What is J3ster Ransomware
J3ster Ransomware ransomware is classified as dangerous malicious software since if your device gets contaminated with it, you might be facing serious problems. It is possible it is your first time encountering this type of malicious program, in which case, you may be particularly shocked. Data encoding malicious program encodes files using strong encryption algorithms, and once the process is complete, files will be locked and you won’t be able to open them. Because ransomware could mean permanent file loss, it’s classified as a very damaging infection. 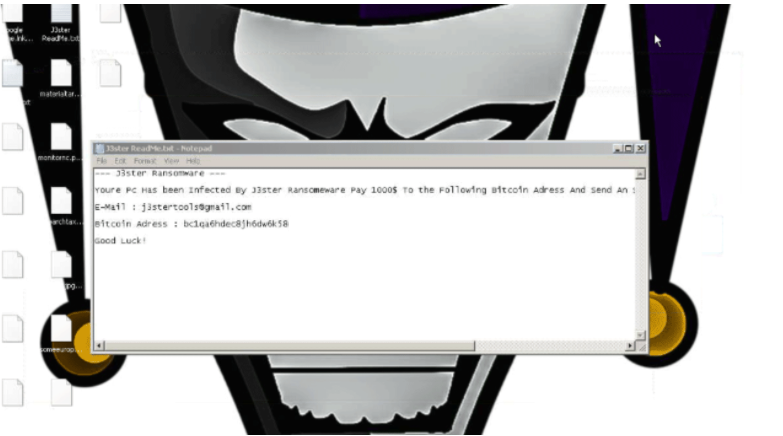
You do have the option of paying the ransom but for various reasons, that isn’t the best choice. Paying does not always guarantee decrypted files, so there’s a possibility that you may just be wasting your money. Consider what is preventing criminals from just taking your money. In addition, by paying you’d be supporting the future projects (more ransomware and malicious program) of these crooks. Do you actually want to support something that does many millions of dollars in damage. People are also becoming more and more attracted to the whole business because the amount of people who pay the ransom make data encoding malware a very profitable business. You may be put into this type of situation again sometime in the future, so investing the demanded money into backup would be a better choice because you wouldn’t need to worry about losing your data. If you had a backup option available, you may just delete J3ster Ransomware and then restore files without being worried about losing them. Details about the most frequent spreads methods will be provided in the below paragraph, if you’re not certain about how the data encoding malicious program even got into your computer.
J3ster Ransomware spread ways
Email attachments, exploit kits and malicious downloads are the distribution methods you need to be cautious about the most. Since plenty of users are not cautious about how they use their email or from where they download, file encrypting malicious program spreaders do not need to think of ways that are more sophisticated. However, some data encrypting malware do use sophisticated methods. Crooks write a somewhat credible email, while pretending to be from some legitimate company or organization, attach the malware to the email and send it to people. Topics about money can often be ran into as people are more prone to opening those emails. Hackers also prefer to pretend to be from Amazon, and alert potential victims that there has been some unusual activity in their account, which would which would make the user less cautious and they’d be more inclined to open the attachment. When you’re dealing with emails, there are certain things to look out for if you want to guard your device. If you are unfamiliar with the sender, look into them. If the sender turns out to be someone you know, do not rush to open the file, first cautiously check the email address. The emails also frequently contain grammar mistakes, which tend to be quite easy to notice. Another big hint could be your name being absent, if, lets say you are an Amazon user and they were to send you an email, they would not use general greetings like Dear Customer/Member/User, and instead would use the name you have given them with. ransomware could also use vulnerabilities in computers to infect. All programs have vulnerabilities but when they’re found, they are normally fixed by vendors so that malware can’t use it to enter a system. As WannaCry has proven, however, not everyone rushes to install those patches. You’re encouraged to regularly update your programs, whenever a patch is released. You can also make patches install automatically.
How does J3ster Ransomware act
A file encoding malware will start looking for certain file types once it installs, and they will be encrypted as soon as they’re identified. Initially, it might not be obvious as to what’s going on, but when your files can not be opened as normal, it ought to become clear. You’ll also see a strange extension added to all files, which helps people identify which data encrypting malware exactly has infected their device. Strong encryption algorithms might have been used to encode your files, and there is a likelihood that they may be encoded permanently. A ransom note will describe what has happened to your files. The method they suggest involves you paying for their decryption program. The note should show the price for a decryptor but if that’s not the case, you’d have to contact criminals via their provided email address to find out how much you’d have to pay. Clearly, we do not believe paying is a wise choice, for the reasons already mentioned. Only think about paying when everything else fails. Maybe you’ve simply forgotten that you have made copies of your files. A free decryption software might also be an option. If a malware specialist is capable of cracking the file encoding malware, he/she may release a free decryption software. Consider that before you even think about complying with the requests. A wiser purchase would be backup. And if backup is available, you can restore data from there after you terminate J3ster Ransomware virus, if it is still on your system. Become familiar with how ransomware spreads so that you can dodge it in the future. Stick to secure websites when it comes to downloads, be cautious of email attachments you open, and keep your programs updated.
How to erase J3ster Ransomware virus
a malware removal tool will be a necessary program to have if you want to fully get rid of the file encrypting malicious software in case it is still present on your computer. When trying to manually fix J3ster Ransomware virus you might cause further damage if you aren’t the most computer-savvy person. Therefore, pick the automatic way. These kinds of programs exist for the purpose of getting rid of these kinds of infections, depending on the program, even stopping them from infecting in the first place. Choose and install a trustworthy program, scan your computer for the the infection. However, the tool is not capable of restoring files, so do not expect your files to be restored once the infection has been terminated. If the file encrypting malware has been terminated fully, recover files from backup, and if you do not have it, start using it.
Offers
Download Removal Toolto scan for J3ster RansomwareUse our recommended removal tool to scan for J3ster Ransomware. Trial version of provides detection of computer threats like J3ster Ransomware and assists in its removal for FREE. You can delete detected registry entries, files and processes yourself or purchase a full version.
More information about SpyWarrior and Uninstall Instructions. Please review SpyWarrior EULA and Privacy Policy. SpyWarrior scanner is free. If it detects a malware, purchase its full version to remove it.

WiperSoft Review Details WiperSoft (www.wipersoft.com) is a security tool that provides real-time security from potential threats. Nowadays, many users tend to download free software from the Intern ...
Download|more


Is MacKeeper a virus? MacKeeper is not a virus, nor is it a scam. While there are various opinions about the program on the Internet, a lot of the people who so notoriously hate the program have neve ...
Download|more


While the creators of MalwareBytes anti-malware have not been in this business for long time, they make up for it with their enthusiastic approach. Statistic from such websites like CNET shows that th ...
Download|more
Quick Menu
Step 1. Delete J3ster Ransomware using Safe Mode with Networking.
Remove J3ster Ransomware from Windows 7/Windows Vista/Windows XP
- Click on Start and select Shutdown.
- Choose Restart and click OK.

- Start tapping F8 when your PC starts loading.
- Under Advanced Boot Options, choose Safe Mode with Networking.

- Open your browser and download the anti-malware utility.
- Use the utility to remove J3ster Ransomware
Remove J3ster Ransomware from Windows 8/Windows 10
- On the Windows login screen, press the Power button.
- Tap and hold Shift and select Restart.

- Go to Troubleshoot → Advanced options → Start Settings.
- Choose Enable Safe Mode or Safe Mode with Networking under Startup Settings.

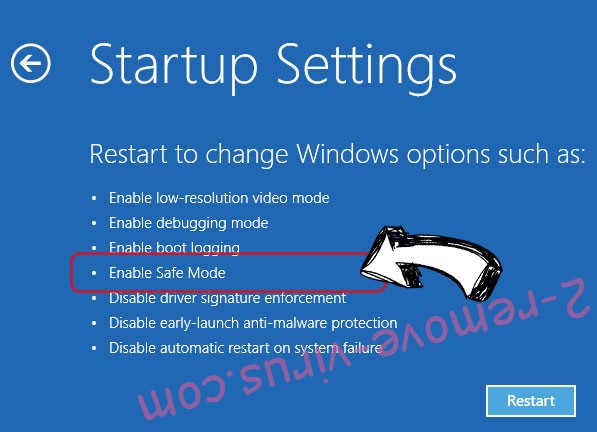
- Click Restart.
- Open your web browser and download the malware remover.
- Use the software to delete J3ster Ransomware
Step 2. Restore Your Files using System Restore
Delete J3ster Ransomware from Windows 7/Windows Vista/Windows XP
- Click Start and choose Shutdown.
- Select Restart and OK


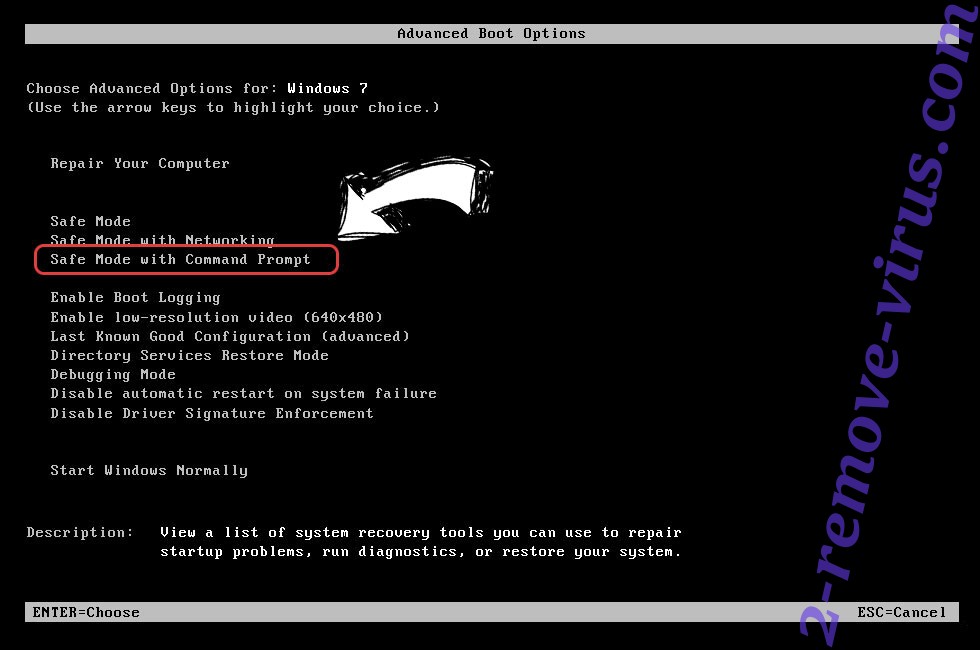
- When your PC starts loading, press F8 repeatedly to open Advanced Boot Options
- Choose Command Prompt from the list.

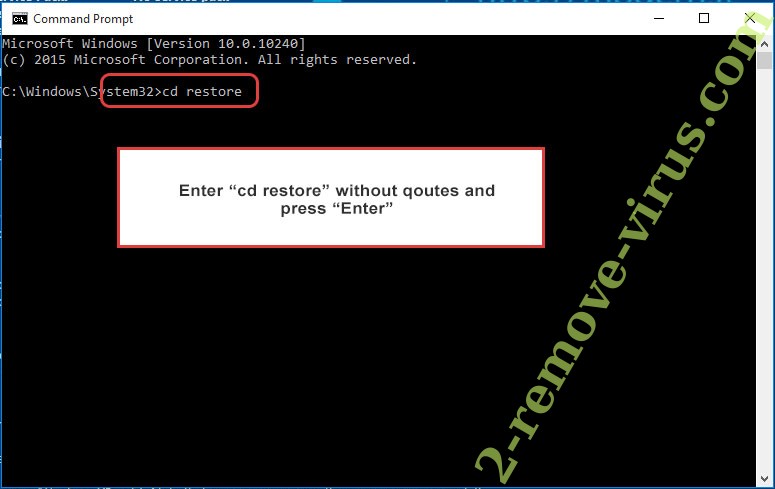
- Type in cd restore and tap Enter.

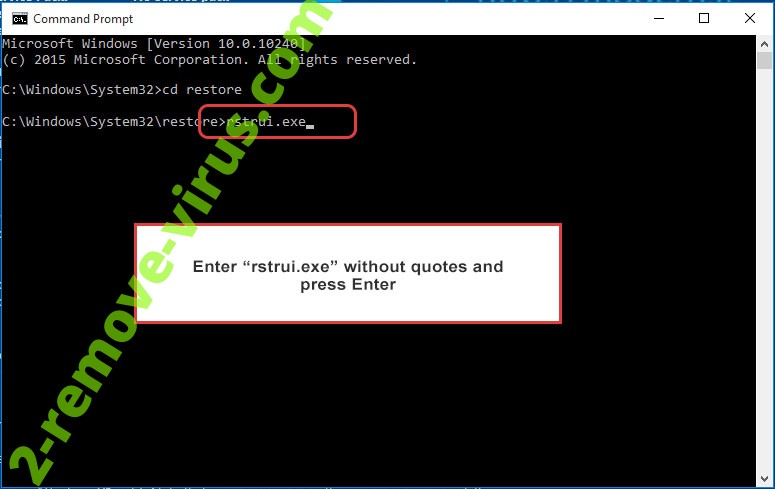
- Type in rstrui.exe and press Enter.

- Click Next in the new window and select the restore point prior to the infection.

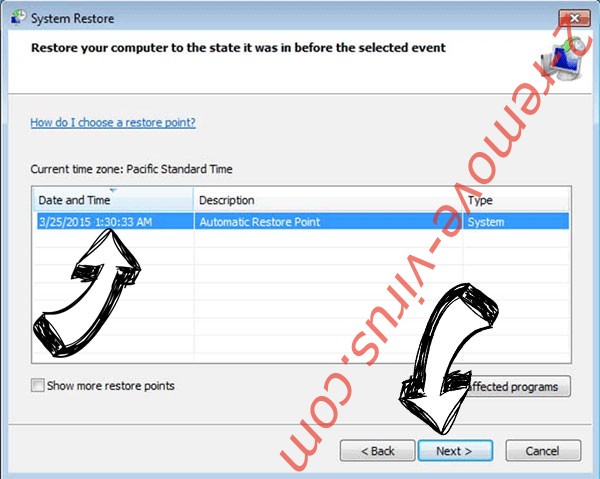
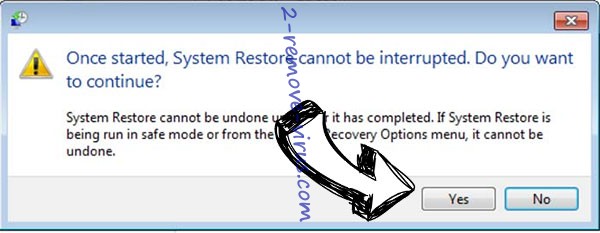
- Click Next again and click Yes to begin the system restore.

Delete J3ster Ransomware from Windows 8/Windows 10
- Click the Power button on the Windows login screen.
- Press and hold Shift and click Restart.


- Choose Troubleshoot and go to Advanced options.
- Select Command Prompt and click Restart.

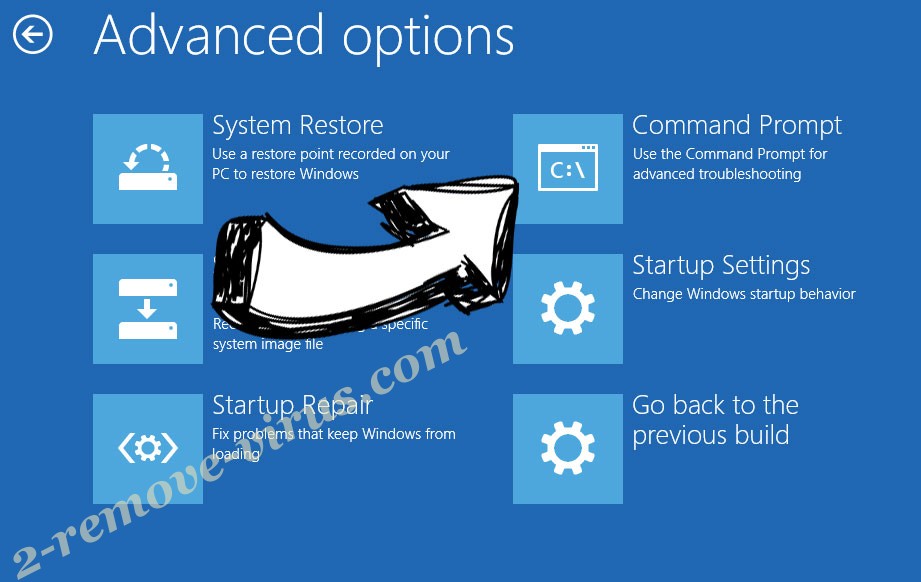
- In Command Prompt, input cd restore and tap Enter.


- Type in rstrui.exe and tap Enter again.


- Click Next in the new System Restore window.

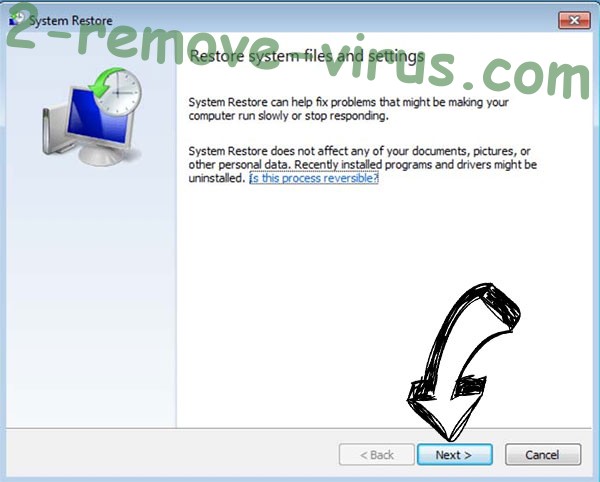
- Choose the restore point prior to the infection.


- Click Next and then click Yes to restore your system.


Site Disclaimer
2-remove-virus.com is not sponsored, owned, affiliated, or linked to malware developers or distributors that are referenced in this article. The article does not promote or endorse any type of malware. We aim at providing useful information that will help computer users to detect and eliminate the unwanted malicious programs from their computers. This can be done manually by following the instructions presented in the article or automatically by implementing the suggested anti-malware tools.
The article is only meant to be used for educational purposes. If you follow the instructions given in the article, you agree to be contracted by the disclaimer. We do not guarantee that the artcile will present you with a solution that removes the malign threats completely. Malware changes constantly, which is why, in some cases, it may be difficult to clean the computer fully by using only the manual removal instructions.
