What is TeslaCrypt Virus?
TeslaCrypt Virus is classified as a ransomware infection, which is aimed at extorting money from you. It spreads online through spam emails, corrupted links, fake ads, unsafe websites, and so on. It functions in a similar manner to other malicious programs of this type like Cryptolocker, CryptoWall, Chimera Ransomware, CTB-Locker, and more. Once in the system, TeslaCrypt Virus starts encrypting your data. After it completes this process, it demands that you pay a ransom for your files. We advise against doing so. You should delete TeslaCrypt Virus from your computer as soon as you can.
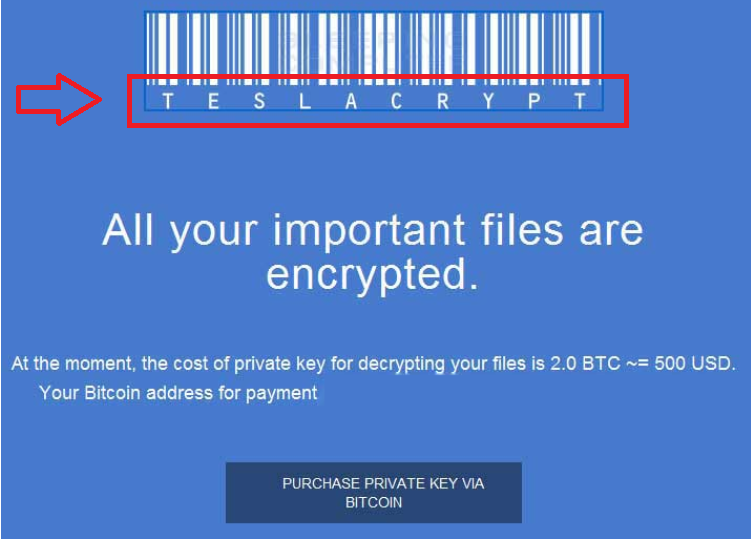
How does TeslaCrypt Virus work?
TeslaCrypt Virus can corrupt your documents, photos, game files, videos, and so on. It uses the AES encryption algorithm. All encrypted files have the .ccc, .vvv, .xxx, .mp3, .micro, or a similar extension added to them. The ransomware also creates files named _H_e_l_p_RECOVER_INSTRUCTIONS in the following formats: PNG, TXT, and HTML. These files contain instructions on how to decrypt your data. The cyber crooks claim that the only way to regain access to your files is by purchasing a private key and a decrypt program from them. They present you with several payment options including PayPal My Cash Cards and Bitcoins.
We urge you not to follow any of the instructions that are provided to you by the cyber criminals. First of all, there are no guarantees that they will follow through on their promises, so you could simply waste your money and get nothing in return. Secondly, there are other ways to restore your data without making the ransom payment. You can use backup (if you have one) or you can download a file-decryption tool created specifically for this threat. Before you do that, however, you need to make sure that you eliminate TeslaCrypt Virus from your PC completely.
How to remove TeslaCrypt Virus?
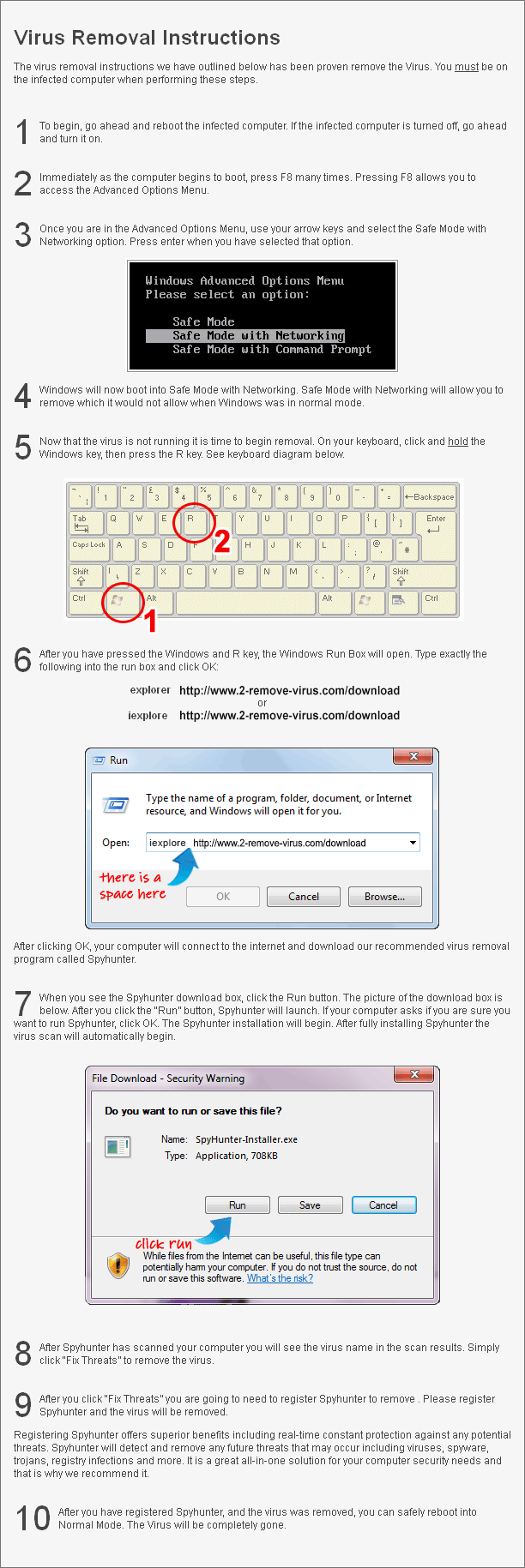
The only way to safely terminate TeslaCrypt Virus is by implementing a powerful anti-malware utility. You can download the security tool from our page and use it to scan your system. It will detect all malicious components of the ransomware as well as other threats that you may have in your system. The remover will erase TeslaCrypt Virus completely. It will also stay useful in the future by shielding your computer from various online infections, so you do not have to deal with similar issues again. Before you can download the anti-malware and remove TeslaCrypt Virus from your computer, you will have to restart it in Safe Mode with Networking. In case you are not sure how to do that, you can follow the instructions presented below the article. Once you reboot your system and acquire the security application, you will be able to get rid of TeslaCrypt Virus without any problems.
Offers
Download Removal Toolto scan for TeslaCrypt VirusUse our recommended removal tool to scan for TeslaCrypt Virus. Trial version of provides detection of computer threats like TeslaCrypt Virus and assists in its removal for FREE. You can delete detected registry entries, files and processes yourself or purchase a full version.
More information about SpyWarrior and Uninstall Instructions. Please review SpyWarrior EULA and Privacy Policy. SpyWarrior scanner is free. If it detects a malware, purchase its full version to remove it.

WiperSoft Review Details WiperSoft (www.wipersoft.com) is a security tool that provides real-time security from potential threats. Nowadays, many users tend to download free software from the Intern ...
Download|more


Is MacKeeper a virus? MacKeeper is not a virus, nor is it a scam. While there are various opinions about the program on the Internet, a lot of the people who so notoriously hate the program have neve ...
Download|more


While the creators of MalwareBytes anti-malware have not been in this business for long time, they make up for it with their enthusiastic approach. Statistic from such websites like CNET shows that th ...
Download|more

Site Disclaimer
2-remove-virus.com is not sponsored, owned, affiliated, or linked to malware developers or distributors that are referenced in this article. The article does not promote or endorse any type of malware. We aim at providing useful information that will help computer users to detect and eliminate the unwanted malicious programs from their computers. This can be done manually by following the instructions presented in the article or automatically by implementing the suggested anti-malware tools.
The article is only meant to be used for educational purposes. If you follow the instructions given in the article, you agree to be contracted by the disclaimer. We do not guarantee that the artcile will present you with a solution that removes the malign threats completely. Malware changes constantly, which is why, in some cases, it may be difficult to clean the computer fully by using only the manual removal instructions.
