What is Retadup Trojan virus
Retadup Trojan ransomware is dangerous malware since if your computer gets it, you might be facing serious issues. It’s likely you have never come across this kind of malicious program before, in which case, you may be especially surprised. Ransomware uses strong encryption algorithms to encrypt files, and once they are locked, your access to them will be prevented. Because file decryption is not possible in all cases, not to mention the time and effort it takes to return everything back to normal, ransomware is considered to be one of the most dangerous malware out there. 
There’s also the option of paying the ransom but for various reasons, that isn’t the best choice. There are countless cases where files weren’t decrypted even after victims comply with the demands. Keep in mind who you’re dealing with, and don’t expect crooks to feel obligated to help you with your data when they can just take your money. Furthermore, that money would go into supporting their future malware projects. It’s already supposed that ransomware did $5 billion worth of damage to businesses in 2017, and that’s an estimation only. The more victims pay, the more profitable it becomes, thus drawing more crooks who are lured by easy money. Buying backup with the demanded money would be a much better choice because if you are ever put in this kind of situation again, you would not need to worry about file loss because you could just recover them from backup. You could then just remove Retadup Trojan and recover files. You may find details on the most frequent distribution ways in the following paragraph, if you’re not sure about how the ransomware even got into your computer.
How did you acquire the ransomware
A file encoding malicious program infection could happen pretty easily, commonly using such methods as adding malware-ridden files to emails, taking advantage of vulnerabilities in computer software and hosting infected files on suspicious download platforms. A lot of data encrypting malicious programs depend on people hastily opening email attachments and don’t have to use more elaborate methods. That isn’t to say more sophisticated methods aren’t popular, however. Crooks don’t need to do much, just write a generic email that less cautious users may fall for, attach the contaminated file to the email and send it to possible victims, who might believe the sender is someone trustworthy. Money related issues are a frequent topic in those emails since users tend to take them seriously and are more inclined to engage in. And if someone like Amazon was to email a user about dubious activity in their account or a purchase, the account owner would be much more likely to open the attachment. When you’re dealing with emails, there are certain things to look out for if you wish to secure your device. It’s critical that you check the sender to see whether they are familiar to you and therefore could be trusted. If you do know them, make sure it’s actually them by cautiously checking the email address. Also, be on the look out for grammatical errors, which can be pretty obvious. Take note of how the sender addresses you, if it’s a sender who knows your name, they will always greet you by your name, instead of a typical Customer or Member. Some data encrypting malware could also use unpatched programs on your computer to enter. All software have weak spots but when they are discovered, they’re usually fixed by software authors so that malware can’t take advantage of it to infect. Nevertheless, as world wide ransomware attacks have shown, not everyone installs those updates. You’re suggested to install an update whenever it is made available. Updates can also be allowed to install automatically.
What can you do about your data
Ransomware only targets specif files, and when they are found, they’re encoded almost immediately. You will not be able to open your files, so even if you don’t notice the encryption process, you’ll know something is not right eventually. Look for weird file extensions added to files, they they’ll help recognize the data encoding malware. Unfortunately, file restoring may be impossible if the file encrypting malware used a powerful encryption algorithm. A ransom note will explain that your data has been encrypted and to go about to decrypt them. What criminals will suggest you do is buy their paid decryptor, and warn that you could harm your files if another method was used. The note ought to clearly display the price for the decryptor but if it does not, it will give you an email address to contact the crooks to set up a price. For the reasons we have already discussed, we do not encourage paying the ransom. Carefully consider all other alternatives, before even considering giving into the demands. Maybe you’ve stored your files somewhere but simply forgotten about it. There is also some probability that a free decryption utility has been released. If the file encoding malware is decryptable, someone might be able to release a tool that would unlock Retadup Trojan files for free. Before you make a decision to pay, look into a decryption utility. It would be a better idea to purchase backup with some of that money. If your most important files are stored somewhere, you just uninstall Retadup Trojan virus and then proceed to data restoring. Become familiar with how a data encoding malicious software is spread so that you can dodge it in the future. At the very least, stop opening email attachments left and right, update your software, and only download from sources you know you can trust.
Retadup Trojan removal
an anti-malware program will be necessary if you wish the ransomware to be gone fully. To manually fix Retadup Trojan virus is no easy process and may lead to additional harm to your system. If you go with the automatic option, it would be a smarter choice. This software is useful to have on the device because it will not only make sure to get rid of this infection but also stopping one from getting in in the future. Find which malware removal tool is most suitable for you, install it and scan your system to identify the threat. The utility isn’t capable of recovering your data, however. After the threat is gone, make sure you get backup and regularly backup all essential data.
Offers
Download Removal Toolto scan for RetadupUse our recommended removal tool to scan for Retadup. Trial version of provides detection of computer threats like Retadup and assists in its removal for FREE. You can delete detected registry entries, files and processes yourself or purchase a full version.
More information about SpyWarrior and Uninstall Instructions. Please review SpyWarrior EULA and Privacy Policy. SpyWarrior scanner is free. If it detects a malware, purchase its full version to remove it.

WiperSoft Review Details WiperSoft (www.wipersoft.com) is a security tool that provides real-time security from potential threats. Nowadays, many users tend to download free software from the Intern ...
Download|more


Is MacKeeper a virus? MacKeeper is not a virus, nor is it a scam. While there are various opinions about the program on the Internet, a lot of the people who so notoriously hate the program have neve ...
Download|more


While the creators of MalwareBytes anti-malware have not been in this business for long time, they make up for it with their enthusiastic approach. Statistic from such websites like CNET shows that th ...
Download|more
Quick Menu
Step 1. Delete Retadup using Safe Mode with Networking.
Remove Retadup from Windows 7/Windows Vista/Windows XP
- Click on Start and select Shutdown.
- Choose Restart and click OK.

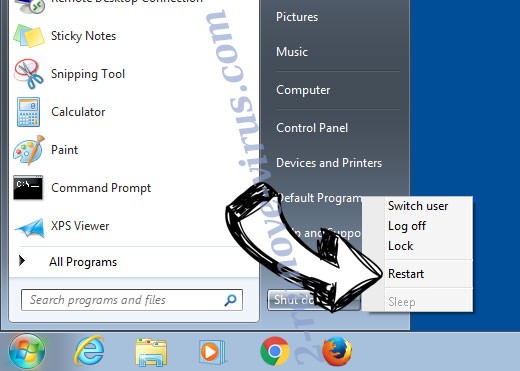
- Start tapping F8 when your PC starts loading.
- Under Advanced Boot Options, choose Safe Mode with Networking.

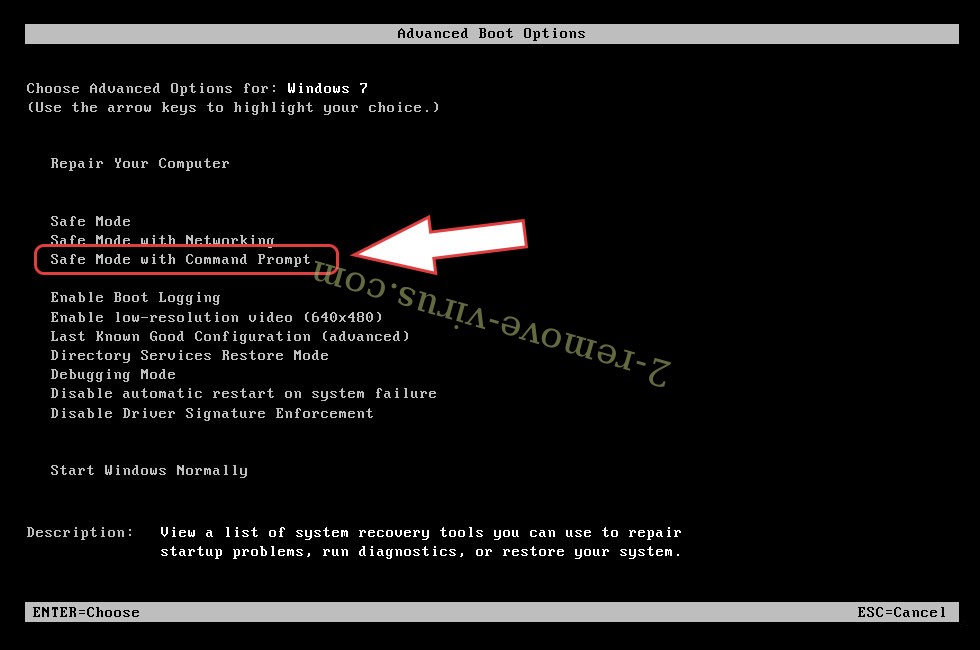
- Open your browser and download the anti-malware utility.
- Use the utility to remove Retadup
Remove Retadup from Windows 8/Windows 10
- On the Windows login screen, press the Power button.
- Tap and hold Shift and select Restart.

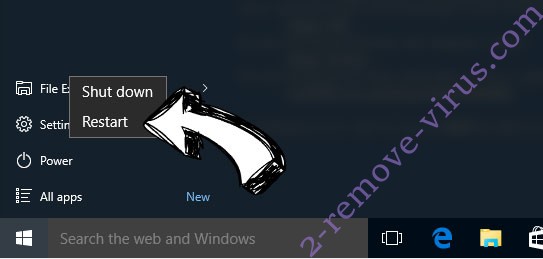
- Go to Troubleshoot → Advanced options → Start Settings.
- Choose Enable Safe Mode or Safe Mode with Networking under Startup Settings.

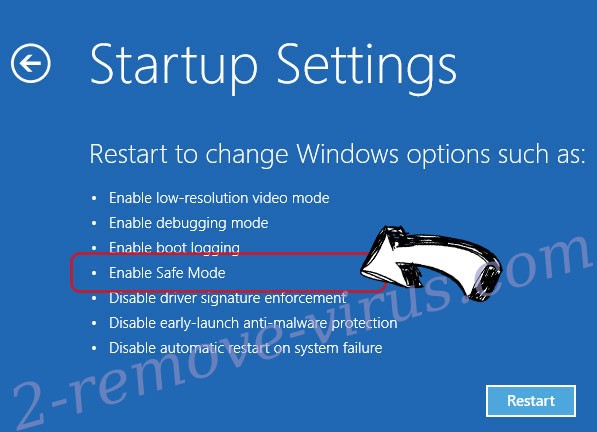
- Click Restart.
- Open your web browser and download the malware remover.
- Use the software to delete Retadup
Step 2. Restore Your Files using System Restore
Delete Retadup from Windows 7/Windows Vista/Windows XP
- Click Start and choose Shutdown.
- Select Restart and OK


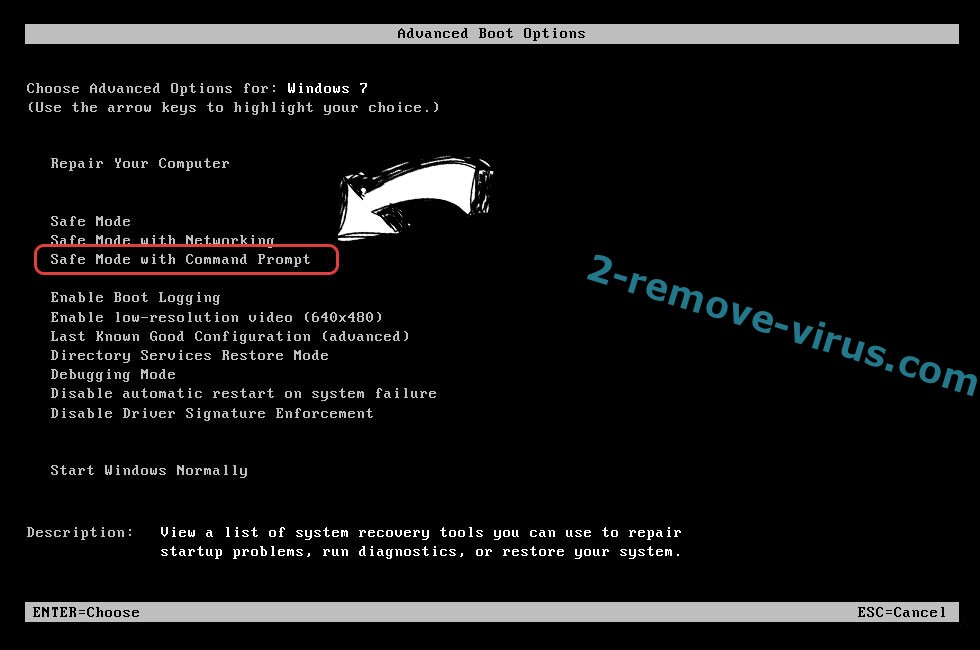
- When your PC starts loading, press F8 repeatedly to open Advanced Boot Options
- Choose Command Prompt from the list.

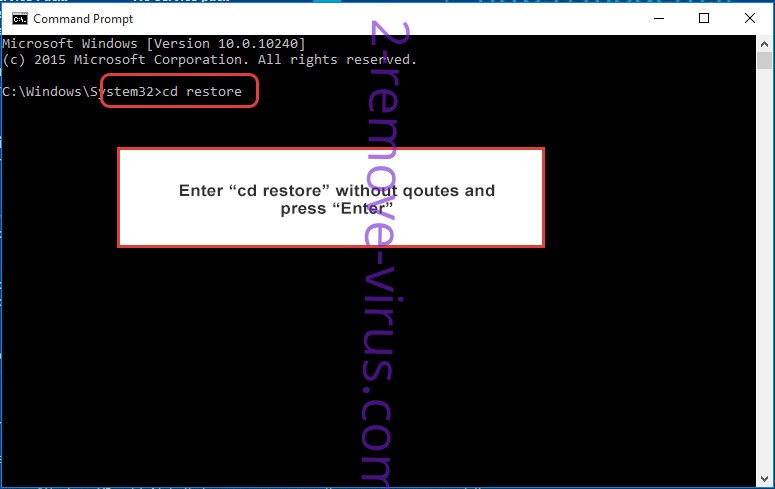
- Type in cd restore and tap Enter.

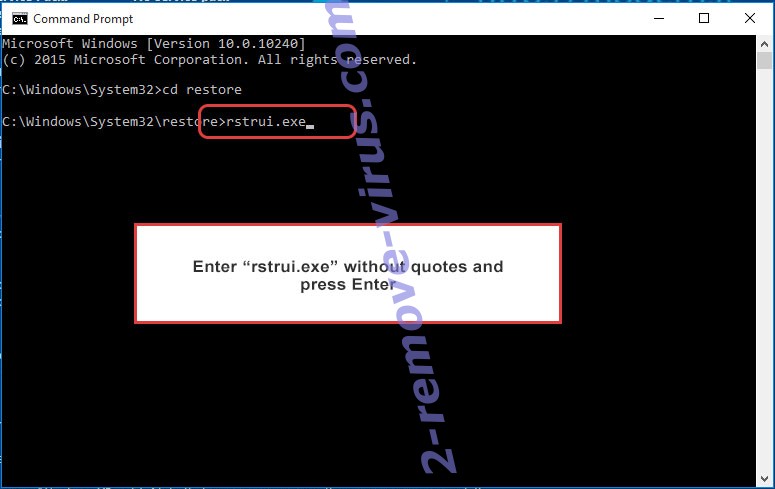
- Type in rstrui.exe and press Enter.

- Click Next in the new window and select the restore point prior to the infection.

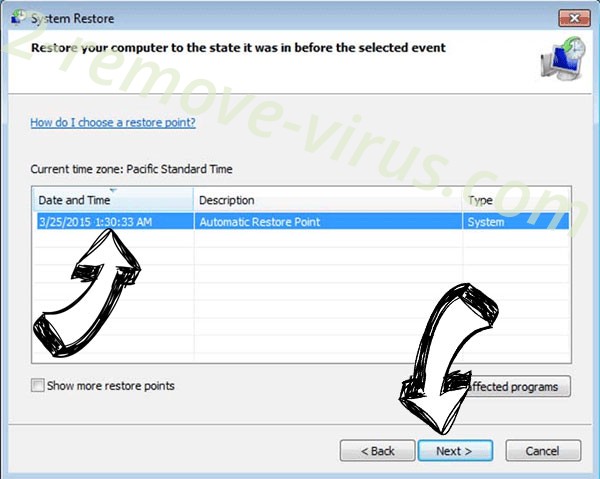
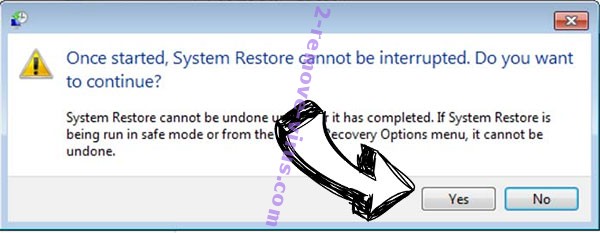
- Click Next again and click Yes to begin the system restore.

Delete Retadup from Windows 8/Windows 10
- Click the Power button on the Windows login screen.
- Press and hold Shift and click Restart.


- Choose Troubleshoot and go to Advanced options.
- Select Command Prompt and click Restart.

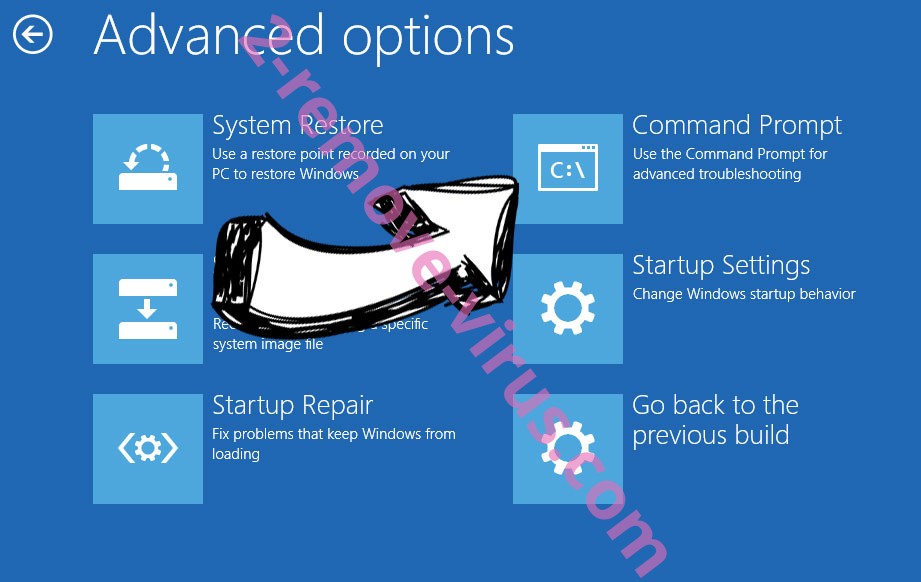
- In Command Prompt, input cd restore and tap Enter.


- Type in rstrui.exe and tap Enter again.


- Click Next in the new System Restore window.

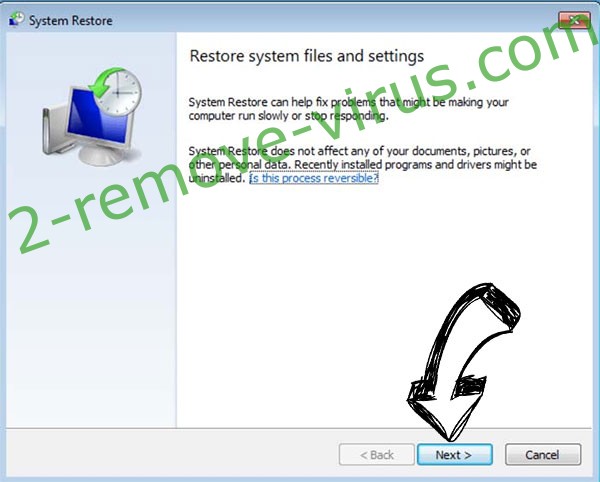
- Choose the restore point prior to the infection.


- Click Next and then click Yes to restore your system.


Site Disclaimer
2-remove-virus.com is not sponsored, owned, affiliated, or linked to malware developers or distributors that are referenced in this article. The article does not promote or endorse any type of malware. We aim at providing useful information that will help computer users to detect and eliminate the unwanted malicious programs from their computers. This can be done manually by following the instructions presented in the article or automatically by implementing the suggested anti-malware tools.
The article is only meant to be used for educational purposes. If you follow the instructions given in the article, you agree to be contracted by the disclaimer. We do not guarantee that the artcile will present you with a solution that removes the malign threats completely. Malware changes constantly, which is why, in some cases, it may be difficult to clean the computer fully by using only the manual removal instructions.
