non-existent explicit videos of users if a payment is not made.
It’s a very generic sextortion scam that we have seen many times before. While the text may be phrased differently, the scam operates the same way as the others. The email sender first tries to catch the recipient’s attention with lines like “Hello, my perverted friend” and then proceeds to frighten users with claims about hacked devices and explicit videos.
The scammer claims that they were able to gain access to your device and take control of your webcam. They claim to have made an explicit video of you watching pornographic content and threaten to publish it on a pornographic site, as well as send it to all your contacts. They were supposedly able to gain access to your device by installing a “trojan on your hard disk”. The scammer even claims that your anti-virus program will not detect the trojan because its signature is updated every few hours.
According to the email, if you want to prevent the video from being leaked, you need to pay $890 in bitcoins to the provided wallet address. It goes without saying that this is nothing more than a scam. You do not need to pay anything, and there is no video.
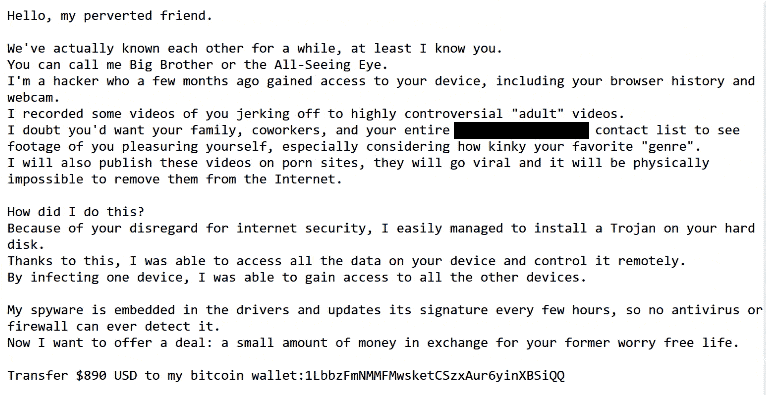
Subject: No reply.
Hello, my perverted friend.
We’ve actually known each other for a while, at least I know you.
You can call me Big Brother or the All-Seeing Eye.
I’m a hacker who a few months ago gained access to your device, including your browser history and webcam.
I recorded some videos of you jerking off to highly controversial “adult” videos.
I doubt you’d want your family, coworkers, and your entire ____ contact list to see footage of you pleasuring yourself, especially considering how kinky your favorite “genre”.
I will also publish these videos on porn sites, they will go viral and it will be physically impossible to remove them from the Internet.How did I do this?
Because of your disregard for internet security, I easily managed to install a Trojan on your hard disk.
Thanks to this, I was able to access all the data on your device and control it remotely.
By infecting one device, I was able to gain access to all the other devices.My spyware is embedded in the drivers and updates its signature every few hours, so no antivirus or firewall can ever detect it.
Now I want to offer a deal: a small amount of money in exchange for your former worry free life.Transfer $890 USD to my bitcoin wallet:1LbbzFmNMMFMwsketCSzxAur6yinXBSiQQ
As soon as I receive confirmation of the payment, I will delete all the videos that compromise you, remove the virus from all your devices and you will never hear from me again.
It’s a very small price for not destroying your reputation in the eyes of others, who think that you are a decent man, according to your messengers. You can think of me as some sort of life coach who wants you to start appreciating what you have.You have 48 hours. I will receive a notification as soon as you open this email, and from this moment, the countdown will begin.
If you’ve never dealt with cryptocurrency before, it’s very easy. Simply type “cryptocurrency exchange” into a search engine, and then all set.Here’s what you shouldn’t do:
– Don’t reply to my email. It was sent from a temporary email account.
– Don’t call the police. Remember, I have access to all your devices, and as soon as I notice such activity, it will automatically lead to the publishing of all the videos.
– Don’t try to reinstall your system or reset your device. First of all, I already have the videos, and secondly, as I said, I have remote access to all your devices, and once I notice such an attempt, you know what happens.Remember, crypto addresses are anonymous, so you won’t be able to track down my wallet.
So long story short, let’s resolve this situation with a benefit for me and you.
I always keep my word unless someone tries to trick me.Lastly, a little advice for the future. Start taking your online security more seriously.
Change your passwords regularly and set up multi-factor authentication on all your accounts.Best wishes.
These emails use scare tactics and threatening language to alarm users and pressure them into reacting without thinking twice. Regardless of whether the recipient has actually watched pornography or not, the scare tactics can sometimes work.
How did sextortion scammers obtain your email address?
You may be wondering how the scammer managed to obtain your email address if not because they hacked your computer. What likely happened is your email address was leaked by some service you use and ended up in a data package sold on a hacker forum. Malicious actors buy this type of data for their malicious purposes, be it scams or malware distribution. Unfortunately, once your email has been leaked, there’s not much you can do besides be more vigilant of potentially malicious emails. You can check whether your email address has been leaked on haveibeenpwned.
We should mention that to appear more convincing, sextortion emails can sometimes include legitimate passwords. When users see a password they use revealed in an email, they panic. However, malicious actors obtain passwords the same way they do email addresses. Services that do not have adequate security can become victims of breaches, and if passwords are not protected, they end up in the hands of cybercriminals. So if you see your password in an email, the service you used it for has been breached. In that case, you would need to change your password immediately. Passwords should be unique to each account and never reused.
Site Disclaimer
2-remove-virus.com is not sponsored, owned, affiliated, or linked to malware developers or distributors that are referenced in this article. The article does not promote or endorse any type of malware. We aim at providing useful information that will help computer users to detect and eliminate the unwanted malicious programs from their computers. This can be done manually by following the instructions presented in the article or automatically by implementing the suggested anti-malware tools.
The article is only meant to be used for educational purposes. If you follow the instructions given in the article, you agree to be contracted by the disclaimer. We do not guarantee that the artcile will present you with a solution that removes the malign threats completely. Malware changes constantly, which is why, in some cases, it may be difficult to clean the computer fully by using only the manual removal instructions.