Brook malware is a remote administration trojan (RAT). It’s a very dangerous infection that can stay stealthily in the background while performing its malicious activities. Its malicious activities are mostly to do with stealing information, such as login credentials. It may also target users’ cryptocurrencies.
Brook malware has several functions, all of which are very dangerous. What’s worse is that it’s a stealthy infection so it will try to avoid detection and being noticed by users. Users without an anti-malware program may not even notice the infection because it works in the background.
One of Brook malware ‘s features is keylogging. It will log keystrokes in order to steal information like passwords, credit card details, personal information, etc. This is very dangerous because stolen login credentials could lead to account hijacking. And stolen credit card details could lead to serious financial losses.
Brook malware can also access and copy clipboard data, which allows it to intercept information users copy to the clipboard (e.g. passwords). It can also replace clipboard contents, which is a very dangerous feature. This feature can allow the trojan operators to steal users’ cryptocurrencies. When users try to make a transaction from their crypto wallet, they often copy the recipient’s wallet address. Trojan operators can replace the recipient’s address with their own wallet address, redirecting a transaction to their account. Not many users double-check the recipient’s wallet address after pasting it because they do not think there’s any need to do that.
Interestingly enough, Brook malware will detect virtual machine environments and debugging tools in order to avoid analysis. This makes it difficult for anti-virus programs to effectively deal with Brook malware .
Brook malware is a stealthy trojan, which means it will not show any obvious signs of being present. The longer it can stay undetected, the more information it can steal and the more damage it can do. There are some signs that could help identify the trojan but having a good anti-malware program active on a computer is a much better defence. Nonetheless, users should be aware of the signs.
When malware, specifically a trojan, is present, there’s usually unexplained computer slowdown, programs crashing, and Internet connectivity issues. There would also be unknown processes in Task Manager, usually using up a lot of computer resources.
How does Brook malware enter users’ computers?
Trojans and other malware that target random users are spread via torrents, malicious ads/redirects, as well as email attachments. Users who have good online habits tend to encounter malware significantly less because they do not engage in risky online behavior. Developing better online habits can go a long way toward avoiding malware.
Torrents are a very common way users pick up a malicious infection. The large majority of torrent sites are poorly moderated and are full of malicious torrents. Unsuspecting users who do not know what malware in a torrent looks like end up downloading those torrents. Malware is particularly common in torrents for entertainment content, including movies, TV series, and video games. This, in addition to torrenting copyrighted content being content theft, is why using torrents to obtain content for free is not recommended.
It’s also common to pick up malware from email attachments. Malicious actors attach a malicious file to an email, and when users open the attachment, the malware can initiate. Generic emails carrying malware are usually quite obvious. The biggest giveaway is often grammar/spelling mistakes. Senders pretend to be from legitimate companies, supposedly emailing with important business. They often claim that the file attached to the email is an important document that needs to be urgently reviewed. But when such emails are full of grammar/spelling mistakes, it becomes quite obvious that the email is fake.
Another thing that can often give away a malicious email is how it addresses users. Senders pretend to be from companies whose services users use but use generic words like User, Member, Customer, etc., to address users. Legitimate emails would address users by name but because malicious emails target many users at the same time, they use generic words.
Some malicious emails may be more sophisticated and difficult to identify as malicious. Thus, users should always scan all unsolicited email attachments with anti-virus software or VirusTota , before opening them. This will ensure that nothing malicious will be opened.
Brook malware removal
Stealthy trojans like Brook malware can remain undetected for a long time unless anti-malware is installed on the computer. All good anti-malware programs will detect and remove Brook malware . However, if the trojan was found on your computer, the trouble does not end with its removal.
Brook malware is a stealer trojan, which means it could have stolen sensitive information, such as passwords. Once your computer is malware-free, you need to change the passwords for all accounts you accessed recently.
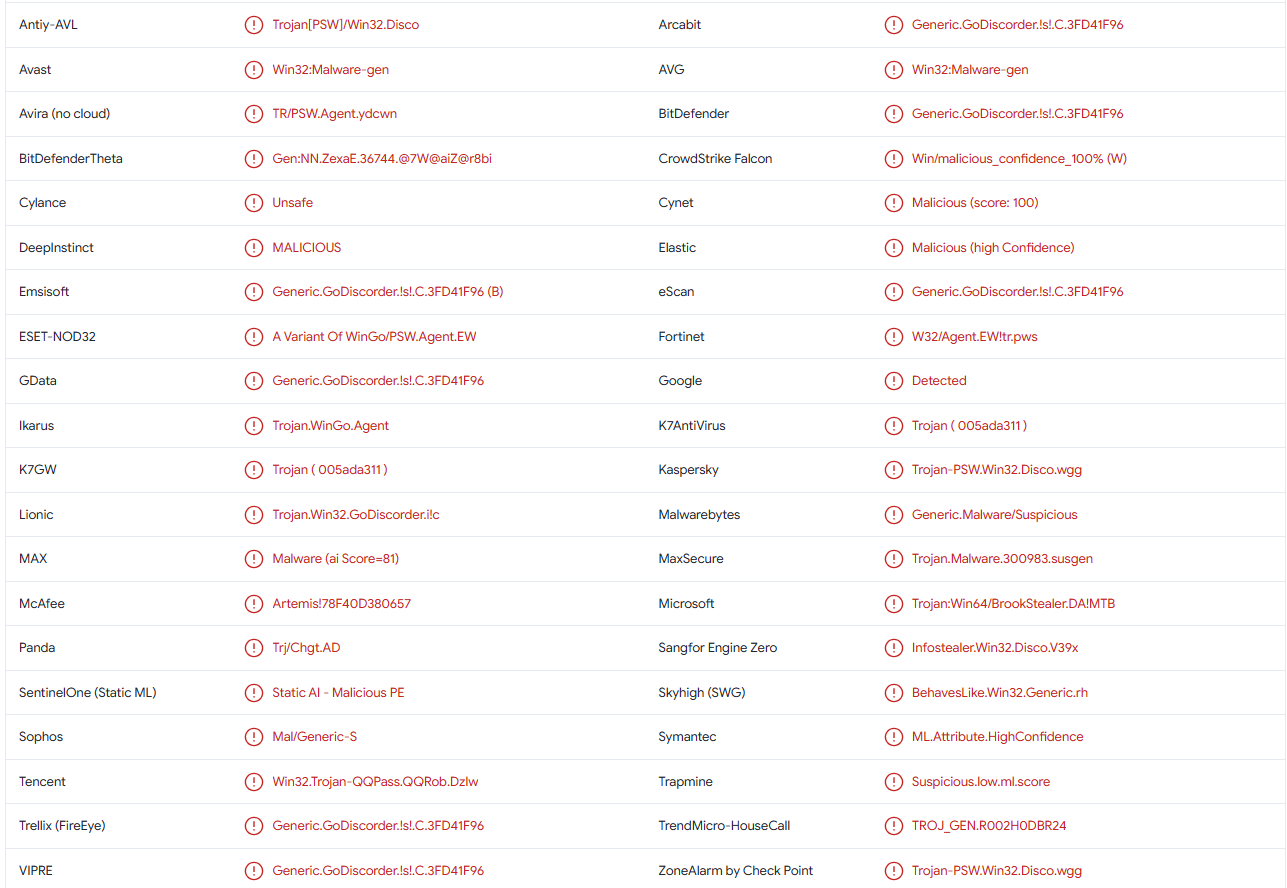
Brook malware is detected as:
- Win32:Malware-gen by Avast/AVG
- A Variant Of WinGo/PSW. Agent.EW by ESET
- Generic.GoDiscorder.! s!. C.3FD41F96 by BitDefender
- Trojan-PSW.Win32.Disco.wgg by Kaspersky
- Generic.Malware/Suspicious by Malwarebytes
- Trojan:Win64/BrookStealer.DA! MTB by Microsoft
Incoming search terms:
Site Disclaimer
2-remove-virus.com is not sponsored, owned, affiliated, or linked to malware developers or distributors that are referenced in this article. The article does not promote or endorse any type of malware. We aim at providing useful information that will help computer users to detect and eliminate the unwanted malicious programs from their computers. This can be done manually by following the instructions presented in the article or automatically by implementing the suggested anti-malware tools.
The article is only meant to be used for educational purposes. If you follow the instructions given in the article, you agree to be contracted by the disclaimer. We do not guarantee that the artcile will present you with a solution that removes the malign threats completely. Malware changes constantly, which is why, in some cases, it may be difficult to clean the computer fully by using only the manual removal instructions.