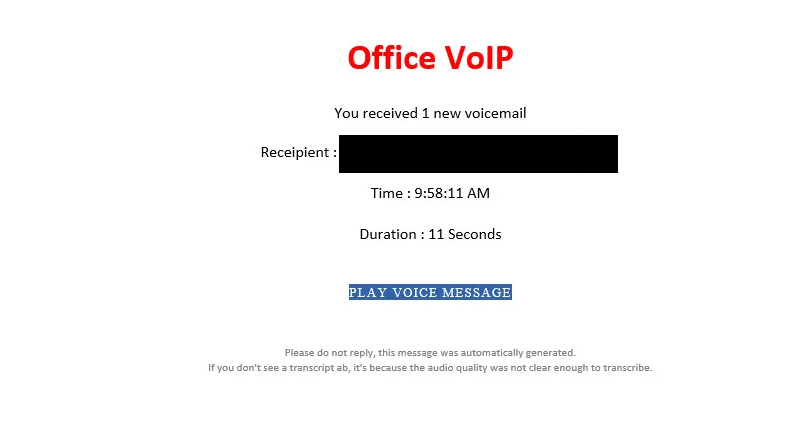
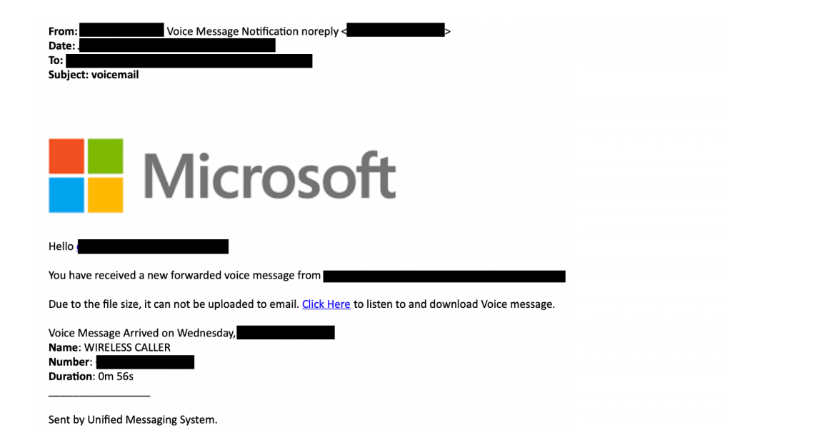
Voicemail email scam refers to a phishing email that claims you have received a new voicemail. Such deceptive emails aim to peak users’ curiosity enough to click on a link or an email attachment. There are various malicious campaigns that are disguised to look like voicemail notifications so it’s difficult to say what a particular email may be concealing. If it’s a phishing attempt, it will likely try to phish email login credentials. If it’s an attachment, opening it would likely result in a malicious infection.
Voicemail email scams falsely claim that you have a new voicemail. They’re usually very simple emails that contain very little information, only the date the voicemail was supposedly received, as well as the length of the message. The emails also contain either a link or a file attachment.
Voicemail email scams that have links are generally phishing attempts. Depending on which scam campaign you’re dealing with, you would be taken to a fake login page if you click on the link. In most cases, the phishing login pages are for Gmail, Outlook, Yahoo, and Microsoft. If you type in your login credentials on such phishing pages, they would be transferred to malicious actors operating the scam. From there on, your credentials would likely be sold on hacker forums for other malicious actors to purchase.
Phishing campaigns like voicemail email scams usually target email login credentials, such as Gmail, and Outlook, as well as accounts like Microsoft. Certain accounts are a hot commodity, email accounts in particular. Gaining access to an email account can allow someone to access all connected accounts. All a malicious actor would need to do is reset the password for an account and then change it via the hijacked email. This is why email accounts are so sought after.
If a voicemail scam email has an attachment, it’s likely malware. Different malicious emails distribute different malware so it’s difficult to say what you’d end up with. Opening the malicious email attachment would initiate the malware. Some malware infections may be more obvious than others. If you initiate a ransomware infection, it would proceed to encrypt your files. If you were to initiate a trojan, it may stay hidden to perform its malicious activities (e.g. steal passwords). This is why it’s important to have a good anti-virus program monitor your computer at all times.
How to recognize a phishing attempt
It’s generally not difficult to identify generic phishing and malicious emails because they target a large number of users and thus have no personal details. If you know what to look for, you should be able to notice when an email is trying to phish you.
One of the most obvious indications that an email may be malicious is grammar and spelling mistakes. In most cases, malicious actors have very poor English language skills and either make a lot of mistakes or use translation tools like Google Translate. Grammar mistakes and awkward phrasing in emails that are supposed to be sent by companies like Microsoft, Google, etc., look very out of place so it’s pretty obvious that the email may be malicious.
How an email addresses you can also say a lot about whether it’s malicious or safe. When a company whose services you use sends you an email, it will always address you by name. For example, if you use the streaming service Netflix, all emails from it will address you by the main profile’s name. If an email from someone who should know your name addresses you using generic words like User, Member, or Customer, it’s likely a malicious or phishing email.
The sender’s email address can also help determine whether the email is legitimate. That is one of the first things you should check when you receive an unsolicited email that asks you to do something (e.g. open an attachment or click on a link). If the email address looks random, you could very well be dealing with a spam/malicious email. Even if an email looks legitimate, we still recommend looking into whether it actually belongs to whomever the sender claims to be. You can usually use a search engine like Google for that.
It’s generally not recommended to click on any links in emails. If you get an email explaining that there’s some kind of issue with your account, log in to the account manually instead of clicking on a link. You can also hover over the link with your mouse and the URL should appear.
Lastly, we caution you to always check the site’s URL before logging in anywhere. Keep in mind that malicious actors can make their phishing websites look practically identical to their legitimate counterparts. But the URL will always give it away. Carefully inspect the URL for any inaccuracies and only then type in your credentials.
Remove Voicemail email scam
If you receive an email that informs you about a voicemail but you do not have a voicemail to email service, you can just delete the email because it’s likely malicious. If you have clicked on one of the links and typed in your login credentials in what you now realize was a phishing site, you need to change your credentials immediately. If you can still access the account whose logins were phished, change the password immediately. if you can no longer access it, try contacting the provider to see whether it’s possible to somehow get your account back. In the meantime, you need to access all accounts that are connected to your hijacked email account and change the email addresses, as well as the passwords immediately. Hijacking an email account can allow malicious actors to access other connected accounts so it’s very important that you secure them before that could happen.
It’s also essential that you set up two-factor authentication (2FA) for all accounts, especially important ones like your email. 2FA adds an extra layer of security because it requires one to type in an additional code when logging in. Most accounts have 2FA so you should be able to enable it for all important ones.
Incoming search terms:
Site Disclaimer
2-remove-virus.com is not sponsored, owned, affiliated, or linked to malware developers or distributors that are referenced in this article. The article does not promote or endorse any type of malware. We aim at providing useful information that will help computer users to detect and eliminate the unwanted malicious programs from their computers. This can be done manually by following the instructions presented in the article or automatically by implementing the suggested anti-malware tools.
The article is only meant to be used for educational purposes. If you follow the instructions given in the article, you agree to be contracted by the disclaimer. We do not guarantee that the artcile will present you with a solution that removes the malign threats completely. Malware changes constantly, which is why, in some cases, it may be difficult to clean the computer fully by using only the manual removal instructions.