8lock8 Ransomware Removal Instructions
8lock8 is a ransomware infection that is based on HiddenTear, which is an open-source program used by cyber criminals to extort money from unsuspecting PC users. The parasite spreads on the Internet by making use of the same old deceptive tactics. It uses corrupted links or attachments that usually reach you through spam email messages.
It may also get distributed in freeware bundles downloaded from unsafe sites or fake adverts. Once you get infected with the 8lock8 Trojan, it encrypts your data and uses it as a “hostage” for which you are supposed to pay the “ransom”. We urge you not to do that and remove 8lock8 Ransomware as soon as possible.
 How does 8lock8 Ransomware work?
How does 8lock8 Ransomware work?
Right after the malware infiltrates your computer, it start scanning your drives for multimedia file. This may result in a more sluggish computer performance. After it completes the scan, the infection encodes all detected data using the AES-256 encryption algorithm. The list of affected files includes your videos, databases, documents, photos, and more. All of these files have the .8lock8 extension added to them. You will not be able to open any longer.
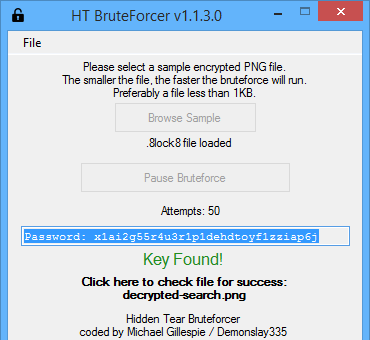
The so-called ransom note can be found in each folder that contains corrupted files. It is called READ_IT.txt. If you open it, you will see the message stating that your files have been cryptographically encoded and that in order to restore them, you should contact the developers of the infection. You should never follow the instructions given to you by cyber criminals as they simply cannot be trusted. Moreover, there is no need for you to contact them anyway, because Demonslay355 has developed a file decryptor specifically for this malicious threat. You can download “HiddenTear Bruteforcer” online and implement the tool. You can also try other variants of restoring your data like System Restore or other decryptors, should you run into any trouble with the Bruteforcer. You also should not forget to completely eliminate 8lock8 Ransomware from your PC.
How to remove 8lock8 Ransomware?
You can delete 8lock8 Ransomware manually by following the instructions we have prepared below the article. It would be more effective, however, to go with automatic 8lock8 Ransomware removal instead. There are several reasons for that. One of them is the fact that there may be other malicious files and programs on your PC. If you use an anti-malware utility to uninstall 8lock8 Ransomware, it will detect and delete other unsafe components from your system. In addition to 8lock8 Ransomware removal, you will also make sure that your computer stays safeguarded from now on as the security tool also comes with real-time online protection.
Delete 8lock8 Ransomware
- Press Win+E and locate the downloaded malicious attachment
- Delete this file and delete READ_IT.txt from your desktop
- Empty the Recycle Bin and restart your PC
Offers
Download Removal Toolto scan for 8lock8 RansomwareUse our recommended removal tool to scan for 8lock8 Ransomware. Trial version of provides detection of computer threats like 8lock8 Ransomware and assists in its removal for FREE. You can delete detected registry entries, files and processes yourself or purchase a full version.
More information about SpyWarrior and Uninstall Instructions. Please review SpyWarrior EULA and Privacy Policy. SpyWarrior scanner is free. If it detects a malware, purchase its full version to remove it.

WiperSoft Review Details WiperSoft (www.wipersoft.com) is a security tool that provides real-time security from potential threats. Nowadays, many users tend to download free software from the Intern ...
Download|more


Is MacKeeper a virus? MacKeeper is not a virus, nor is it a scam. While there are various opinions about the program on the Internet, a lot of the people who so notoriously hate the program have neve ...
Download|more


While the creators of MalwareBytes anti-malware have not been in this business for long time, they make up for it with their enthusiastic approach. Statistic from such websites like CNET shows that th ...
Download|more
Site Disclaimer
2-remove-virus.com is not sponsored, owned, affiliated, or linked to malware developers or distributors that are referenced in this article. The article does not promote or endorse any type of malware. We aim at providing useful information that will help computer users to detect and eliminate the unwanted malicious programs from their computers. This can be done manually by following the instructions presented in the article or automatically by implementing the suggested anti-malware tools.
The article is only meant to be used for educational purposes. If you follow the instructions given in the article, you agree to be contracted by the disclaimer. We do not guarantee that the artcile will present you with a solution that removes the malign threats completely. Malware changes constantly, which is why, in some cases, it may be difficult to clean the computer fully by using only the manual removal instructions.