What is Hacker Who Has Access To Your Operating System Email Scam
Hacker Who Has Access To Your Operating System Email Scam is classified as a sextortion scam. It’s essentially a fake email that threatens to publicly release a private video of you if you do not agree to pay $500. These types of sextortion email scams have been around for years now, and while the sextortion campaigns may be operated by different scammers, they all follow the same pattern and look more or less identical to one another.
Hacker Who Has Access To Your Operating System Email Scam has “Security Alert. Your accounts were hacked by a criminal group” as the subject line, which would immediately catch people’s attention and intrigue or scare them enough to open the email. The sender then proceeds to explain that they are a hacker and were able to get access to users’ operating systems and their accounts. Supposedly, they have been monitoring users’ activities for a couple of months, after infecting their computers with malware via an adult website they visited. The infection supposedly gave the hacker access to their computers, including the microphone and camera.
The sender claims to have used access to your microphone and camera to create a video of you watching pornography. According to the sender, the video shows you on one side, and the adult video you were watching on the other. They threaten to send the video to all of your contacts if you do not agree to send $500 in Bitcoin to the provided wallet address.
This email, like most sextortion emails, is not particularly convincing but it may work on users who are not familiar with such scams. The email is written in a way that would cause anxiety to the recipient, and the degrading language used in the email, as well as the mocking tone may pressure users into making a payment. After all, the fact that sextortion scams are still around years later means that some percentage of them are successful.
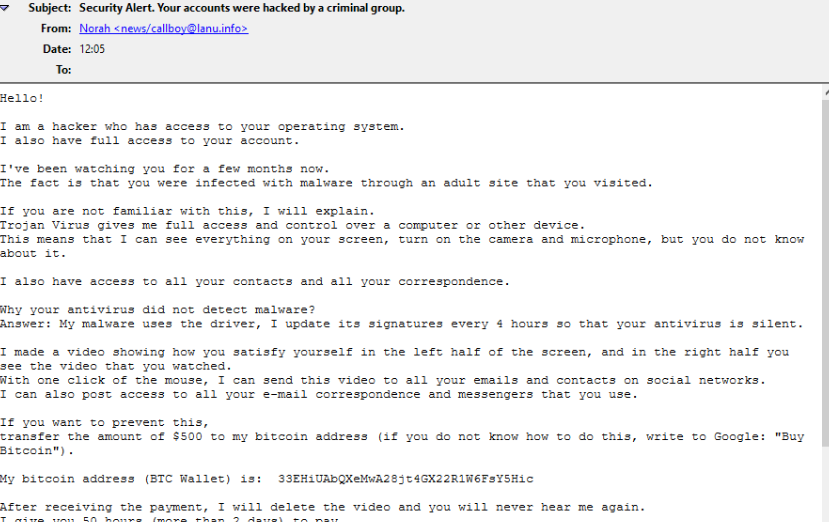
Here’s the full Hacker Who Has Access To Your Operating System Email Scam:
Subject: Security Alert. Your accounts were hacked by a criminal group.
Hello!
I am a hacker who has access to your operating system.
I also have full access to your account.I’ve been watching you for a few months now.
The fact is that you were infected with malware through an adult site that you visited.If you are not familiar with this, I will explain.
Trojan Virus gives me full access and control over a computer or other device.
This means that I can see everything on your screen, turn on the camera and microphone, but you do not know about it.I also have access to all your contacts and all your correspondence.
Why your antivirus did not detect malware?
Answer: My malware uses the driver, I update its signatures every 4 hours so that your antivirus is silent.I made a video showing how you satisfy yourself in the left half of the screen, and in the right half you see the video that you watched.
With one click of the mouse, I can send this video to all your emails and contacts on social networks.
I can also post access to all your e-mail correspondence and messengers that you use.If you want to prevent this,
transfer the amount of $500 to my bitcoin address (if you do not know how to do this, write to Google: “Buy Bitcoin”).My bitcoin address (BTC Wallet) is: –
After receiving the payment, I will delete the video and you will never hear me again.
I give you 50 hours (more than 2 days) to pay.
I have a notice reading this letter, and the timer will work when you see this letter.Filing a complaint somewhere does not make sense because this email cannot be tracked like my bitcoin address.
I do not make any mistakes.If I find that you have shared this message with someone else, the video will be immediately distributed.
Best regards!
Sextortion emails may contain correct personal information
This Hacker Who Has Access To Your Operating System Email Scam is fairly generic but some more sophisticated sextortion emails may contain users’ correct personal information, including full name and some password. Revealing users’ personal information is an effective tactic that will scare users and pressure them into making rash decisions. However, there’s an easy explanation for how scammers manage to get the information, and it has nothing to do with hacking users’ computers.
Malicious actors obtain personal information (e.g. email addresses, passwords, full names) from hacker forums, where it ends up after data leaks or breaches. Thus, if a sextortion email contains any information about you, it merely means that some service you were a customer of has either leaked your personal information or has suffered a data breach. You can check whether your email address and/or password has been leaked on haveibeenpwned.
While there’s not much you can do if your email address has been leaked, you need to immediately change your password if it’s included in a sextortion email. Keep in mind that passwords need to be complex and include upper/lowercase letters, numbers, and symbols. Passwords also need to be unique to each account. If you have trouble keeping track of your passwords, you can use password managers.
Hacker Who Has Access To Your Operating System Email Scam removal
If you receive a sextortion email, you can simply delete it. The contents of such emails are false, there is no malware on your computer nor is there a video of you watching pornography. Simply delete Hacker Who Has Access To Your Operating System Email Scam from your inbox.
Offers
Download Removal Toolto scan for Hacker Who Has Access To Your Operating SystemUse our recommended removal tool to scan for Hacker Who Has Access To Your Operating System. Trial version of provides detection of computer threats like Hacker Who Has Access To Your Operating System and assists in its removal for FREE. You can delete detected registry entries, files and processes yourself or purchase a full version.
More information about SpyWarrior and Uninstall Instructions. Please review SpyWarrior EULA and Privacy Policy. SpyWarrior scanner is free. If it detects a malware, purchase its full version to remove it.

WiperSoft Review Details WiperSoft (www.wipersoft.com) is a security tool that provides real-time security from potential threats. Nowadays, many users tend to download free software from the Intern ...
Download|more


Is MacKeeper a virus? MacKeeper is not a virus, nor is it a scam. While there are various opinions about the program on the Internet, a lot of the people who so notoriously hate the program have neve ...
Download|more


While the creators of MalwareBytes anti-malware have not been in this business for long time, they make up for it with their enthusiastic approach. Statistic from such websites like CNET shows that th ...
Download|more
Quick Menu
Step 1. Uninstall Hacker Who Has Access To Your Operating System and related programs.
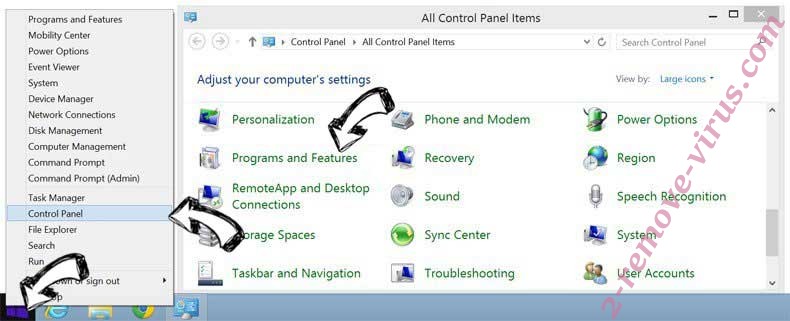
Remove Hacker Who Has Access To Your Operating System from Windows 8
Right-click in the lower left corner of the screen. Once Quick Access Menu shows up, select Control Panel choose Programs and Features and select to Uninstall a software.

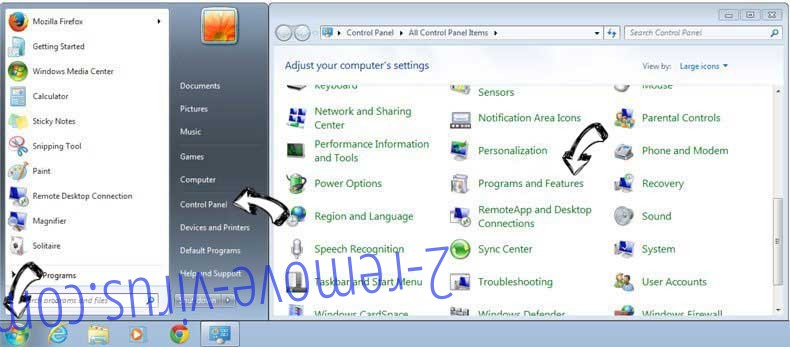
Uninstall Hacker Who Has Access To Your Operating System from Windows 7
Click Start → Control Panel → Programs and Features → Uninstall a program.

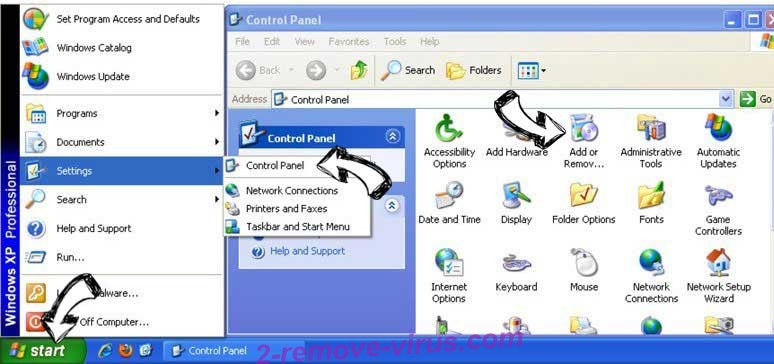
Delete Hacker Who Has Access To Your Operating System from Windows XP
Click Start → Settings → Control Panel. Locate and click → Add or Remove Programs.

Remove Hacker Who Has Access To Your Operating System from Mac OS X
Click Go button at the top left of the screen and select Applications. Select applications folder and look for Hacker Who Has Access To Your Operating System or any other suspicious software. Now right click on every of such entries and select Move to Trash, then right click the Trash icon and select Empty Trash.


Step 2. Delete Hacker Who Has Access To Your Operating System from your browsers
Terminate the unwanted extensions from Internet Explorer
- Tap the Gear icon and go to Manage Add-ons.

- Pick Toolbars and Extensions and eliminate all suspicious entries (other than Microsoft, Yahoo, Google, Oracle or Adobe)

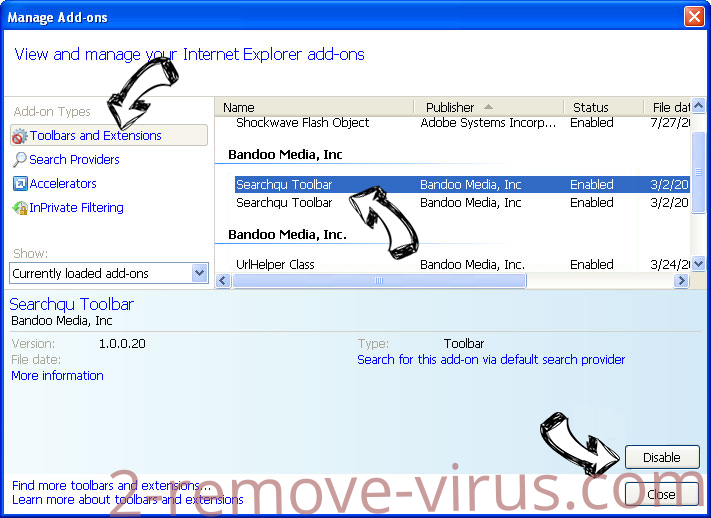
- Leave the window.
Change Internet Explorer homepage if it was changed by virus:
- Tap the gear icon (menu) on the top right corner of your browser and click Internet Options.

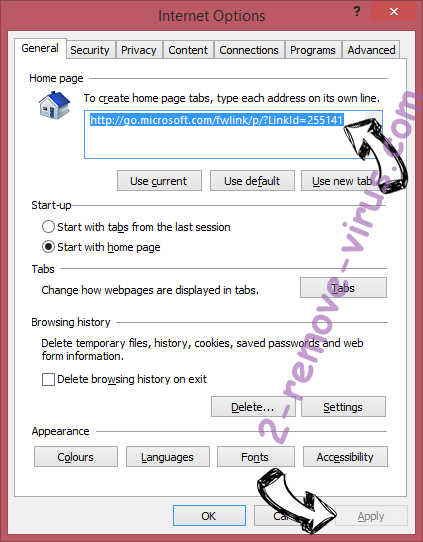
- In General Tab remove malicious URL and enter preferable domain name. Press Apply to save changes.

Reset your browser
- Click the Gear icon and move to Internet Options.

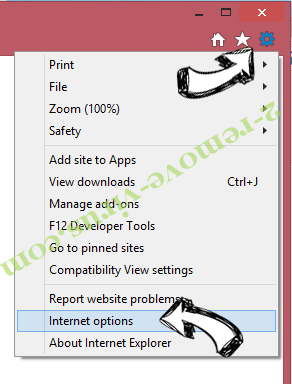
- Open the Advanced tab and press Reset.

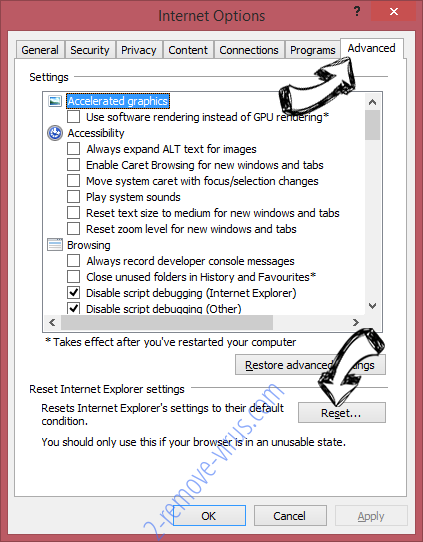
- Choose Delete personal settings and pick Reset one more time.

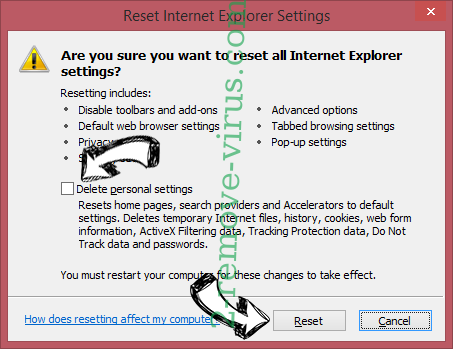
- Tap Close and leave your browser.

- If you were unable to reset your browsers, employ a reputable anti-malware and scan your entire computer with it.
Erase Hacker Who Has Access To Your Operating System from Google Chrome
- Access menu (top right corner of the window) and pick Settings.

- Choose Extensions.

- Eliminate the suspicious extensions from the list by clicking the Trash bin next to them.

- If you are unsure which extensions to remove, you can disable them temporarily.

Reset Google Chrome homepage and default search engine if it was hijacker by virus
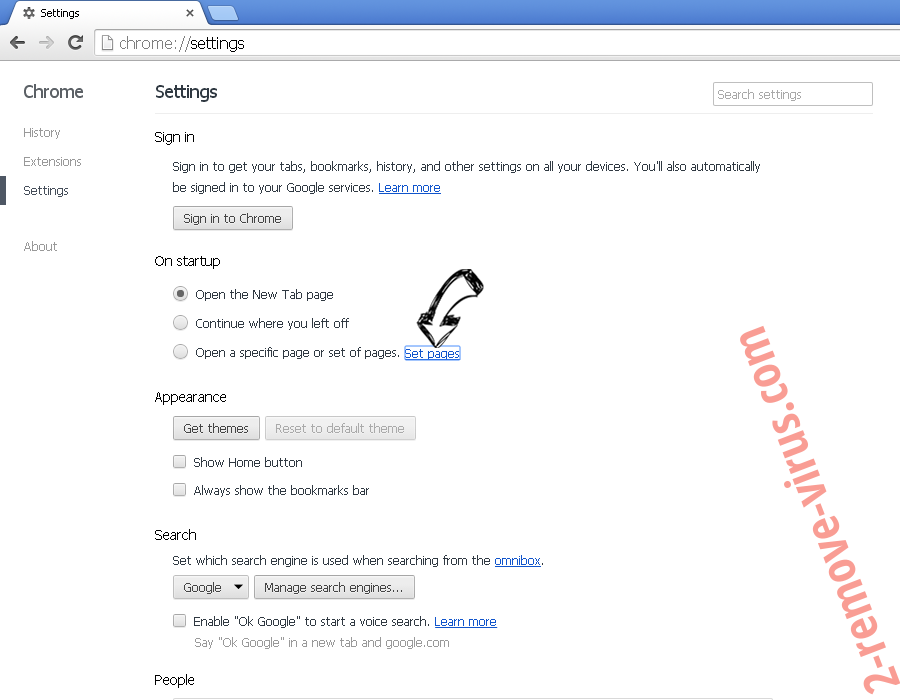
- Press on menu icon and click Settings.

- Look for the “Open a specific page” or “Set Pages” under “On start up” option and click on Set pages.

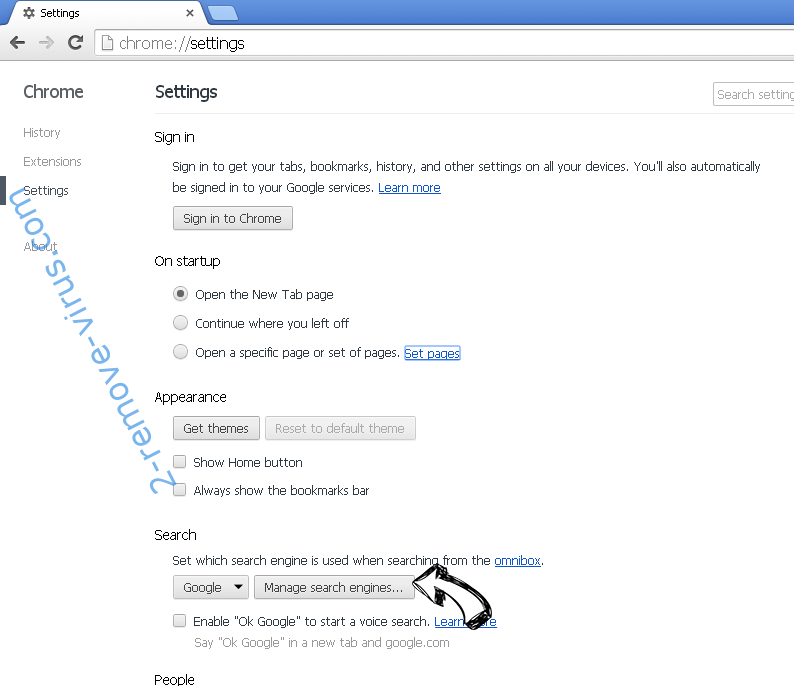
- In another window remove malicious search sites and enter the one that you want to use as your homepage.


- Under the Search section choose Manage Search engines. When in Search Engines..., remove malicious search websites. You should leave only Google or your preferred search name.


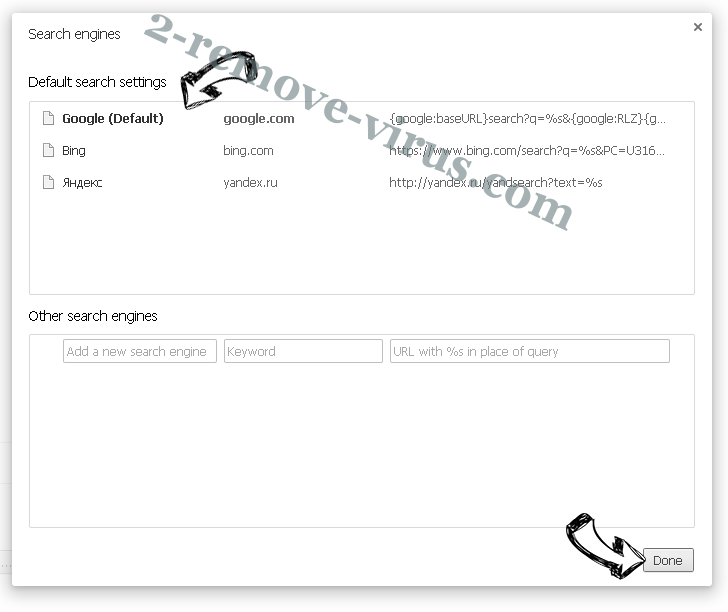
Reset your browser
- If the browser still does not work the way you prefer, you can reset its settings.
- Open menu and navigate to Settings.

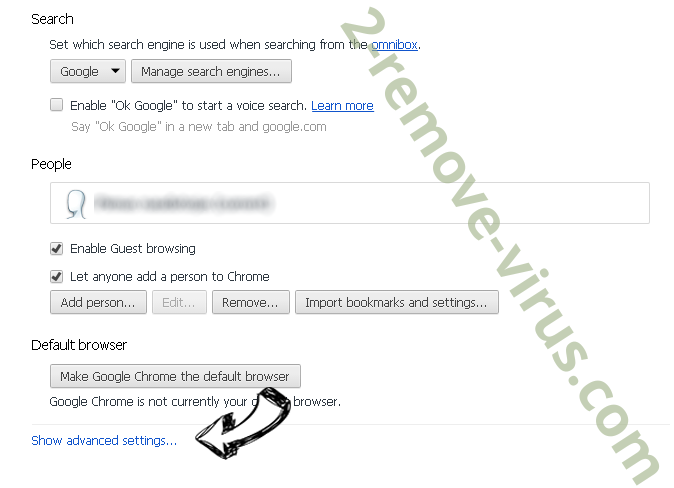
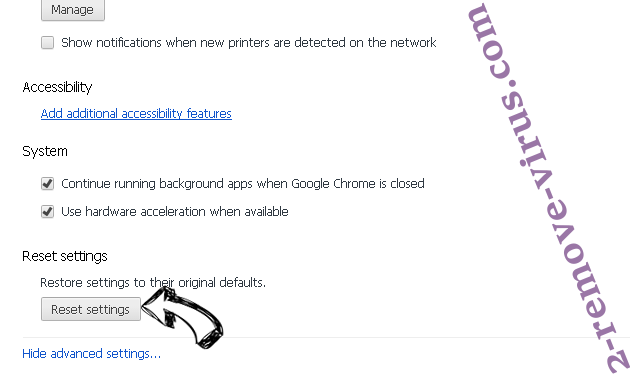
- Press Reset button at the end of the page.

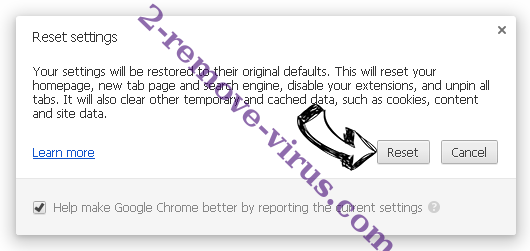
- Tap Reset button one more time in the confirmation box.

- If you cannot reset the settings, purchase a legitimate anti-malware and scan your PC.
Remove Hacker Who Has Access To Your Operating System from Mozilla Firefox
- In the top right corner of the screen, press menu and choose Add-ons (or tap Ctrl+Shift+A simultaneously).

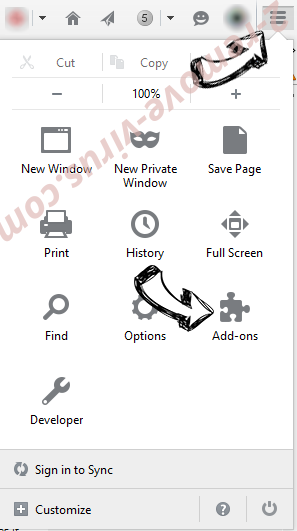
- Move to Extensions and Add-ons list and uninstall all suspicious and unknown entries.

Change Mozilla Firefox homepage if it was changed by virus:
- Tap on the menu (top right corner), choose Options.

- On General tab delete malicious URL and enter preferable website or click Restore to default.

- Press OK to save these changes.
Reset your browser
- Open the menu and tap Help button.

- Select Troubleshooting Information.

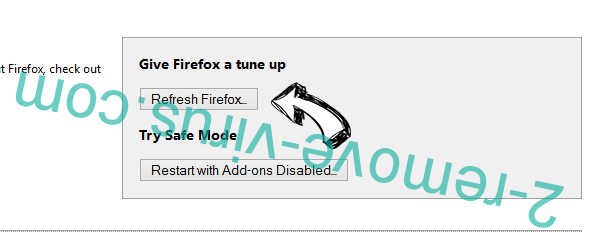
- Press Refresh Firefox.

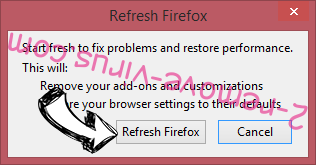
- In the confirmation box, click Refresh Firefox once more.

- If you are unable to reset Mozilla Firefox, scan your entire computer with a trustworthy anti-malware.
Uninstall Hacker Who Has Access To Your Operating System from Safari (Mac OS X)
- Access the menu.
- Pick Preferences.

- Go to the Extensions Tab.

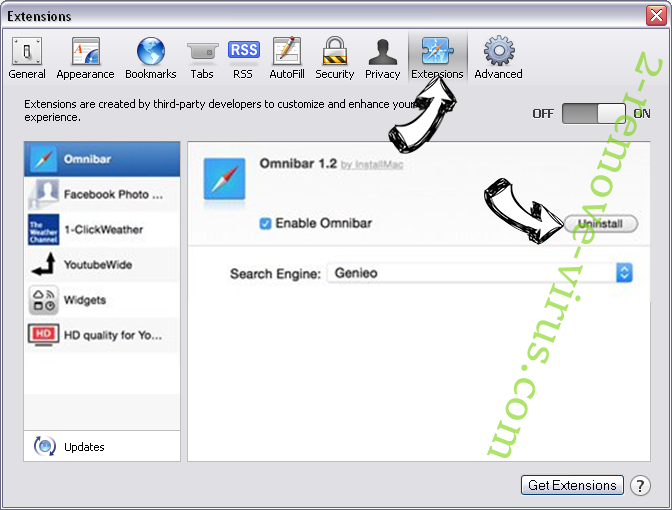
- Tap the Uninstall button next to the undesirable Hacker Who Has Access To Your Operating System and get rid of all the other unknown entries as well. If you are unsure whether the extension is reliable or not, simply uncheck the Enable box in order to disable it temporarily.
- Restart Safari.
Reset your browser
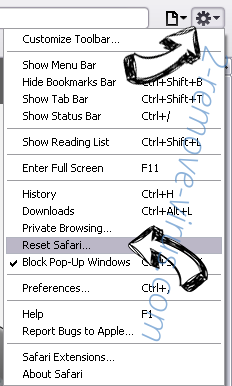
- Tap the menu icon and choose Reset Safari.

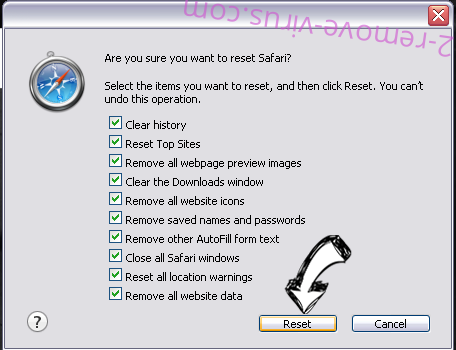
- Pick the options which you want to reset (often all of them are preselected) and press Reset.

- If you cannot reset the browser, scan your whole PC with an authentic malware removal software.
Site Disclaimer
2-remove-virus.com is not sponsored, owned, affiliated, or linked to malware developers or distributors that are referenced in this article. The article does not promote or endorse any type of malware. We aim at providing useful information that will help computer users to detect and eliminate the unwanted malicious programs from their computers. This can be done manually by following the instructions presented in the article or automatically by implementing the suggested anti-malware tools.
The article is only meant to be used for educational purposes. If you follow the instructions given in the article, you agree to be contracted by the disclaimer. We do not guarantee that the artcile will present you with a solution that removes the malign threats completely. Malware changes constantly, which is why, in some cases, it may be difficult to clean the computer fully by using only the manual removal instructions.