About this infection
icrypt@cock.li Ransomware is a file-encrypting type of malware, detected by malware researcher Jakub Kroustek. It’s a variant of Dharma Ransomware, a malware that regularly releases new versions. It’s a highly dangerous piece of malicious software that encrypts files and then demands payment in order to unlock them. Infection can happen very easily in various ways, which also adds to the dangerousness of ransomware. 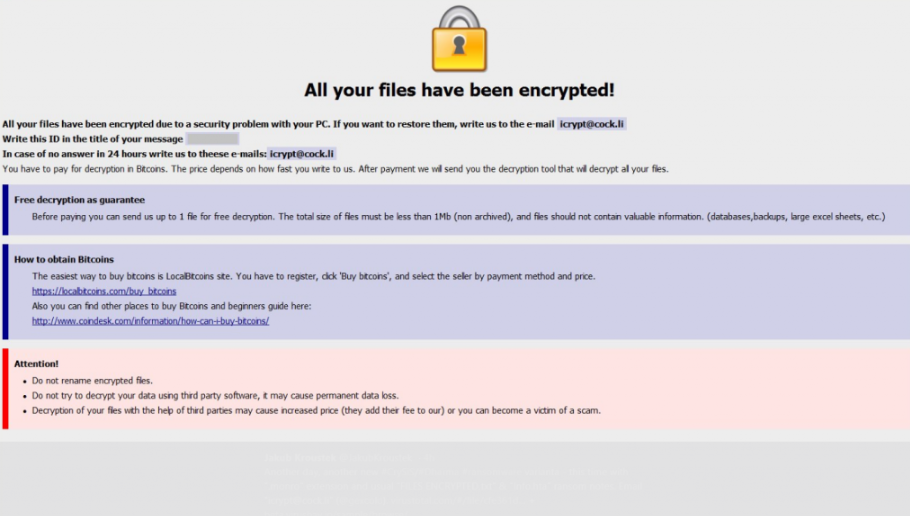
When files are taken for hostage, crooks demand that victims pay a certain amount of money in order recover them. The sum varies from ransomware to ransomware, but is generally somewhere in between $100 and $1000. Paying the ransom is never recommended because file decryption does not always happen. Trusting the people who encrypted your files in the first place to not just steal your money is not a great idea. What’s there to stop them from not giving you a decrypter after you pay? Investing that money into back would be a better idea. Backup is the primary way to protect oneself from ransomware, thus files should be backed up regularly. Furthermore, if you pay the ransom, you would be supporting criminal’s future activities, and they would continue in hopes of getting more profit.
If you had made backup prior to infection, you can safely remove icrypt@cock.li Ransomware with anti-malware and then proceed to recover files from backup. If you do not have backup, you have the option of waiting for malware researchers to develop a decrypter and release it for free.
How does it spread?
Ransomware spreads in a variety of different ways, one of the more common being spam emails. Ransomware distributors attach infected files to emails and send them to hundreds or even thousands of potential victims. When the attached file is opened by the user, the ransomware can start file encryption. If you don’t want to end up with ransomware again, you need to be very careful about what emails you open. Spam email can generally be noticed, as long as you know what to look for. For example, spam emails will contain loads of grammar mistakes and be written in weird English (or whichever other language). Senders may pretend to come from legitimate companies in order to appease users. This can be easily checked by looking at the email address. If it’s a random string of letters and numbers, you can be sure that’s spam. And even if the email looks legitimate, it’s suggested to look into it using a search engine.
One thing you should take notice of is how you are addressed in emails. Spam emails whose senders are pretending to come from legitimate companies will refer to you as User, Member or Customer instead of your name.
What happened to your files?
The ransomware started encrypting your files as soon as you opened the infected file. You probably didn’t even notice it happening because it happened in the background. Once the process is complete, you will be unable to open files. Encrypted files will have an id-%ID%.[icrypt@cock.li].monro file extension added to them, so you will know which ones have been affected. You will then notice a ransom note FILES ENCRYPTED.txt. It will explain that your files have been encrypted and in order to get them back, you will need to email them. The crooks will then demand that you pay a certain amount of money, and they will send you a decryption tool in return. The note also says that the price depends on how fast you contact them.
Paying them anything, no matter how much they ask for, is not recommended. It would not be the first time crooks just took the money without providing the decrypter. There’s nothing stopping them from doing so. You would also be supporting their future projects, of which you could become a victim of again.
Backup would have saved you a lot of trouble. You could just delete icrypt@cock.li Ransomware and then recover files without having to worry about losing something. However, all is not lost if you have no other options. Occasionally, malware researchers are able to crack the ransomware and can release free decryption tools. So you can store your encrypted files and wait for a free tool to unlock them.
icrypt@cock.li Ransomware removal
You will need to obtain anti-malware software to uninstall icrypt@cock.li Ransomware from your computer. Manual icrypt@cock.li Ransomware removal would be too complex for inexperienced users and further damage may be done. After you delete icrypt@cock.li Ransomware, you can restore files from backup. However, if you did not have backup, do not expect that removing the malware will recover files, as that is not how it works.
Offers
Download Removal Toolto scan for icrypt@cock.li RansomwareUse our recommended removal tool to scan for icrypt@cock.li Ransomware. Trial version of provides detection of computer threats like icrypt@cock.li Ransomware and assists in its removal for FREE. You can delete detected registry entries, files and processes yourself or purchase a full version.
More information about SpyWarrior and Uninstall Instructions. Please review SpyWarrior EULA and Privacy Policy. SpyWarrior scanner is free. If it detects a malware, purchase its full version to remove it.

WiperSoft Review Details WiperSoft (www.wipersoft.com) is a security tool that provides real-time security from potential threats. Nowadays, many users tend to download free software from the Intern ...
Download|more


Is MacKeeper a virus? MacKeeper is not a virus, nor is it a scam. While there are various opinions about the program on the Internet, a lot of the people who so notoriously hate the program have neve ...
Download|more


While the creators of MalwareBytes anti-malware have not been in this business for long time, they make up for it with their enthusiastic approach. Statistic from such websites like CNET shows that th ...
Download|more
Quick Menu
Step 1. Delete icrypt@cock.li Ransomware using Safe Mode with Networking.
Remove icrypt@cock.li Ransomware from Windows 7/Windows Vista/Windows XP
- Click on Start and select Shutdown.
- Choose Restart and click OK.

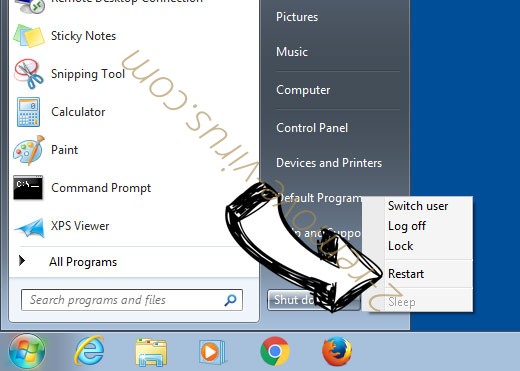
- Start tapping F8 when your PC starts loading.
- Under Advanced Boot Options, choose Safe Mode with Networking.

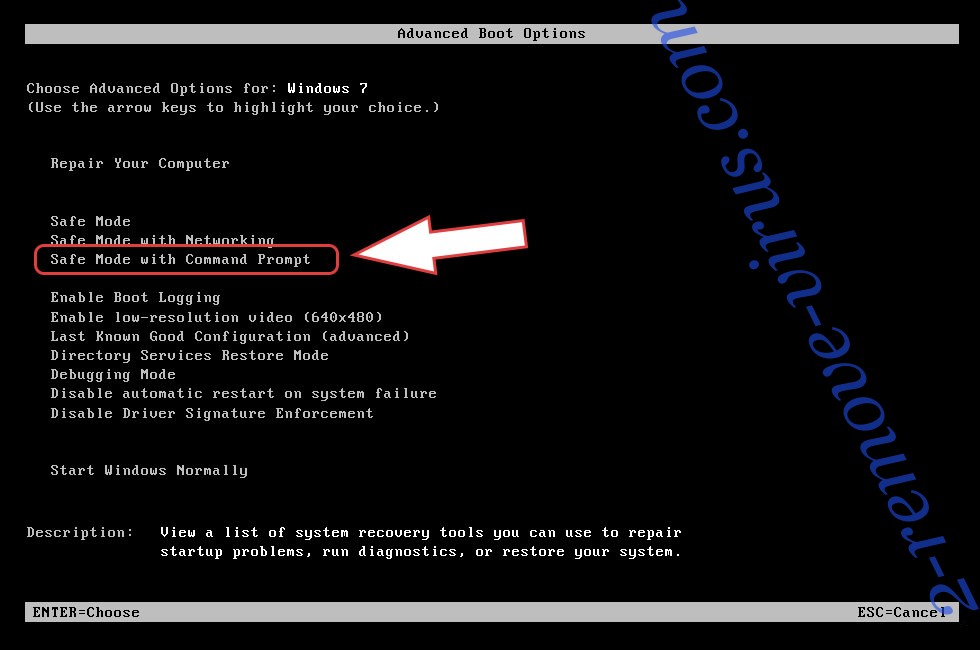
- Open your browser and download the anti-malware utility.
- Use the utility to remove icrypt@cock.li Ransomware
Remove icrypt@cock.li Ransomware from Windows 8/Windows 10
- On the Windows login screen, press the Power button.
- Tap and hold Shift and select Restart.

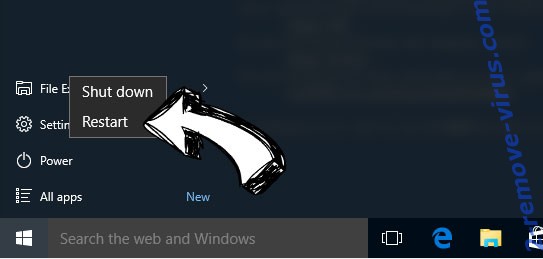
- Go to Troubleshoot → Advanced options → Start Settings.
- Choose Enable Safe Mode or Safe Mode with Networking under Startup Settings.

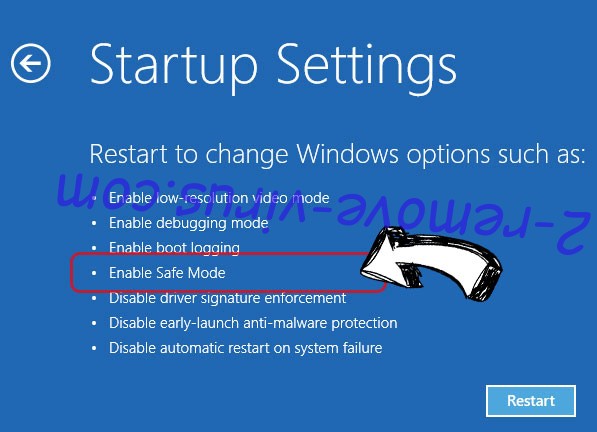
- Click Restart.
- Open your web browser and download the malware remover.
- Use the software to delete icrypt@cock.li Ransomware
Step 2. Restore Your Files using System Restore
Delete icrypt@cock.li Ransomware from Windows 7/Windows Vista/Windows XP
- Click Start and choose Shutdown.
- Select Restart and OK


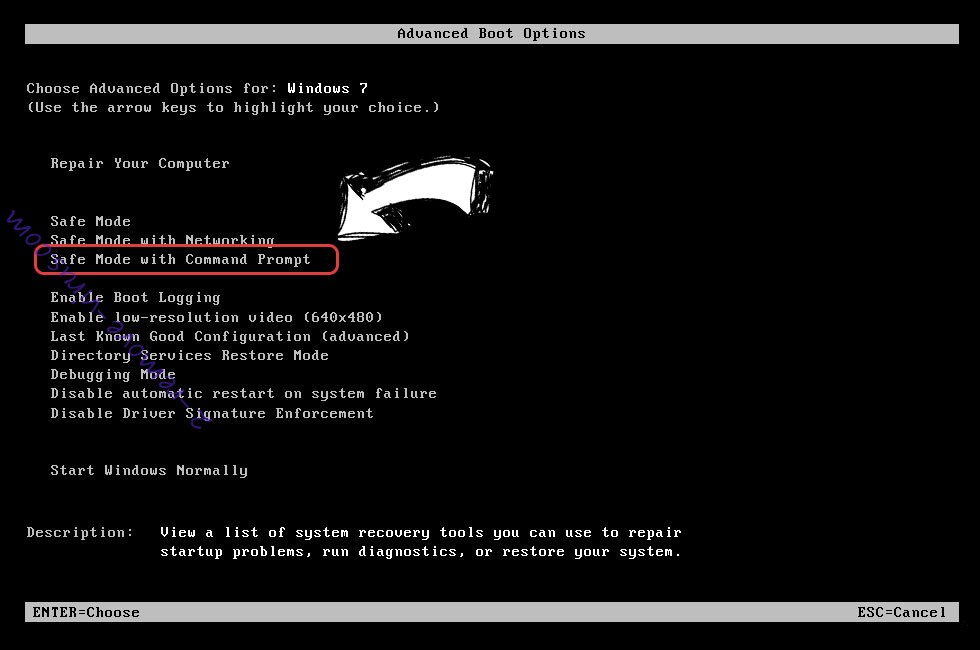
- When your PC starts loading, press F8 repeatedly to open Advanced Boot Options
- Choose Command Prompt from the list.

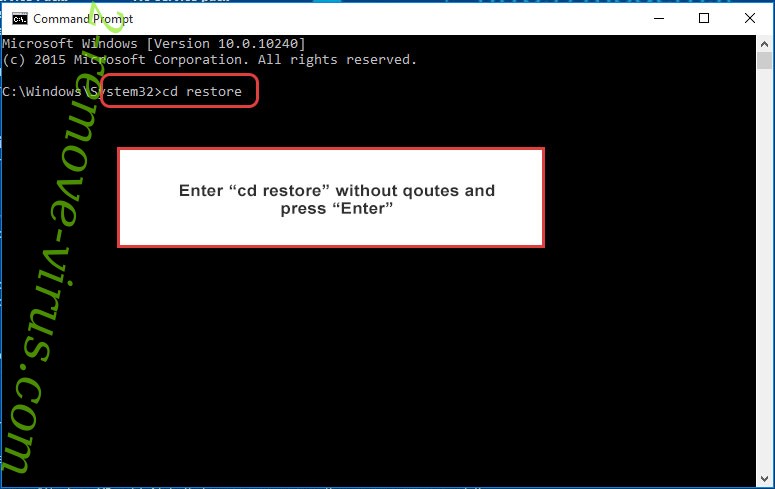
- Type in cd restore and tap Enter.

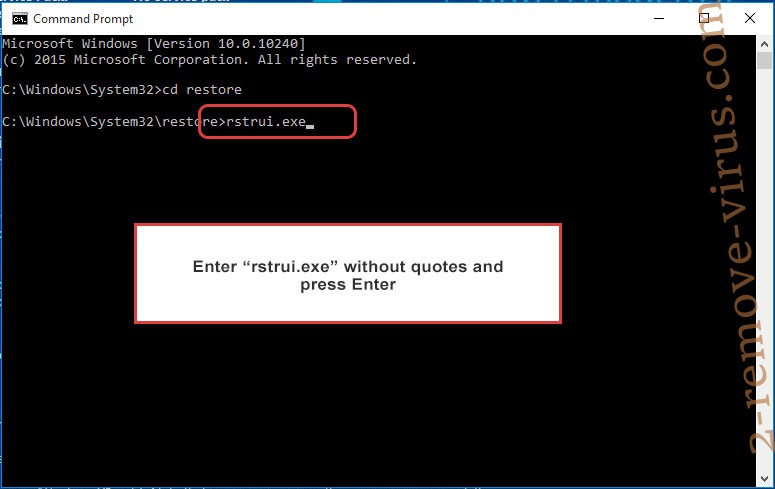
- Type in rstrui.exe and press Enter.

- Click Next in the new window and select the restore point prior to the infection.

- Click Next again and click Yes to begin the system restore.

Delete icrypt@cock.li Ransomware from Windows 8/Windows 10
- Click the Power button on the Windows login screen.
- Press and hold Shift and click Restart.


- Choose Troubleshoot and go to Advanced options.
- Select Command Prompt and click Restart.

- In Command Prompt, input cd restore and tap Enter.


- Type in rstrui.exe and tap Enter again.


- Click Next in the new System Restore window.

- Choose the restore point prior to the infection.


- Click Next and then click Yes to restore your system.


Site Disclaimer
2-remove-virus.com is not sponsored, owned, affiliated, or linked to malware developers or distributors that are referenced in this article. The article does not promote or endorse any type of malware. We aim at providing useful information that will help computer users to detect and eliminate the unwanted malicious programs from their computers. This can be done manually by following the instructions presented in the article or automatically by implementing the suggested anti-malware tools.
The article is only meant to be used for educational purposes. If you follow the instructions given in the article, you agree to be contracted by the disclaimer. We do not guarantee that the artcile will present you with a solution that removes the malign threats completely. Malware changes constantly, which is why, in some cases, it may be difficult to clean the computer fully by using only the manual removal instructions.
