OBZ ransomware is a malware infection that will effectively take your files hostage by encrypting them. As soon as files are encrypted, they will remain locked until you run a special decryptor. Files could be encrypted permanently. This makes ransomware a very dangerous malware infection. It will be difficult to obtain the decryptor because only the malware operators have it. It’s not clear how much the decryptor costs but whatever the price may be, paying is risky because it will not necessarily result in decrypted files.
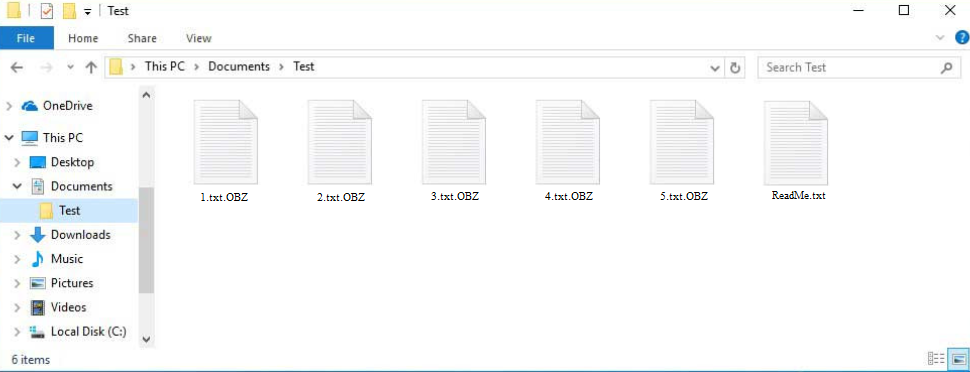
The malware will start encrypting files as soon as you initiate an infected file. It will mostly target personal files, including photos, videos, documents, etc. Each encrypted file will have .obz added to it. For example, text.txt would become text.txt.obz if encrypted by this ransomware. The malware would also drop a ReadMe.txt ransom note.
The ransom note explains how to obtain the decryptor. Unfortunately, to get it, you’d need to pay a ransom. The amount is not specified and may vary depending on the victim. If you’re considering paying the ransom, you need to be aware of the fact that you will not necessarily get the decryptor. You are dealing with cyber criminals, and you cannot force them to send you the decryptor even if you pay.
Unfortunately, there currently is no free OBZ ransomware decryptor available. Free decryptors are occasionally released by malware researchers to help victims but it’s not always possible. Unfortunately, at the moment, that is the case with OBZ ransomware. But if a decryptor is ever released, it would be posted on NoMoreRansom.
You may start recovering your files from your backup as soon as you remove OBZ ransomware from your computer. It is strongly advised that you use a good anti-malware program because manual OBZ ransomware removal could be very difficult.
Attention!
All your files, documents, photos, databases and other important files are encrypted
The only method of recovering files is to purchase an unique decryptor. Only we can give you this decryptor and only we can recover your files.
The server with your decryptor is in a closed network TOR. You can get there by the following ways:
————————————————–
1. Download Tor browser – hxxps://www.torproject.org/
2. Install Tor browser
3. Open Tor Browser
4. Open link in TOR browser: hxxp://obzuqvr5424kkc4unbq2p2i67ny3zngce3tbdr37nicjqesgqcgomfqd.onion/?101VWOPRTUL
5. and open ticket————————————————–
Alternate communication channel here: hxxps://yip.su/2QstD5
Ways ransomware enters computers
Malware may enter a computer in many different ways. Users most frequently come into contact with malware through email attachments, torrents, downloads from questionable sites, etc. To put it simply, the poorer someone’s browsing habits are, the more likely are they to come across some type of malware. We strongly recommend that you change your browsing habits if you want to avoid malware infections in the future.
Users opening unsolicited email attachments is one of the most typical ways malware gets into computers. Malicious emails are often disguised to look like they are sent by legitimate companies, though fortunately for users, the emails are very poorly done. The majority of the time, these emails are full of grammar and spelling mistakes, which immediately gives them away as malicious. Malicious actors usually have very poor English language skills, which results in mistakes in their malicious email campaigns. Since mistakes make emails appear unprofessional, legitimate emails seldom have them.
If you are addressed in an email as “User”, “Member”, or “Customer”, it could also be a sign of a malicious email. Companies whose services you use will always refer to you by name in emails. Therefore, if the sender addresses you in a generic manner even though they should know your name, you could be dealing with a malicious email.
By researching the sender’s email address, you can also tell whether an email is malicious. Check the sender’s email address carefully if you get an email that asks you to do something, such as clicking a link or opening an attachment. If the address appears to be random, the email is probably malicious. However, an email address could occasionally appear to be quite authentic, so you should research it before engaging with the email.
It’s important to note that certain malicious campaigns may be more advanced than others. But it usually only happens when someone is a specific target. If the malicious actors can obtain the target’s personal information, they may be able to make the emails look more real. Such an email would be free of mistakes, address the recipient by name, and even include details that would give it credibility. It is thus recommended to scan all unsolicited email attachments with VirusTotal or anti-virus software before opening them.
Lastly, you are probably well aware that malware is regularly spread via torrents. Malicious actors are able to upload torrents with malware on torrent sites because they are often inadequately moderated. Malware is most typically seen in torrents for entertainment-related content. For instance, torrents for movies, TV shows, and video games often contain malware. Using torrents puts your computer at risk. Furthermore, downloading copyrighted content through torrents is essentially theft.
How to delete OBZ ransomware
We do not recommend attempting to manually remove OBZ ransomware because you run the risk of causing further damage to your computer. OBZ ransomware might not be completely removed if you don’t use a good anti-virus program to remove it, and that could allow it to recover later on. The files in your backup would get encrypted if you tried to access them while the ransomware was still active on your computer.
Without a backup, file recovery will be extremely difficult, if not impossible. At the moment, the only free way to recover files is a backup. If you don’t have a backup, you will have to wait until a free OBZ ransomware decryptor is released. But it’s unclear exactly when that will happen. You should occasionally check NoMoreRansom for a decryptor and back up the encrypted files while you wait.
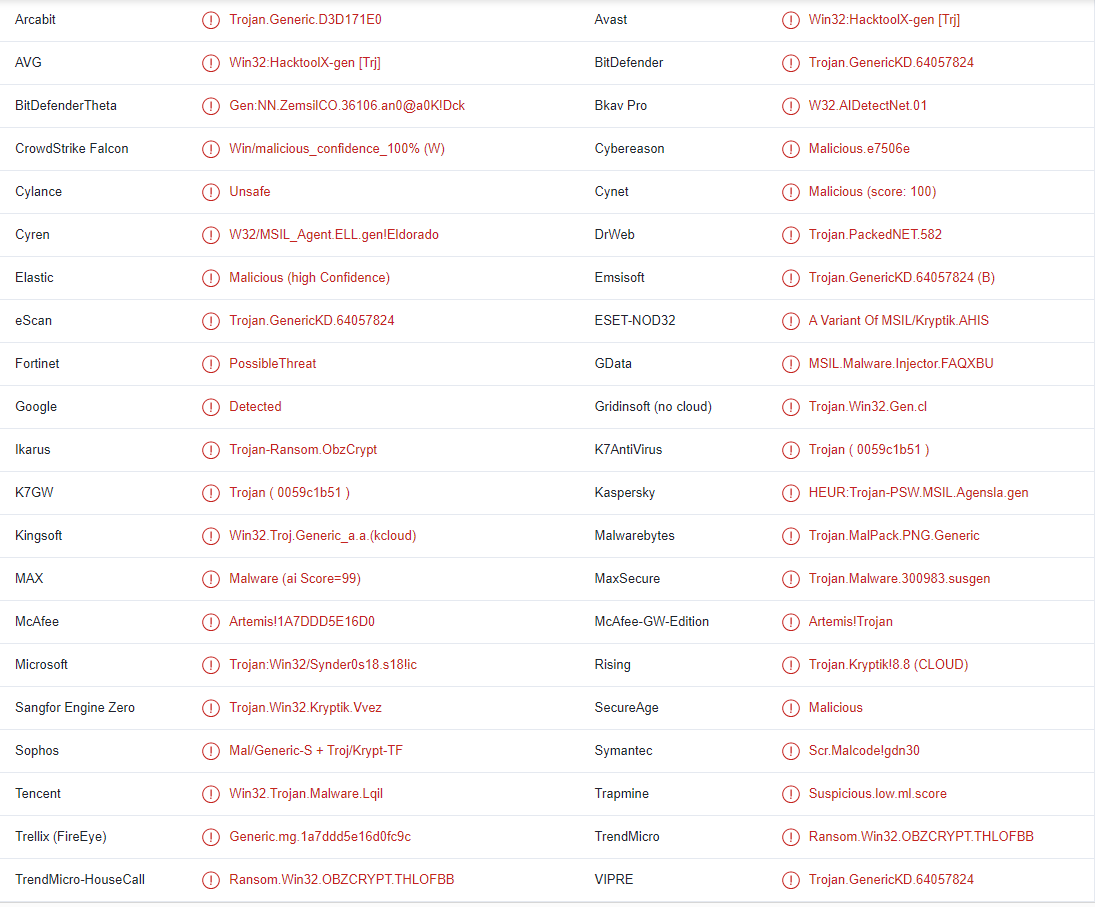
OBZ ransomware is detected as:
- Win32:HacktoolX-gen [Trj] by AVG/Avast
- Artemis!1A7DDD5E16D0 by McAfee
- Trojan:Win32/Synder0s18.s18!ic by Microsoft
- Trojan.GenericKD.64057824 by BitDefender
- A Variant Of MSIL/Kryptik.AHIS by ESET
- Trojan.GenericKD.64057824 (B) by Emsisoft
- HEUR:Trojan-PSW.MSIL.Agensla.gen by Kaspersky
- Trojan.MalPack.PNG.Generic by Malwarebytes
- Ransom.Win32.OBZCRYPT.THLOFBB by TrendMicro
Quick Menu
Step 1. Delete OBZ ransomware using Safe Mode with Networking.
Remove OBZ ransomware from Windows 7/Windows Vista/Windows XP
- Click on Start and select Shutdown.
- Choose Restart and click OK.

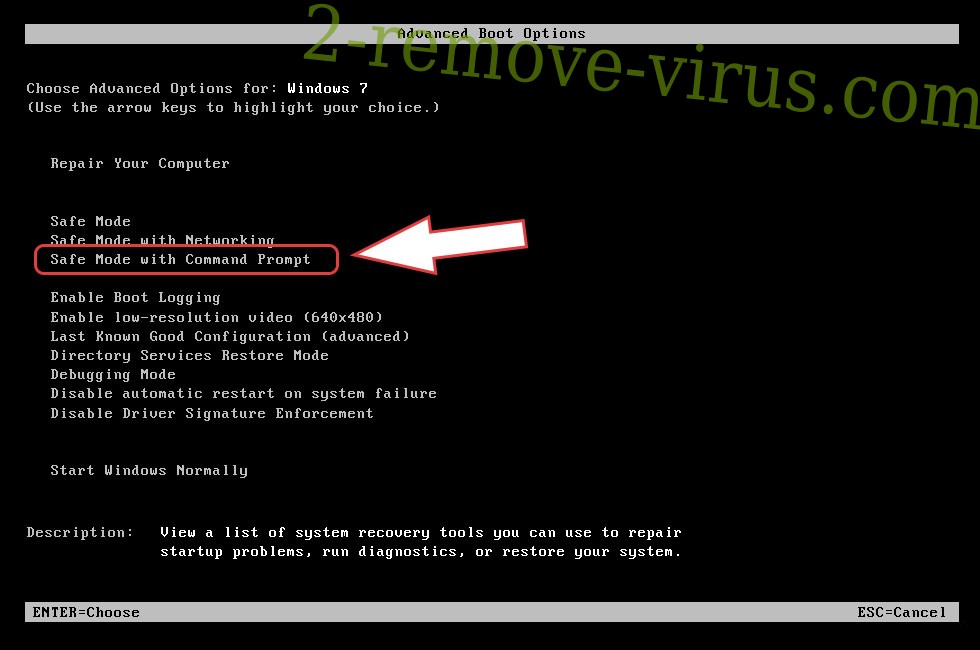
- Start tapping F8 when your PC starts loading.
- Under Advanced Boot Options, choose Safe Mode with Networking.

- Open your browser and download the anti-malware utility.
- Use the utility to remove OBZ ransomware
Remove OBZ ransomware from Windows 8/Windows 10
- On the Windows login screen, press the Power button.
- Tap and hold Shift and select Restart.

- Go to Troubleshoot → Advanced options → Start Settings.
- Choose Enable Safe Mode or Safe Mode with Networking under Startup Settings.

- Click Restart.
- Open your web browser and download the malware remover.
- Use the software to delete OBZ ransomware
Step 2. Restore Your Files using System Restore
Delete OBZ ransomware from Windows 7/Windows Vista/Windows XP
- Click Start and choose Shutdown.
- Select Restart and OK

- When your PC starts loading, press F8 repeatedly to open Advanced Boot Options
- Choose Command Prompt from the list.

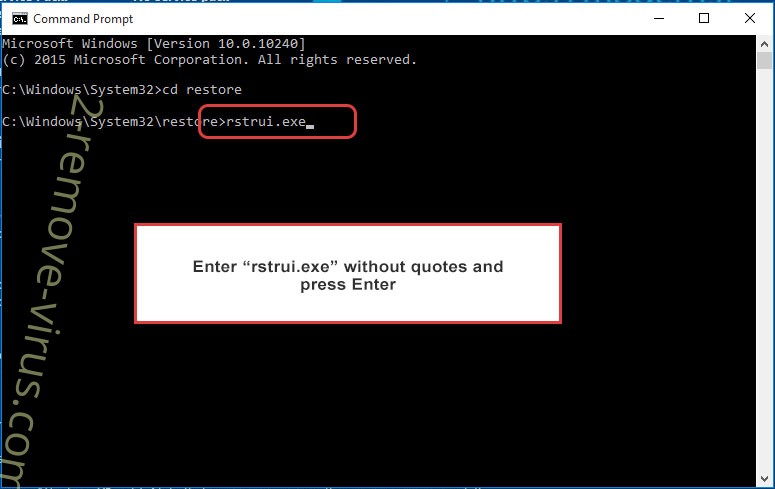
- Type in cd restore and tap Enter.

- Type in rstrui.exe and press Enter.

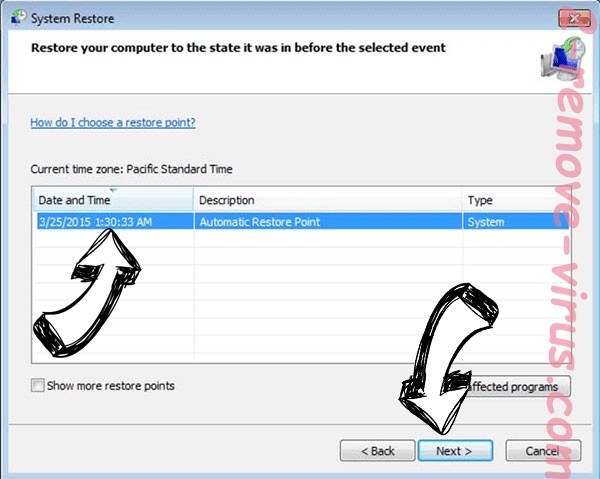
- Click Next in the new window and select the restore point prior to the infection.

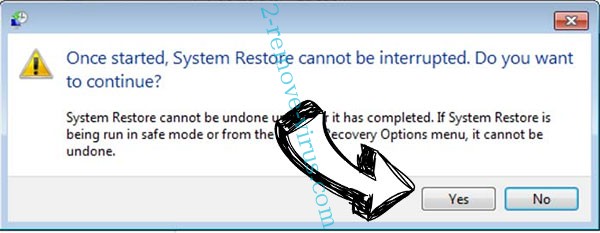
- Click Next again and click Yes to begin the system restore.

Delete OBZ ransomware from Windows 8/Windows 10
- Click the Power button on the Windows login screen.
- Press and hold Shift and click Restart.

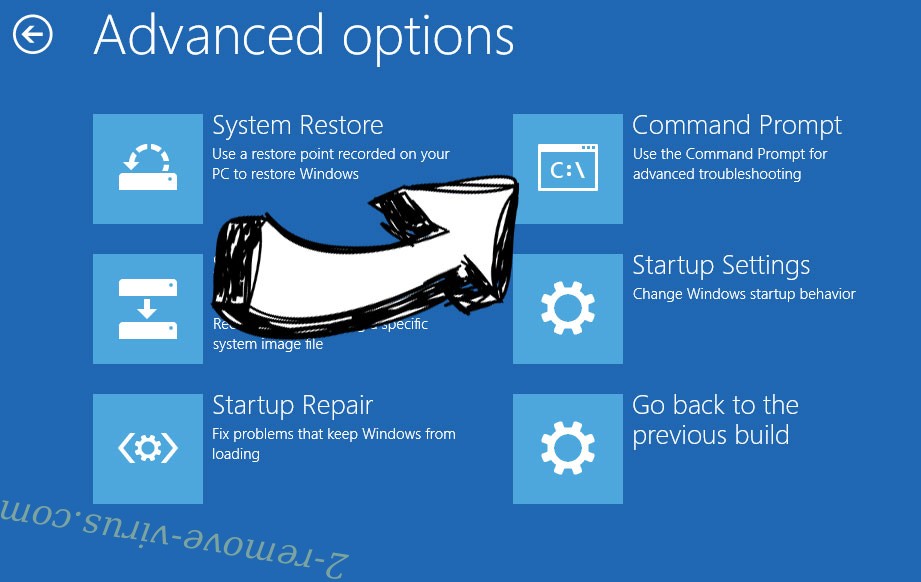
- Choose Troubleshoot and go to Advanced options.
- Select Command Prompt and click Restart.

- In Command Prompt, input cd restore and tap Enter.

- Type in rstrui.exe and tap Enter again.

- Click Next in the new System Restore window.

- Choose the restore point prior to the infection.

- Click Next and then click Yes to restore your system.

Offers
Download Removal Toolto scan for OBZ ransomwareUse our recommended removal tool to scan for OBZ ransomware. Trial version of provides detection of computer threats like OBZ ransomware and assists in its removal for FREE. You can delete detected registry entries, files and processes yourself or purchase a full version.
More information about SpyWarrior and Uninstall Instructions. Please review SpyWarrior EULA and Privacy Policy. SpyWarrior scanner is free. If it detects a malware, purchase its full version to remove it.

WiperSoft Review Details WiperSoft (www.wipersoft.com) is a security tool that provides real-time security from potential threats. Nowadays, many users tend to download free software from the Intern ...
Download|more


Is MacKeeper a virus? MacKeeper is not a virus, nor is it a scam. While there are various opinions about the program on the Internet, a lot of the people who so notoriously hate the program have neve ...
Download|more


While the creators of MalwareBytes anti-malware have not been in this business for long time, they make up for it with their enthusiastic approach. Statistic from such websites like CNET shows that th ...
Download|more
Site Disclaimer
2-remove-virus.com is not sponsored, owned, affiliated, or linked to malware developers or distributors that are referenced in this article. The article does not promote or endorse any type of malware. We aim at providing useful information that will help computer users to detect and eliminate the unwanted malicious programs from their computers. This can be done manually by following the instructions presented in the article or automatically by implementing the suggested anti-malware tools.
The article is only meant to be used for educational purposes. If you follow the instructions given in the article, you agree to be contracted by the disclaimer. We do not guarantee that the artcile will present you with a solution that removes the malign threats completely. Malware changes constantly, which is why, in some cases, it may be difficult to clean the computer fully by using only the manual removal instructions.