Darj ransomware is a file-encrypting malware that belongs to the notorious Djvu/STOP malware family. Because files cannot always be recovered after being encrypted by this ransomware, it is considered to be a very serious malware infection. At the moment, only users who have backups will be able to recover their files without issue because a free Darj ransomware decryptor is not currently available. The cybercriminals operating the ransomware do have a decryptor but they will not offer it to you for free. You will be required to pay $980 in ransom to them. But even then, a decryptor is not guaranteed because malicious actors are not always willing to help victims, even after they pay.
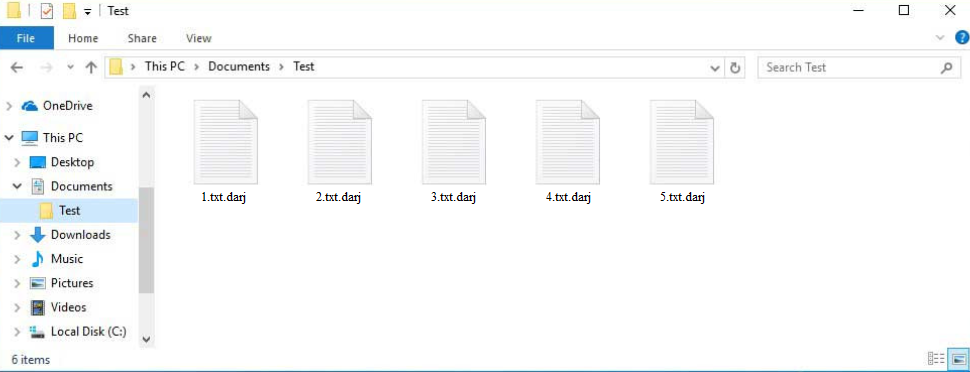
The Djvu/STOP ransomware family has hundreds of ransomware variants, with Darj ransomware being the most recent one. These variants are practically identical to one another but you can differentiate them by the extensions they add to encrypted files. For example, this ransomware adds .darj. So an encrypted text.txt file would become text.txt.darj. All your personal files will have this extension, including photos, videos, documents, images, etc. Unless you use a decryptor on these files first, none of them will be openable. However, the only people who possess a decryptor are the operators of this malware.
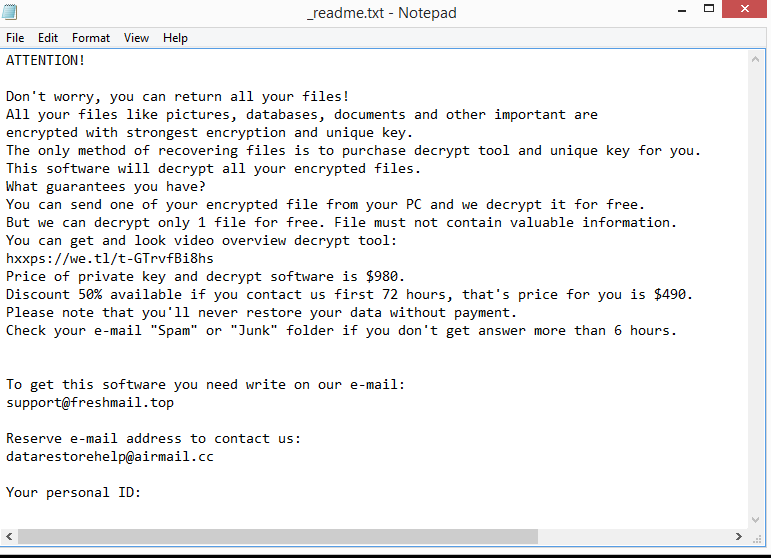
When the malware is initiated, it immediately starts encrypting files. The ransomware will show a fake Windows update window on your screen to divert your attention from what is actually happening. The ransomware will also drop a _readme.txt ransom note in each folder that has encrypted files once it has finished encrypting everything. The note is fairly generic and largely the same as those left by other ransomware in this family. It explains how to buy the decryptor, and unfortunately, the malicious actors will ask you to pay $980 for it. Supposedly, if you get in touch with them within the first 72 hours, you would receive a 50% discount. Victims who want to contact the malicious actors can use support@freshmail.top and datarestorehelp@airmail.cc.
The decision whether to pay or not is yours to make but you need to be aware of the risks that come with paying and why it’s not recommended. The main reason is that paying does not guarantee a decryptor. You need to keep in mind that you are dealing with cyber criminals, and there is nothing to force them to help you. They can easily just take your money and not send a decryptor. Furthermore, the money you pay would go towards future criminal activities. As long as victims keep paying the demanded ransom, ransomware will continue to thrive.
Unfortunately, you might not be able to recover your data if you do not have a backup. If you don’t have a backup, waiting for a free Darj ransomware to be released may be your only option. You won’t find one at the moment but it may be released in the future. However, because ransomware from this family uses online keys to encrypt files, it’s very difficult for malware researchers to develop decryptors. The keys are unique to each victim, and without those keys, a decryptor is not very likely. Nonetheless, all hope is not lost, and if a decryptor does get released, it would appear on NoMoreRansom.
As long as you remove Darj ransomware from your computer before accessing your backup, you should have no issues with recovering files. For Darj ransomware removal, make sure to use an anti-malware program because manual removal could cause issues.
How to protect yourself from ransomware infections
Users frequently acquire ransomware through malicious email attachments. So by just being more careful about which emails and attachments you open, you should be able to avoid some malware infections. You are particularly likely to receive malicious emails if your email address has been leaked. Cybercriminals buy leaked email addresses from hacker forums and use them for their malicious campaigns. Fortunately, malware-carrying emails are often very easy to recognize. For one, they are usually full of grammar/spelling mistakes. If the sender claims to be from a legitimate company but the email contains obvious grammar/spelling mistakes, it’s more than likely that the email is malicious, or at least spam.
Another giveaway is when senders who should know your name use generic words like User, Member, Customer, etc., to address you. Emails from companies whose services you use will always address you by name because it makes the emails seem more personal. But one malicious campaign can target hundreds if not thousands of users at once so potential victims are addressed with generic words.
It’s worth mentioning that some malicious campaigns can be much more sophisticated. If they target someone specific, the emails would be free of mistakes, address the target by name, as well as contain some detail(s) that would give them credibility. Thus, it’s recommended to use anti-virus programs or VirusTotal to scan email attachments before opening them.
Malware is also frequently found in torrents. Torrent sites are usually poorly regulated, and this allows malicious actors to upload torrents with malware in them. Malware is most frequently found in torrents for well-known media, including movies, TV shows, video games, software, etc. For example, torrents for the highly popular TV series The Last of Us often contain malware. So using torrents to pirate copyrighted content is not only content theft, but it’s also dangerous.
Other methods of encountering malware include clicking on advertisements and installing programs from dubious sources. It’s a good idea to form healthy browsing habits to prevent infections.
How to remove Darj ransomware
You shouldn’t try to manually remove Darj ransomware because you risk making things worse. Ransomware is a fairly complex malware infection and the use of a professional program is recommended. You can begin file recovery as soon as you are certain the ransomware has been removed. And if you don’t have a backup, we advise backing up your encrypted files while you wait for a free decryptor to become accessible.
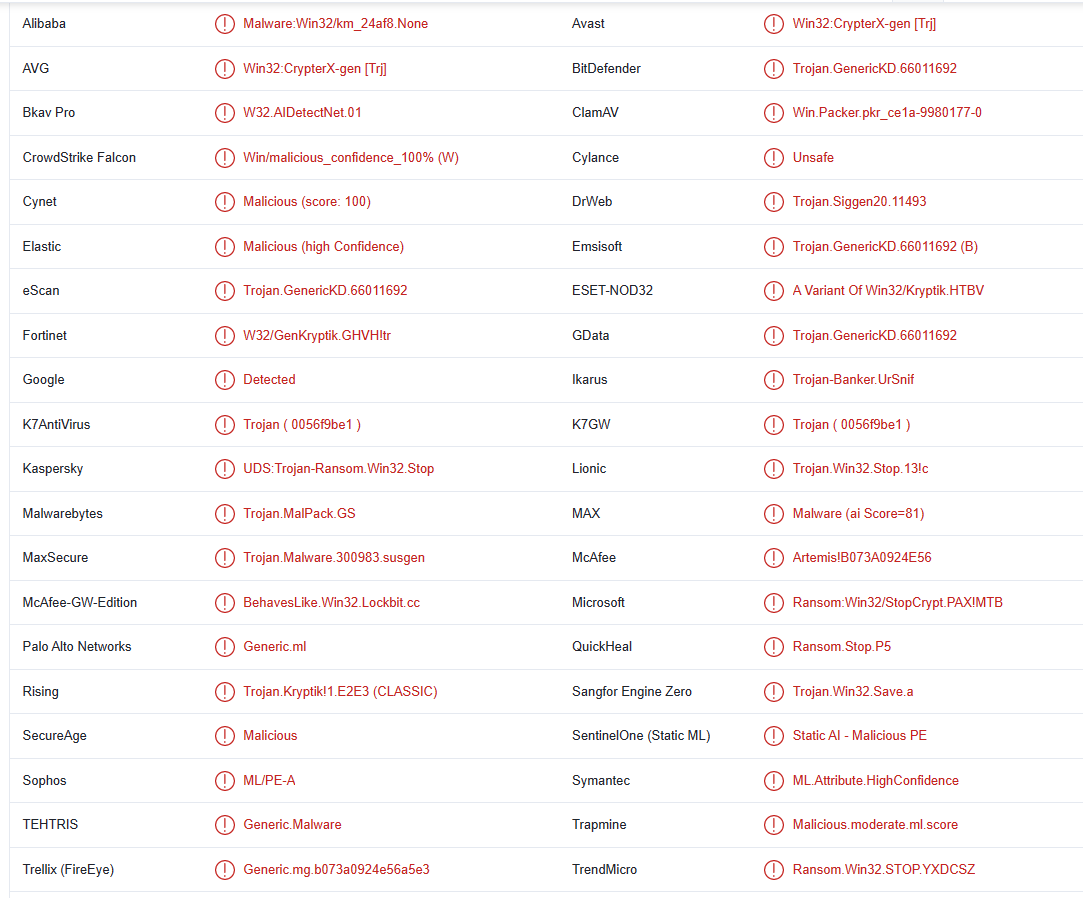
Darj ransomware is detected as:
- Win32:CrypterX-gen [Trj] by AVG/Avast
- UDS:Trojan-Ransom.Win32.Stop by Kaspersky
- Trojan.MalPack.GS by Malwarebytes
- Trojan.GenericKD.66011692 by BitDefender
- Trojan.GenericKD.66011692 (B) by Emsisoft
- A Variant Of Win32/Kryptik.HTBV by ESET
- Artemis!B073A0924E56 by McAfee
- Ransom:Win32/StopCrypt.PAX!MTB by Microsoft
- Ransom.Win32.STOP.YXDCSZ by TrendMicro
Quick Menu
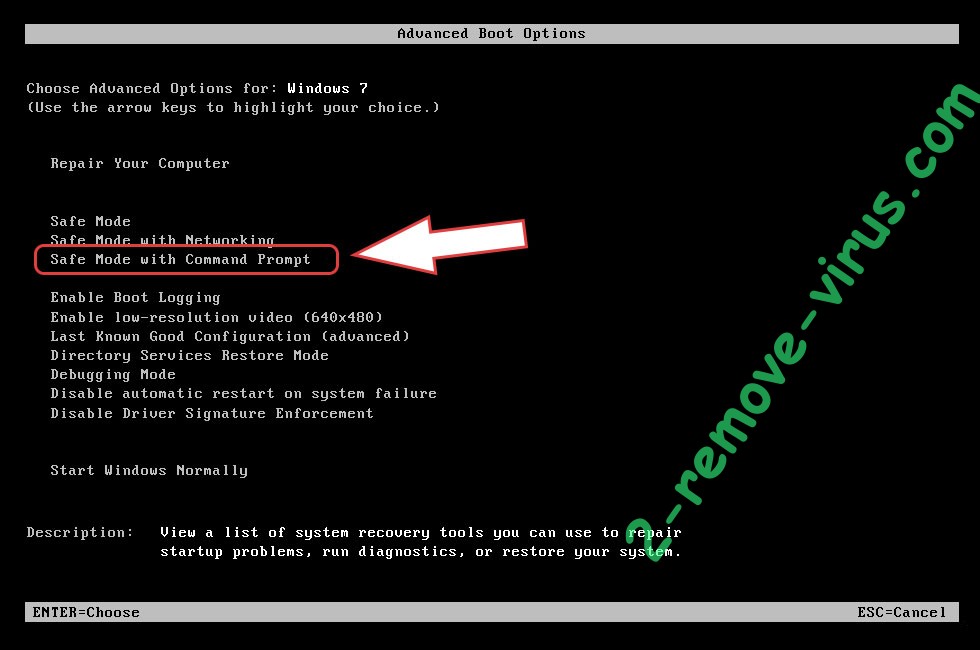
Step 1. Delete Darj ransomware using Safe Mode with Networking.
Remove Darj ransomware from Windows 7/Windows Vista/Windows XP
- Click on Start and select Shutdown.
- Choose Restart and click OK.

- Start tapping F8 when your PC starts loading.
- Under Advanced Boot Options, choose Safe Mode with Networking.

- Open your browser and download the anti-malware utility.
- Use the utility to remove Darj ransomware
Remove Darj ransomware from Windows 8/Windows 10
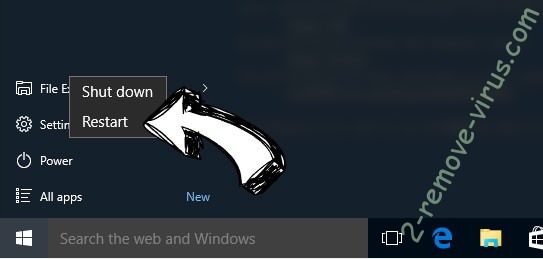
- On the Windows login screen, press the Power button.
- Tap and hold Shift and select Restart.

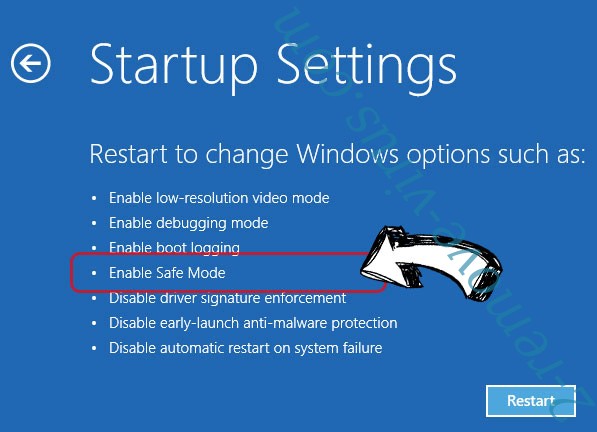
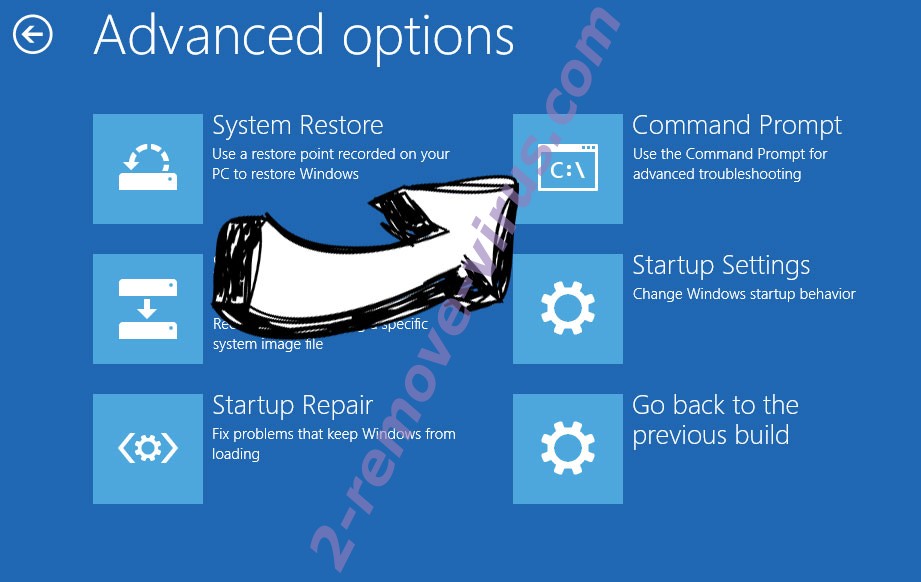
- Go to Troubleshoot → Advanced options → Start Settings.
- Choose Enable Safe Mode or Safe Mode with Networking under Startup Settings.

- Click Restart.
- Open your web browser and download the malware remover.
- Use the software to delete Darj ransomware
Step 2. Restore Your Files using System Restore
Delete Darj ransomware from Windows 7/Windows Vista/Windows XP
- Click Start and choose Shutdown.
- Select Restart and OK

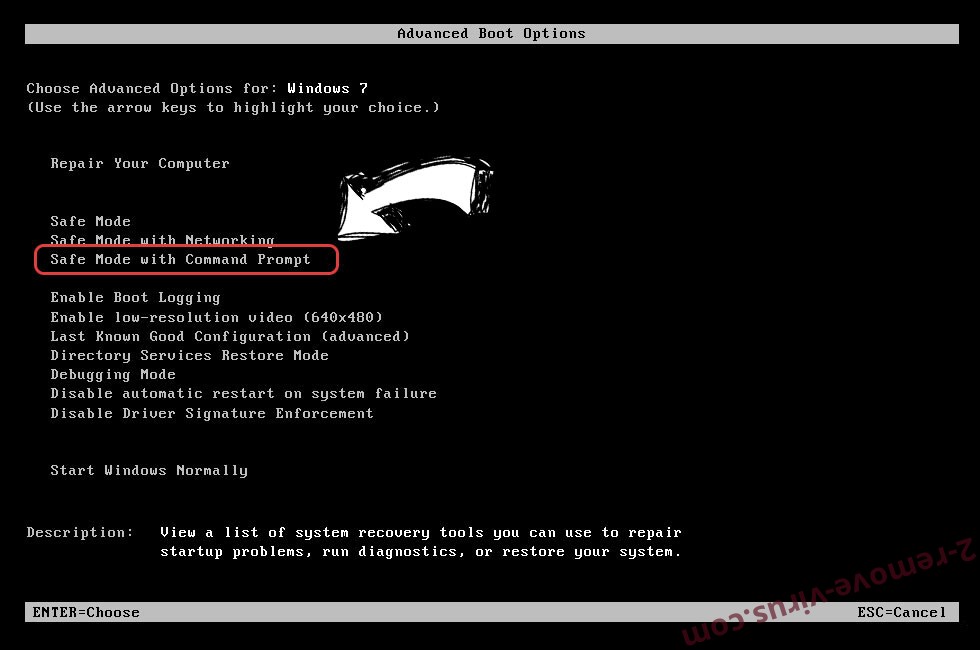
- When your PC starts loading, press F8 repeatedly to open Advanced Boot Options
- Choose Command Prompt from the list.

- Type in cd restore and tap Enter.

- Type in rstrui.exe and press Enter.

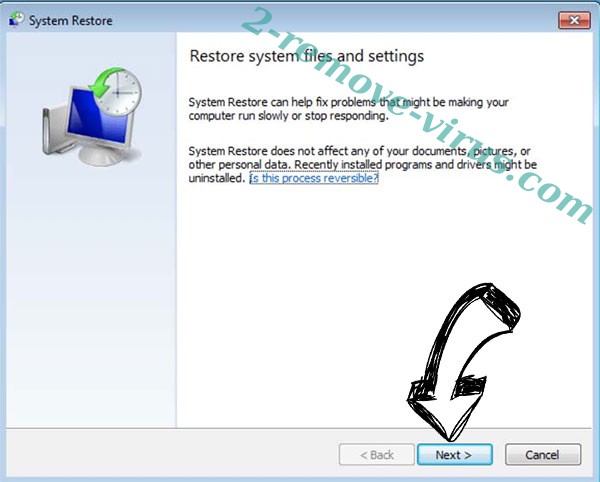
- Click Next in the new window and select the restore point prior to the infection.

- Click Next again and click Yes to begin the system restore.

Delete Darj ransomware from Windows 8/Windows 10
- Click the Power button on the Windows login screen.
- Press and hold Shift and click Restart.

- Choose Troubleshoot and go to Advanced options.
- Select Command Prompt and click Restart.

- In Command Prompt, input cd restore and tap Enter.

- Type in rstrui.exe and tap Enter again.

- Click Next in the new System Restore window.

- Choose the restore point prior to the infection.

- Click Next and then click Yes to restore your system.

Offers
Download Removal Toolto scan for Darj ransomwareUse our recommended removal tool to scan for Darj ransomware. Trial version of provides detection of computer threats like Darj ransomware and assists in its removal for FREE. You can delete detected registry entries, files and processes yourself or purchase a full version.
More information about SpyWarrior and Uninstall Instructions. Please review SpyWarrior EULA and Privacy Policy. SpyWarrior scanner is free. If it detects a malware, purchase its full version to remove it.

WiperSoft Review Details WiperSoft (www.wipersoft.com) is a security tool that provides real-time security from potential threats. Nowadays, many users tend to download free software from the Intern ...
Download|more


Is MacKeeper a virus? MacKeeper is not a virus, nor is it a scam. While there are various opinions about the program on the Internet, a lot of the people who so notoriously hate the program have neve ...
Download|more


While the creators of MalwareBytes anti-malware have not been in this business for long time, they make up for it with their enthusiastic approach. Statistic from such websites like CNET shows that th ...
Download|more
Site Disclaimer
2-remove-virus.com is not sponsored, owned, affiliated, or linked to malware developers or distributors that are referenced in this article. The article does not promote or endorse any type of malware. We aim at providing useful information that will help computer users to detect and eliminate the unwanted malicious programs from their computers. This can be done manually by following the instructions presented in the article or automatically by implementing the suggested anti-malware tools.
The article is only meant to be used for educational purposes. If you follow the instructions given in the article, you agree to be contracted by the disclaimer. We do not guarantee that the artcile will present you with a solution that removes the malign threats completely. Malware changes constantly, which is why, in some cases, it may be difficult to clean the computer fully by using only the manual removal instructions.