WirelessZipServer Mac virus is a browser hijacker targeting Mac computers
WirelessZipServer Mac virus browser hijacker is also called a redirect virus, and mainly targets Mac devices. Browser hijackers don’t aim to damage the system directly, therefore are thought to be pretty minor infections. Hijackers’ main goal is to redirect users to sponsored sites and generate traffic/profit, which is why they aren’t harmless infections. Hijackers install rather secretly but once they are in, they’re quite obvious infections. Sponsored content will be mixed in among legitimate search results, you’ll end up on unusual web pages, and you will note your browser exhibiting other unusual behaviour. However, because not everyone knows what specifically is a browser hijacker, they may not associate the unusual behaviour with an infection. A simple search of the signs/web page redirected to with a search engine usually points users in the correct direction.
You’ll see changes made to your browser’s settings, besides the weird redirects. Every time it is launched, you browser will have a different homepage/new tabs, which may be complicated to undo. Making alterations to your browser’s settings permits hijackers to redirect you.
Hijackers cannot install by themselves because they aren’t malware or viruses, even if many users refer to them as that. While users are normally not aware of this, but they provide permission for the hijacker to install themselves. Software bundling is the method used by pests like hijackers to install, meaning they are attached to freeware as extra items and can install together with it. Preventing these unwanted installation isn’t hard, and the next section of the report will explain how to do it.
It is not the most harmful things you may infect your system with, but the quicker you carry out WirelessZipServer Mac virus uninstallation, the better. Your normal browsing might be interrupted by the hijacker but it might also expose you to dangerous content such as malware and scams.
Ways a hijacker installs
Browser hijackers install with free programs, as we have said above. This method of distribution is called program bundling, and it’s essentially attaching hijackers and other extra offers to popular free programs. Users are generally not informed about any offers being added but they’re set to install with the freeware, which makes program bundling a dubious installation method. The installations aren’t hard to avoid, however, if you pay attention to program installation processes.
Above all else, choose Advanced (Custom) settings when installing freeware. Otherwise, the offers will stay hidden. Advanced will allow you to uncheck everything, in addition to making all items visible. Deselecting the boxes of those items is sufficient to prevent them from installing. It may take a long time to get rid of already installed programs, compared to the seconds it takes to avoid them from installing initially. By paying attention to how you install programs, you will block many rubbish applications.
More details about the hijacker
Redirect viruses are very simple to see as they take over browsers (Safari, Google Chrome and Mozilla Firefox) and cause redirects to random websites. The hijacker’s promoted site will become your homepage and new tabs, and whenever you launch your browser, that’s the page you’ll see. The browser will also have another search engine. You will be redirected to a web page promoted by the hijacker and then shown search results that have been modified when you search for something through the browser address bar. Hijackers alter search results so you’ll certainly see sponsored content among valid results. Because the hijacker’s main purpose is to generate traffic and income, users are redirected to those sponsored pages. Take into consideration that being randomly redirected to weird web pages isn’t only annoying but also possibly damaging. We would advise not interacting with any sponsored or advertisement content until you eliminate the hijacker because of that. You could easily be led to dangerous site because the hijacker does not check whether the sites are safe. A sponsored site might be encouraging you to download harmful malicious software or trying to trick you into falling for some kind of scam. So even if hijackers aren’t directly damaging to the computer, keeping them installed is a bad idea.
We ought to also note that browser hijackers have a tendency to spy on users, and collect various information related their searches, visited websites, IP address and more. It’s likely that the hijacker would share the information with unfamiliar third-parties as well.
In short, the hijacker installed on your Mac without your authorization, made unwanted changes to your browsers, started leading you to sponsored sites in order to generate revenue, and displayed you potentially dubious content. WirelessZipServer Mac virus removal is essential, and the quicker you do it the better.
WirelessZipServer Mac virus elimination
It is easiest to uninstall WirelessZipServer Mac virus by using anti-spyware software. It is easier to use anti-spyware programs to remove infections because the software takes care of everything and guarantees the infection is no longer present. Manual WirelessZipServer Mac virus elimination is also possible, if you’re familiar with what to do and ensure to not leave any remaining hijacker files. You could modify your browser’s settings back to normal after WirelessZipServer Mac virus deletion.
Offers
Download Removal Toolto scan for WirelessZipServerUse our recommended removal tool to scan for WirelessZipServer. Trial version of provides detection of computer threats like WirelessZipServer and assists in its removal for FREE. You can delete detected registry entries, files and processes yourself or purchase a full version.
More information about SpyWarrior and Uninstall Instructions. Please review SpyWarrior EULA and Privacy Policy. SpyWarrior scanner is free. If it detects a malware, purchase its full version to remove it.

WiperSoft Review Details WiperSoft (www.wipersoft.com) is a security tool that provides real-time security from potential threats. Nowadays, many users tend to download free software from the Intern ...
Download|more


Is MacKeeper a virus? MacKeeper is not a virus, nor is it a scam. While there are various opinions about the program on the Internet, a lot of the people who so notoriously hate the program have neve ...
Download|more


While the creators of MalwareBytes anti-malware have not been in this business for long time, they make up for it with their enthusiastic approach. Statistic from such websites like CNET shows that th ...
Download|more
Quick Menu
Step 1. Uninstall WirelessZipServer and related programs.
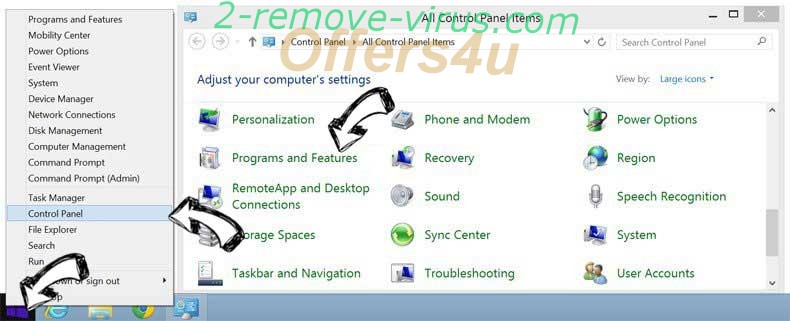
Remove WirelessZipServer from Windows 8
Right-click in the lower left corner of the screen. Once Quick Access Menu shows up, select Control Panel choose Programs and Features and select to Uninstall a software.

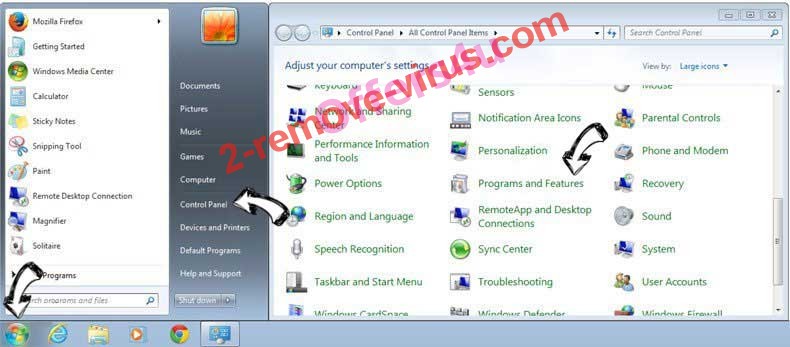
Uninstall WirelessZipServer from Windows 7
Click Start → Control Panel → Programs and Features → Uninstall a program.

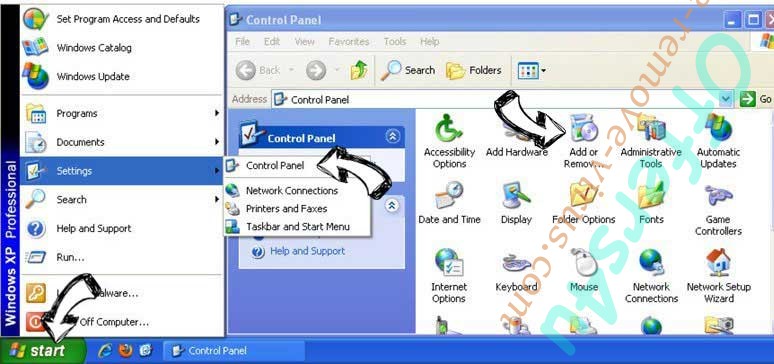
Delete WirelessZipServer from Windows XP
Click Start → Settings → Control Panel. Locate and click → Add or Remove Programs.

Remove WirelessZipServer from Mac OS X
Click Go button at the top left of the screen and select Applications. Select applications folder and look for WirelessZipServer or any other suspicious software. Now right click on every of such entries and select Move to Trash, then right click the Trash icon and select Empty Trash.


Step 2. Delete WirelessZipServer from your browsers
Terminate the unwanted extensions from Internet Explorer
- Tap the Gear icon and go to Manage Add-ons.

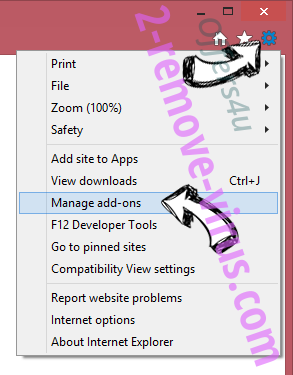
- Pick Toolbars and Extensions and eliminate all suspicious entries (other than Microsoft, Yahoo, Google, Oracle or Adobe)

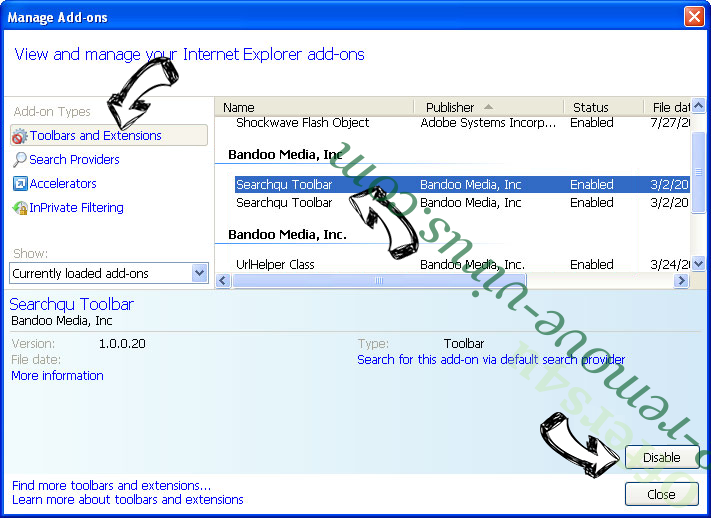
- Leave the window.
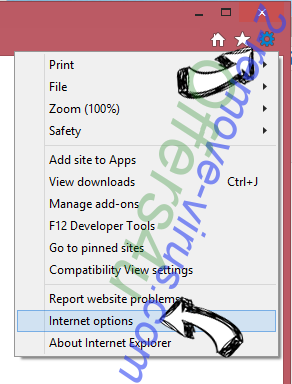
Change Internet Explorer homepage if it was changed by virus:
- Tap the gear icon (menu) on the top right corner of your browser and click Internet Options.

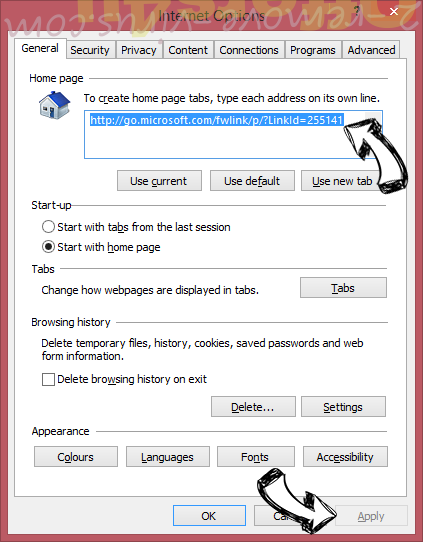
- In General Tab remove malicious URL and enter preferable domain name. Press Apply to save changes.

Reset your browser
- Click the Gear icon and move to Internet Options.

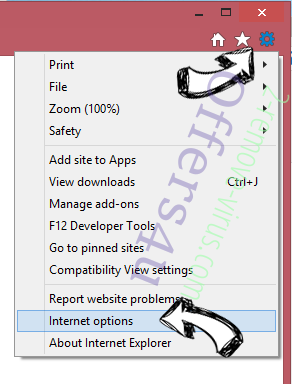
- Open the Advanced tab and press Reset.

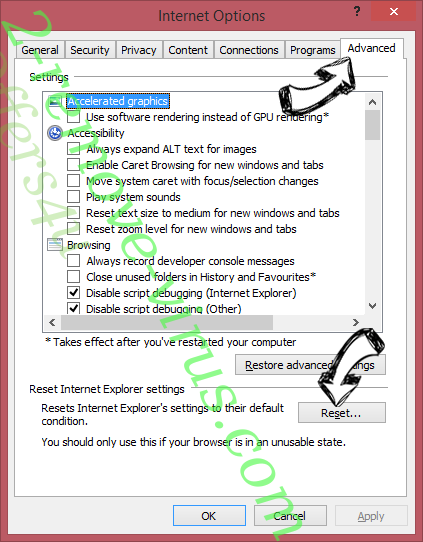
- Choose Delete personal settings and pick Reset one more time.

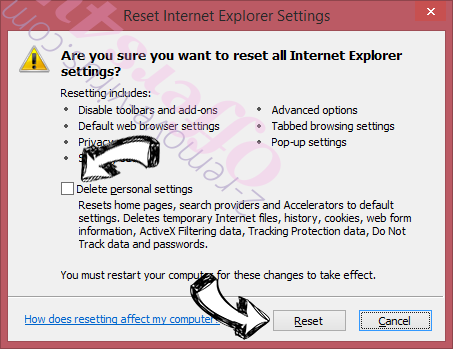
- Tap Close and leave your browser.

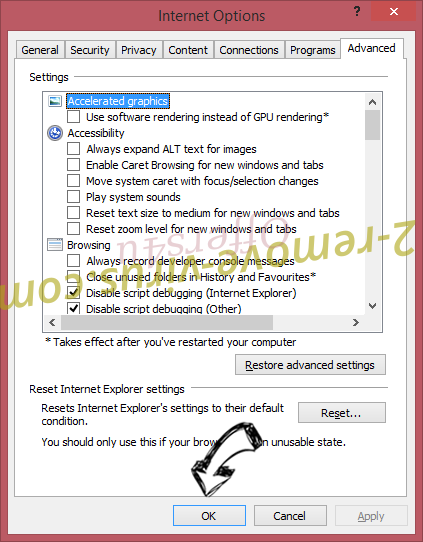
- If you were unable to reset your browsers, employ a reputable anti-malware and scan your entire computer with it.
Erase WirelessZipServer from Google Chrome
- Access menu (top right corner of the window) and pick Settings.

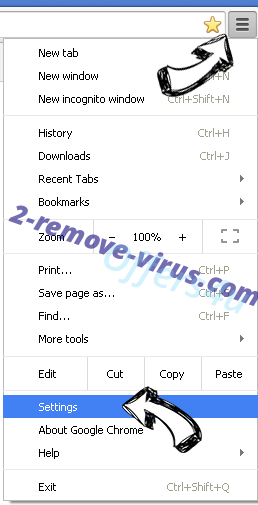
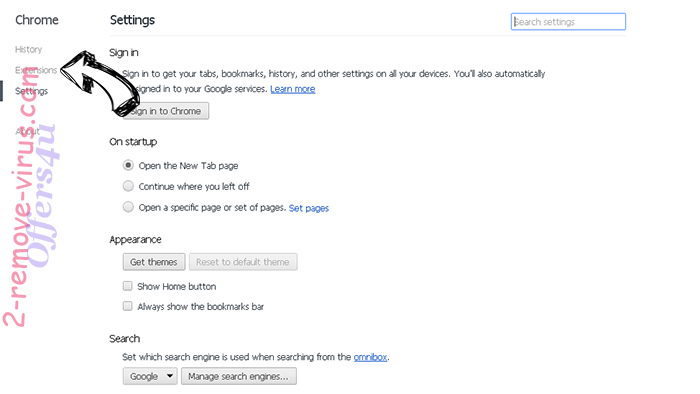
- Choose Extensions.

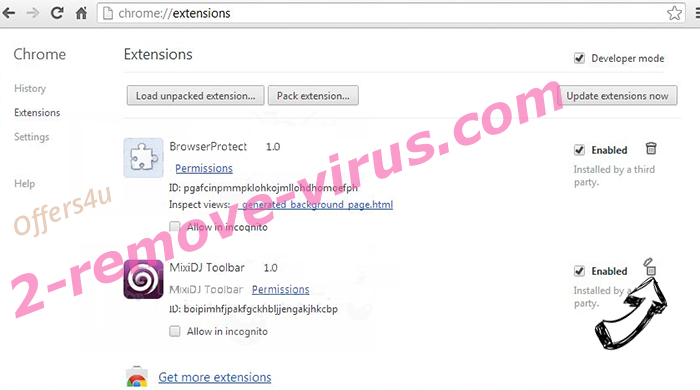
- Eliminate the suspicious extensions from the list by clicking the Trash bin next to them.

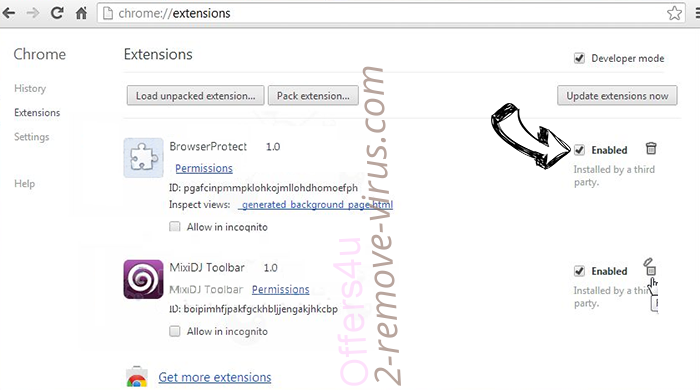
- If you are unsure which extensions to remove, you can disable them temporarily.

Reset Google Chrome homepage and default search engine if it was hijacker by virus
- Press on menu icon and click Settings.

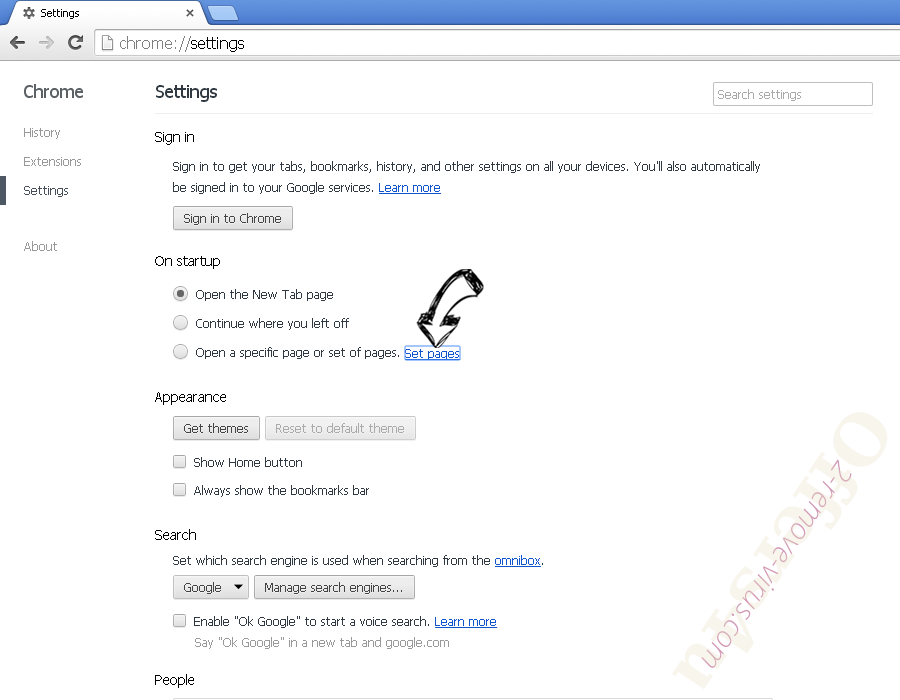
- Look for the “Open a specific page” or “Set Pages” under “On start up” option and click on Set pages.

- In another window remove malicious search sites and enter the one that you want to use as your homepage.


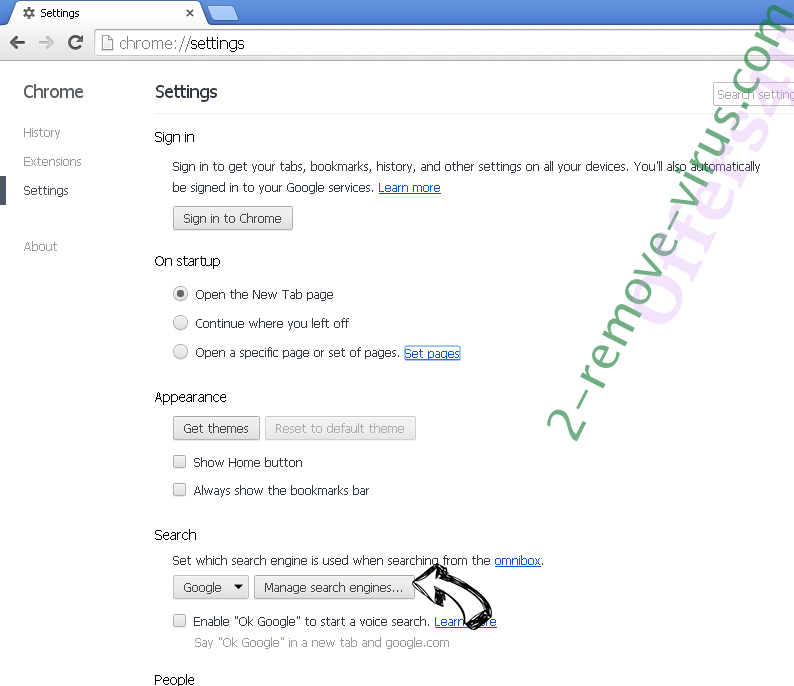
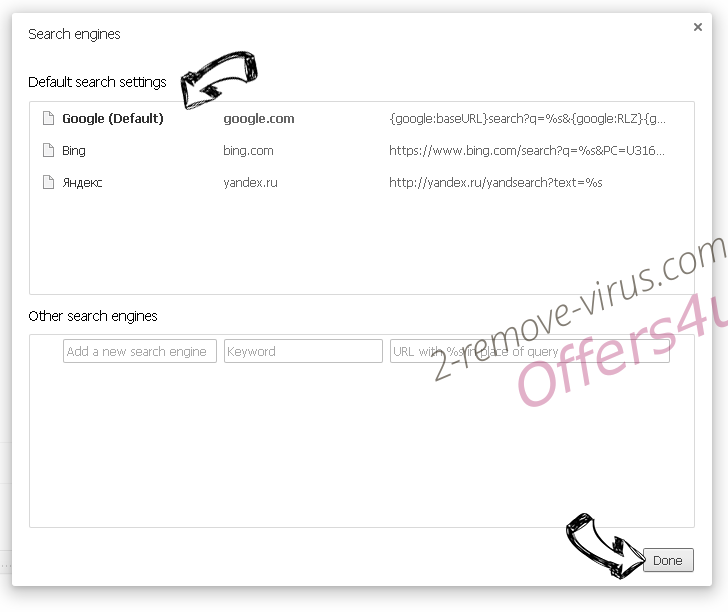
- Under the Search section choose Manage Search engines. When in Search Engines..., remove malicious search websites. You should leave only Google or your preferred search name.


Reset your browser
- If the browser still does not work the way you prefer, you can reset its settings.
- Open menu and navigate to Settings.

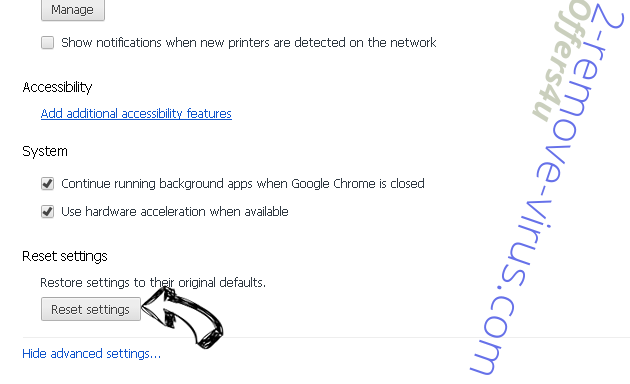
- Press Reset button at the end of the page.

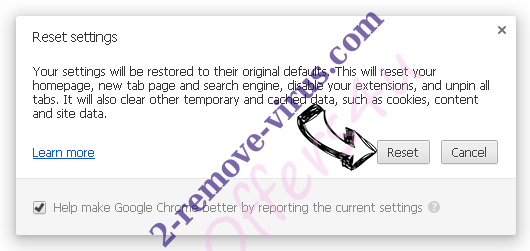
- Tap Reset button one more time in the confirmation box.

- If you cannot reset the settings, purchase a legitimate anti-malware and scan your PC.
Remove WirelessZipServer from Mozilla Firefox
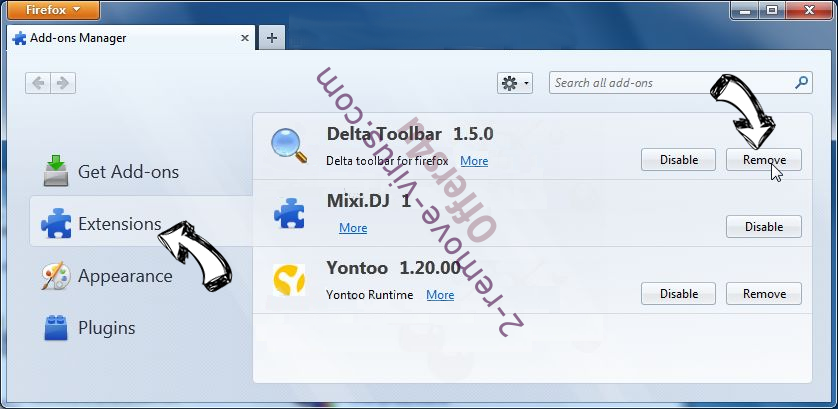
- In the top right corner of the screen, press menu and choose Add-ons (or tap Ctrl+Shift+A simultaneously).

- Move to Extensions and Add-ons list and uninstall all suspicious and unknown entries.

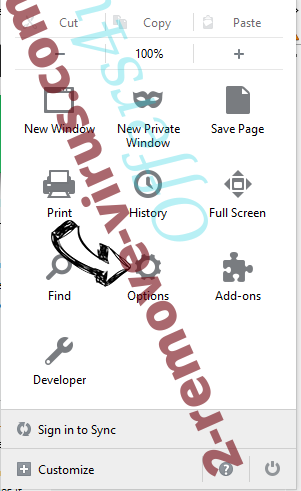
Change Mozilla Firefox homepage if it was changed by virus:
- Tap on the menu (top right corner), choose Options.

- On General tab delete malicious URL and enter preferable website or click Restore to default.

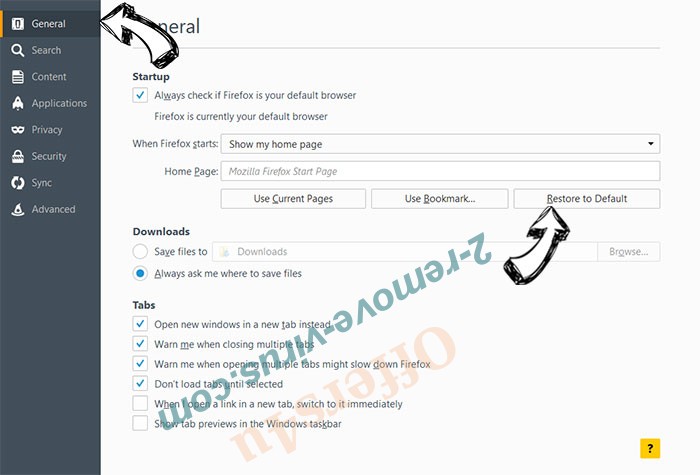
- Press OK to save these changes.
Reset your browser
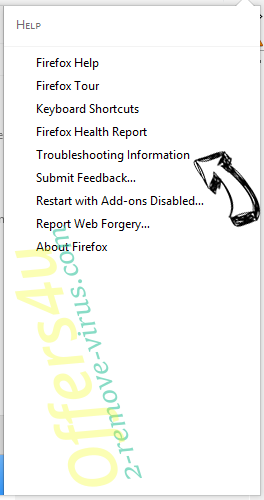
- Open the menu and tap Help button.

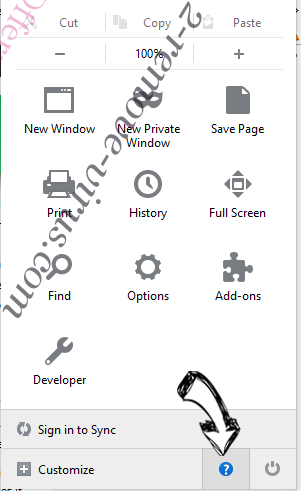
- Select Troubleshooting Information.

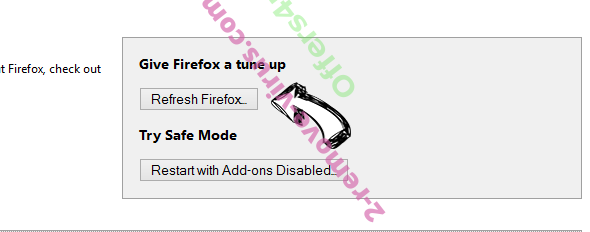
- Press Refresh Firefox.

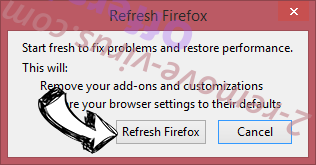
- In the confirmation box, click Refresh Firefox once more.

- If you are unable to reset Mozilla Firefox, scan your entire computer with a trustworthy anti-malware.
Uninstall WirelessZipServer from Safari (Mac OS X)
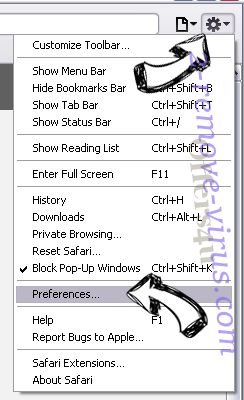
- Access the menu.
- Pick Preferences.

- Go to the Extensions Tab.

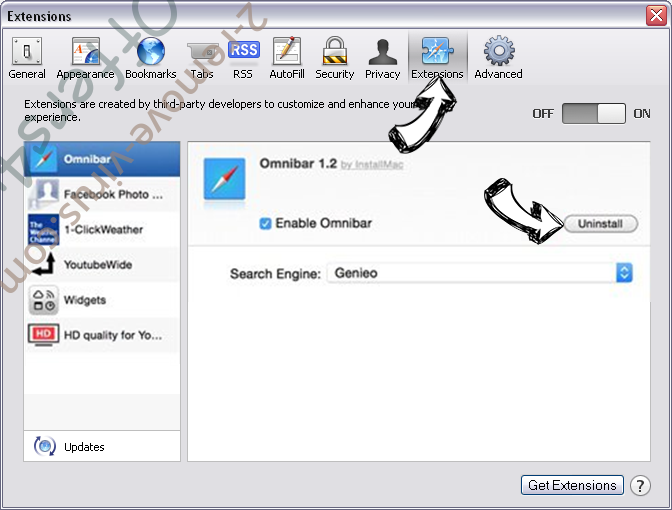
- Tap the Uninstall button next to the undesirable WirelessZipServer and get rid of all the other unknown entries as well. If you are unsure whether the extension is reliable or not, simply uncheck the Enable box in order to disable it temporarily.
- Restart Safari.
Reset your browser
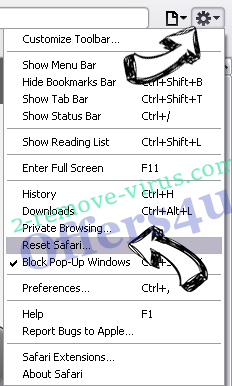
- Tap the menu icon and choose Reset Safari.

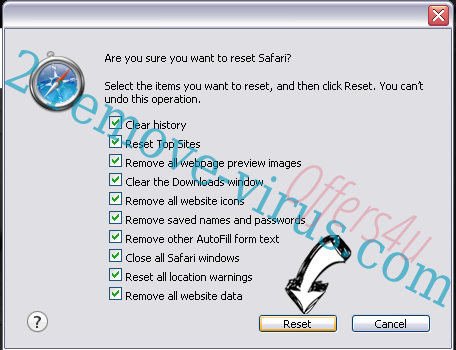
- Pick the options which you want to reset (often all of them are preselected) and press Reset.

- If you cannot reset the browser, scan your whole PC with an authentic malware removal software.
Site Disclaimer
2-remove-virus.com is not sponsored, owned, affiliated, or linked to malware developers or distributors that are referenced in this article. The article does not promote or endorse any type of malware. We aim at providing useful information that will help computer users to detect and eliminate the unwanted malicious programs from their computers. This can be done manually by following the instructions presented in the article or automatically by implementing the suggested anti-malware tools.
The article is only meant to be used for educational purposes. If you follow the instructions given in the article, you agree to be contracted by the disclaimer. We do not guarantee that the artcile will present you with a solution that removes the malign threats completely. Malware changes constantly, which is why, in some cases, it may be difficult to clean the computer fully by using only the manual removal instructions.