What is Exploit.poweliks.gen?
Exploit.poweliks.gen is a Trojan infection that can do serious harm to your computer. Usually, users are not aware of Exploit.poweliks.gen being on their computer but there are certain signs that can indicate it. If you have even the slightest suspicion that a Trojan has entered your computer, scan your device with reliable anti-malware software. If it is located, delete Exploit.poweliks.gen immediately. Trojans enter computer via exploit kits and take advantage of vulnerabilities on your computer. It will slow down your computer, prevent your from accessing certain websites and downloading files. If you anti-virus is running, it should immediately alert you of Exploit.poweliks.gen presence. If you do not have such a program, we suggest you get it because having to remove Exploit.poweliks.gen manually is extremely difficult.
What does Exploit.poweliks.gen do?
Exploit.poweliks.gen can enter your computer if you visit a hacked website and have not updated software in a while. Exploit.poweliks.gen will take advantage of vulnerabilities on your computer to install. This is why it’s very important that you regularly update your software and not visit suspicious websites. Adware and browser hijacker can indirectly expose you to dangerous websites, which is why it’s important that get rid of said applications. If you keep all of you programs up-to-date, and not visit weird websites, you should be able to avoid Exploit.poweliks.gen.
If you computer has Exploit.poweliks.gen present, it will slow down and act sluggish. When you check the Task Manager for running programs, you will see some unusual activity and that should be a clear indication that something is wrong. When you use the Internet, you might not be allowed to enter some websites or download files. Exploit.poweliks.gen may get access to Internet and download dangerous malware onto your computer. It could also gain access to your private data and then send it to its creators. If you notice any suspicious activity on your computer, you need to investigate as soon as possible. If Exploit.poweliks.gen is indeed present on your computer, you might end up with even more malicious viruses and end up getting your private data stolen. As soon as your malware scanner locates it, make sure you erase Exploit.poweliks.gen.
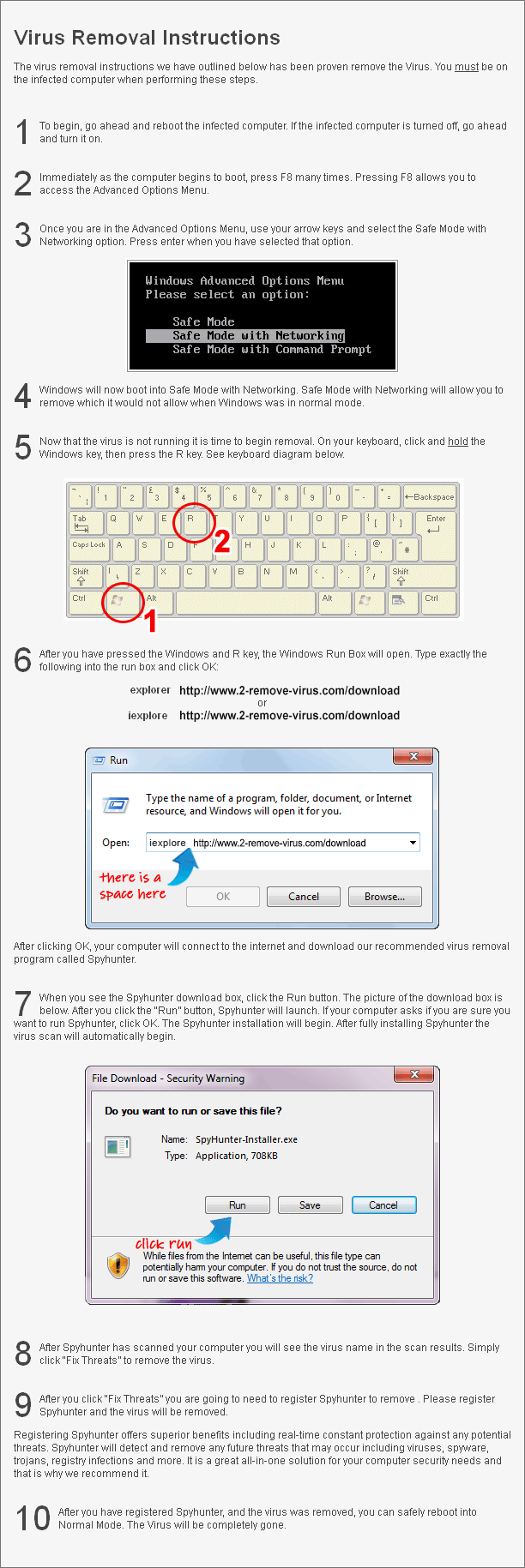
Exploit.poweliks.gen removal
When Exploit.poweliks.gen installed, the installer deletes itself and the Trojan is present only in the Registry. This is why it’s very difficult to spot and uninstall Exploit.poweliks.gen. Manual Exploit.poweliks.gen removal is quite complex for the same reason and can do some damage if done incorrectly. Which is why we cannot recommend you to delete Exploit.poweliks.gen by hand. To safely remove Exploit.poweliks.gen, you should use powerful anti-malware software. Feel free to use the provided guide below this article to fully uninstall Exploit.poweliks.gen.
Offers
Download Removal Toolto scan for Exploit.poweliks.genUse our recommended removal tool to scan for Exploit.poweliks.gen. Trial version of provides detection of computer threats like Exploit.poweliks.gen and assists in its removal for FREE. You can delete detected registry entries, files and processes yourself or purchase a full version.
More information about SpyWarrior and Uninstall Instructions. Please review SpyWarrior EULA and Privacy Policy. SpyWarrior scanner is free. If it detects a malware, purchase its full version to remove it.

WiperSoft Review Details WiperSoft (www.wipersoft.com) is a security tool that provides real-time security from potential threats. Nowadays, many users tend to download free software from the Intern ...
Download|more


Is MacKeeper a virus? MacKeeper is not a virus, nor is it a scam. While there are various opinions about the program on the Internet, a lot of the people who so notoriously hate the program have neve ...
Download|more


While the creators of MalwareBytes anti-malware have not been in this business for long time, they make up for it with their enthusiastic approach. Statistic from such websites like CNET shows that th ...
Download|more

Site Disclaimer
2-remove-virus.com is not sponsored, owned, affiliated, or linked to malware developers or distributors that are referenced in this article. The article does not promote or endorse any type of malware. We aim at providing useful information that will help computer users to detect and eliminate the unwanted malicious programs from their computers. This can be done manually by following the instructions presented in the article or automatically by implementing the suggested anti-malware tools.
The article is only meant to be used for educational purposes. If you follow the instructions given in the article, you agree to be contracted by the disclaimer. We do not guarantee that the artcile will present you with a solution that removes the malign threats completely. Malware changes constantly, which is why, in some cases, it may be difficult to clean the computer fully by using only the manual removal instructions.
