About COPA ransomware
The ransomware known as COPA ransomware is categorized as a very damaging infection, due to the possible harm it could cause. If you have never heard of this type of malware until now, you might be in for a surprise. File encoding malware uses strong encryption algorithms for data encryption, and once it’s done executing the process, you’ll be unable to open them. The reason this malware is considered to be a serious threat is because ransomware encrypted files are not always recoverable. 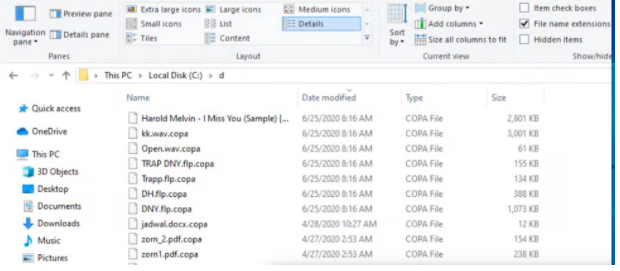
Crooks will give you the option of decrypting files by paying the ransom, but that option isn’t recommended for a few reasons. First of all, paying will not guarantee file decryption. It would be naive to think that the people who encrypted your data in the first place will feel obligated to help you restore data, when they don’t have to. You ought to also take into account that the money will be used for malicious software projects in the future. It’s already estimated that file encoding malware costs millions of dollars in losses to different businesses in 2017, and that is an estimation only. The more people pay, the more profitable it gets, thus drawing more crooks who want to earn easy money. Investing that money into backup would be a much better decision because if you ever encounter this type of situation again, you could just unlock COPA ransomware data from backup and not worry about losing them. And you could simply remove COPA ransomware without problems. If you’re confused about how the threat managed to get into your system, we will explain the most frequent spread methods in the below paragraph.
How is COPA ransomware distributed
Email attachments, exploit kits and malicious downloads are the spread methods you need to be careful about the most. Seeing as these methods are still used, that means that users are pretty careless when they use email and download files. Nevertheless, some file encoding malware might be spread using more sophisticated methods, which require more time and effort. Crooks don’t have to do much, just write a simple email that seems quite convincing, add the infected file to the email and send it to hundreds of people, who might think the sender is someone trustworthy. Commonly, the emails will mention money, which users tend to take seriously. Crooks prefer to pretend to be from Amazon and warn you that there was strange activity in your account or a purchase was made. Because of this, you have to be careful about opening emails, and look out for signs that they might be malicious. Before proceeding to open the attached file, look into the sender of the email. And if you do know them, check the email address to make sure it matches the person’s/company’s real address. The emails also commonly contain grammar mistakes, which tend to be pretty obvious. Take note of how you’re addressed, if it’s a sender with whom you have had business before, they will always greet you by your name, instead of a universal Customer or Member. Vulnerabilities on your computer Out-of-date software may also be used as a pathway to you system. A program has vulnerabilities that could be exploited by ransomware but normally, they’re patched when the vendor finds out about it. Unfortunately, as shown by the WannaCry ransomware, not everyone installs those patches, for different reasons. You are suggested to update your software, whenever a patch becomes available. Patches can be set to install automatically, if you find those notifications bothersome.
What can you do about your files
A file encoding malicious program will scan for specific file types once it enters the system, and when they’re found, they’ll be encrypted. You will not be able to open your files, so even if you don’t see what is going initially, you will know something’s not right eventually. You will know which files have been encrypted because they will have a weird extension attached to them. Powerful encryption algorithms could have been used to encode your data, and it is possible that they may be encoded without likelihood to restore them. After all data has been locked, a ransom note will appear, which will attempt to explain what has occurred and how you should proceed. They will propose you a decryption program, which will not come for free. The note ought to specify the price for a decryption tool but if that’s not the case, you’ll have to email criminals through their given address. Obviously, we do not believe paying is a wise idea, for the previously mentioned reasons. Look into every other likely option, before you even think about buying what they offer. Maybe you’ve stored your files somewhere but simply forgotten about it. Or, if you’re lucky, someone may have published a free decryptor. Sometimes malware researchers are capable of cracking a file encrypting malicious software, which means you may get a decryptor with no payments necessary. Keep this in mind before paying the requested money even crosses your mind. Investing part of that money to buy some kind of backup might turn out to be more beneficial. And if backup is an option, you may restore data from there after you uninstall COPA ransomware virus, if it still remains on your device. In the future, make sure you avoid ransomware as much as possible by familiarizing yourself how it’s distributed. At the very least, do not open email attachments left and right, keep your software up-to-date, and only download from real sources.
COPA ransomware removal
If the ransomware is still in the computer, an anti-malware tool should be used to terminate it. To manually fix COPA ransomware virus is no simple process and might lead to additional damage to your computer. Using a malware removal tool would be much less troublesome. The program is not only capable of helping you take care of the threat, but it may also stop similar ones from getting in in the future. Choose the malware removal tool that would best match what you need, download it, and scan your system for the threat once you install it. It should be said that an anti-malware software is meant to terminate the threat and not to help recover data. If your computer has been fully cleaned, unlock COPA ransomware files from backup, if you have it.
Offers
Download Removal Toolto scan for COPA ransomwareUse our recommended removal tool to scan for COPA ransomware. Trial version of provides detection of computer threats like COPA ransomware and assists in its removal for FREE. You can delete detected registry entries, files and processes yourself or purchase a full version.
More information about SpyWarrior and Uninstall Instructions. Please review SpyWarrior EULA and Privacy Policy. SpyWarrior scanner is free. If it detects a malware, purchase its full version to remove it.

WiperSoft Review Details WiperSoft (www.wipersoft.com) is a security tool that provides real-time security from potential threats. Nowadays, many users tend to download free software from the Intern ...
Download|more


Is MacKeeper a virus? MacKeeper is not a virus, nor is it a scam. While there are various opinions about the program on the Internet, a lot of the people who so notoriously hate the program have neve ...
Download|more


While the creators of MalwareBytes anti-malware have not been in this business for long time, they make up for it with their enthusiastic approach. Statistic from such websites like CNET shows that th ...
Download|more
Quick Menu
Step 1. Delete COPA ransomware using Safe Mode with Networking.
Remove COPA ransomware from Windows 7/Windows Vista/Windows XP
- Click on Start and select Shutdown.
- Choose Restart and click OK.

- Start tapping F8 when your PC starts loading.
- Under Advanced Boot Options, choose Safe Mode with Networking.

- Open your browser and download the anti-malware utility.
- Use the utility to remove COPA ransomware
Remove COPA ransomware from Windows 8/Windows 10
- On the Windows login screen, press the Power button.
- Tap and hold Shift and select Restart.

- Go to Troubleshoot → Advanced options → Start Settings.
- Choose Enable Safe Mode or Safe Mode with Networking under Startup Settings.

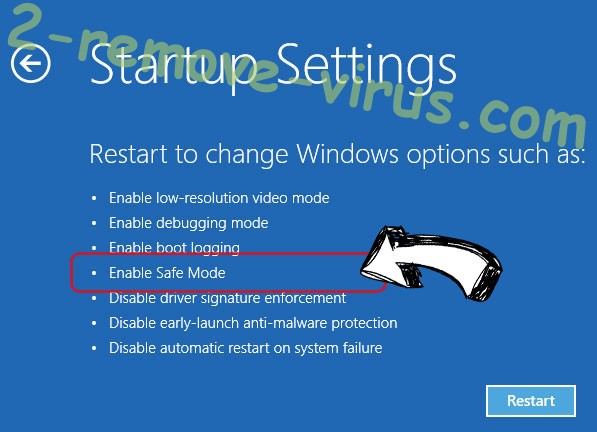
- Click Restart.
- Open your web browser and download the malware remover.
- Use the software to delete COPA ransomware
Step 2. Restore Your Files using System Restore
Delete COPA ransomware from Windows 7/Windows Vista/Windows XP
- Click Start and choose Shutdown.
- Select Restart and OK


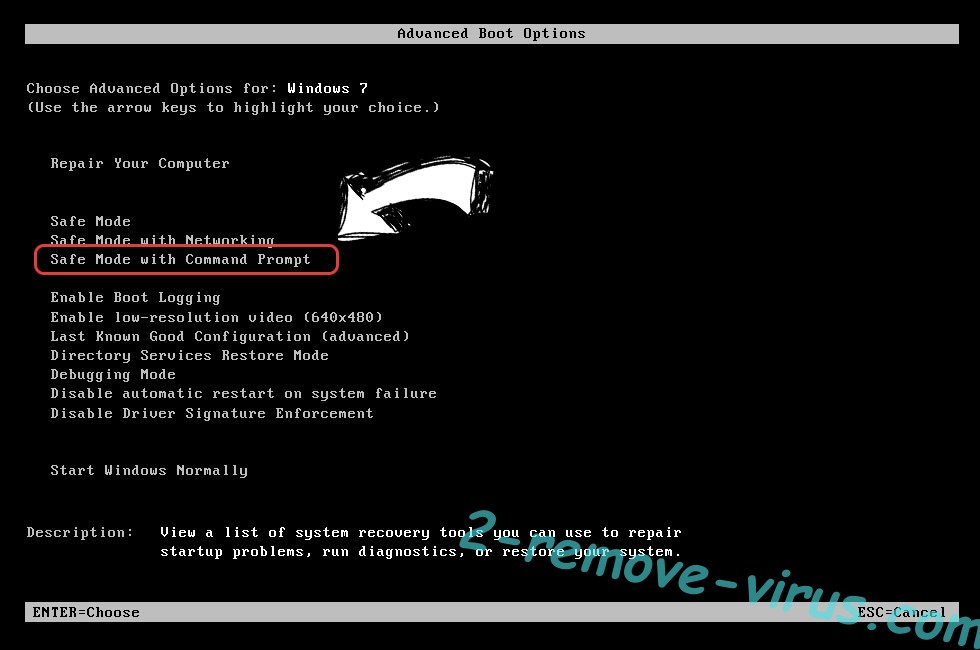
- When your PC starts loading, press F8 repeatedly to open Advanced Boot Options
- Choose Command Prompt from the list.

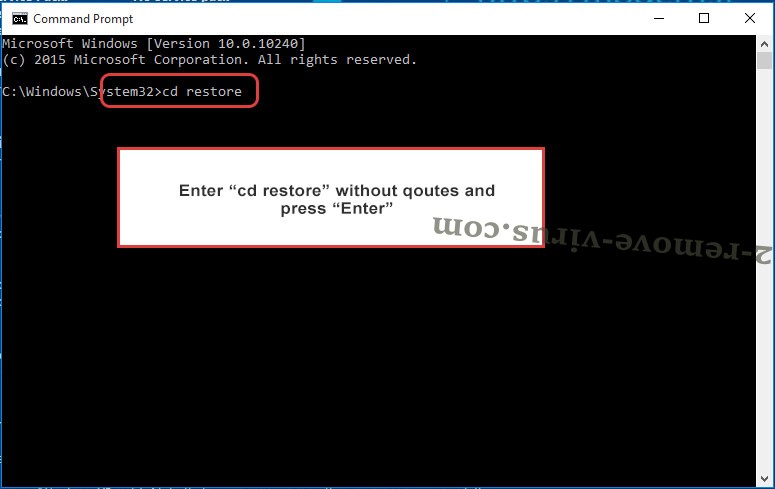
- Type in cd restore and tap Enter.

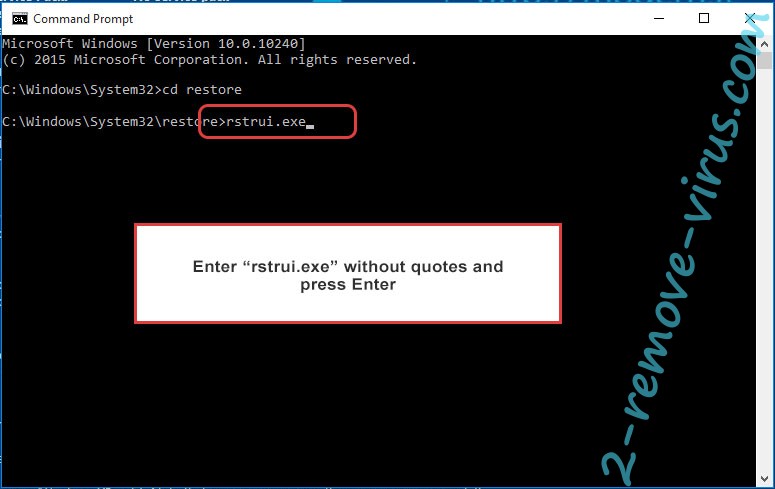
- Type in rstrui.exe and press Enter.

- Click Next in the new window and select the restore point prior to the infection.

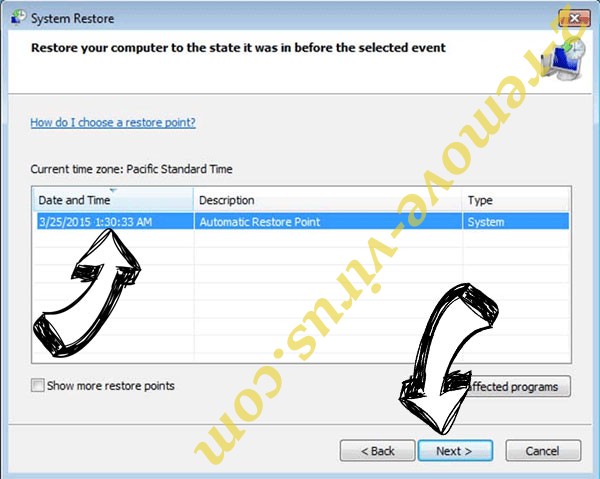
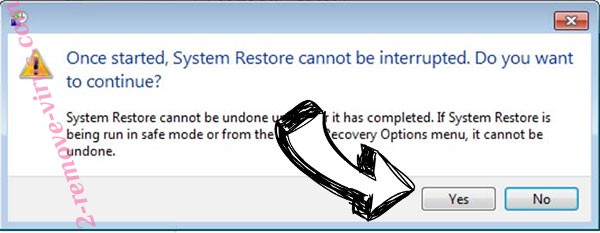
- Click Next again and click Yes to begin the system restore.

Delete COPA ransomware from Windows 8/Windows 10
- Click the Power button on the Windows login screen.
- Press and hold Shift and click Restart.


- Choose Troubleshoot and go to Advanced options.
- Select Command Prompt and click Restart.

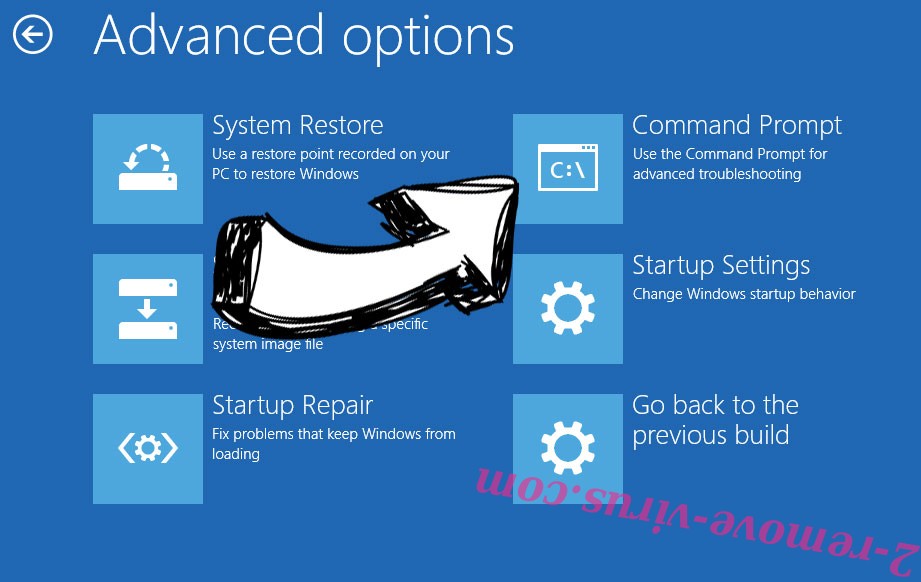
- In Command Prompt, input cd restore and tap Enter.


- Type in rstrui.exe and tap Enter again.


- Click Next in the new System Restore window.

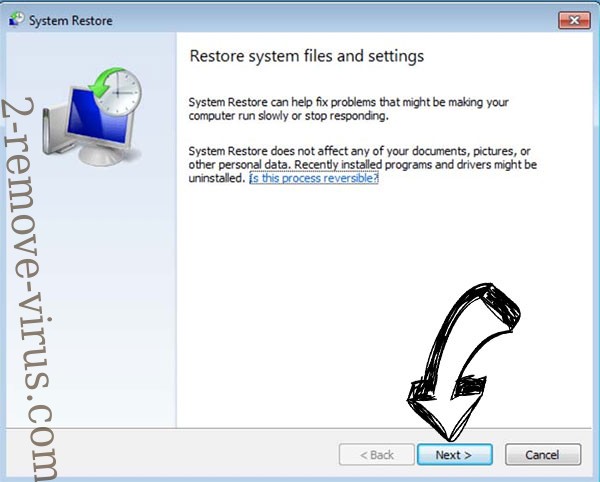
- Choose the restore point prior to the infection.


- Click Next and then click Yes to restore your system.


Site Disclaimer
2-remove-virus.com is not sponsored, owned, affiliated, or linked to malware developers or distributors that are referenced in this article. The article does not promote or endorse any type of malware. We aim at providing useful information that will help computer users to detect and eliminate the unwanted malicious programs from their computers. This can be done manually by following the instructions presented in the article or automatically by implementing the suggested anti-malware tools.
The article is only meant to be used for educational purposes. If you follow the instructions given in the article, you agree to be contracted by the disclaimer. We do not guarantee that the artcile will present you with a solution that removes the malign threats completely. Malware changes constantly, which is why, in some cases, it may be difficult to clean the computer fully by using only the manual removal instructions.
