What is Calipso.god@aol.com?
Calipso.god@aol.com is an email address used by the hackers responsible for this ransomware infection. It is very similar to another program that belongs to this category named Vipasana Ransomware. The main goal of the malign software is to make profit off of computer users by taking their files “hostage”. The threat slithers into your PC through spam emails with infected attachments, malicious links, fake ads, etc. It starts corrupting your data files, thus making them useless to you. Once the encryption is complete, the parasite demands that you pay a ransom in exchange for a decryption key that can decode your files. We advise against that. Instead, you should terminate Calipso.god@aol.com as soon as you can.
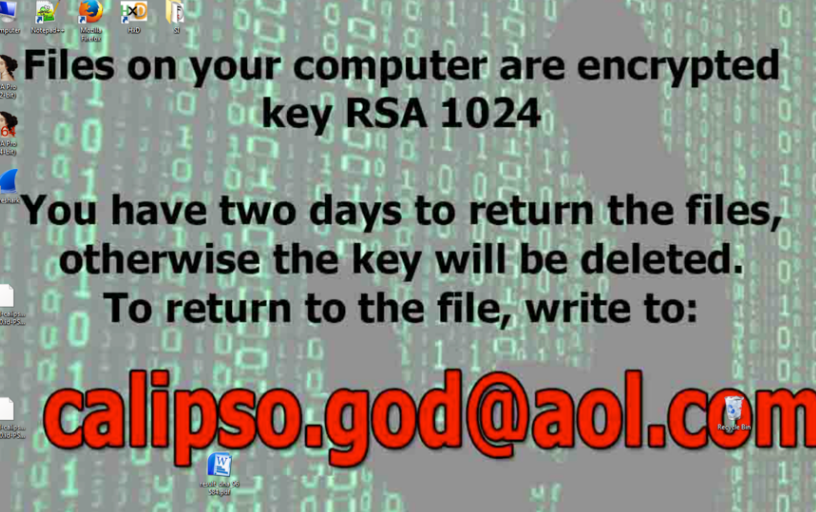
How does Calipso.god@aol.com work?
As we have already mentioned, the harmful software uses different tricks to spread online. You may have downloaded it as an email attachment thinking that it is a legitimate file as this is one of the most widespread techniques used by malware. You should always be cautious while browsing the Web, especially if you do not have anti-malware installed on your PC. Before you download a file or visit a website make sure that it can be trusted.
After the ransomware takes over your PC, it starts encrypting your files including your photos, videos, music, documents, presentations, and other important data. The encryption process usually goes by unnoticed by the user. The only symptom you may experience is slower system performance. Once all of your files are corrupted, the infection presents you with a ransom note, which states that your data has been encrypted with RSA-1024 cryptographic algorithm and that you should send 1 file to the provided email address. It also informs you of the fact that you have 2 days to make the payment, otherwise the decryption key will be deleted. It is clear that if you contact the cyber crooks, they will demand that you pay them. The sum may vary. Whatever it is, we urge you not to waste your money and find a different way to get your files back. Before you can do that, however, you need to get rid of Calipso.god@aol.com.
How to remove Calipso.god@aol.com?
You can eliminate Calipso.god@aol.com from your computer with the help of a powerful anti-malware utility. The anti-malware can be acquired on our website. It will scan your system and detect all malicious components. The security software will delete Calipso.god@aol.com and other threats that it finds. It will also keep your PC safeguarded after Calipso.god@aol.com removal is complete. As for your files, you can restore them from backup, if you have one. If not, you can try using the System Restore feature or the Shadow Explorer software. There is no decryption tool developed specifically for this ransomware yet, however, you can choose from a variety of free data recovery programs. Make sure that you erase Calipso.god@aol.com before you try them out.
Offers
Download Removal Toolto scan for Calipso.god@aol.comUse our recommended removal tool to scan for Calipso.god@aol.com. Trial version of provides detection of computer threats like Calipso.god@aol.com and assists in its removal for FREE. You can delete detected registry entries, files and processes yourself or purchase a full version.
More information about SpyWarrior and Uninstall Instructions. Please review SpyWarrior EULA and Privacy Policy. SpyWarrior scanner is free. If it detects a malware, purchase its full version to remove it.

WiperSoft Review Details WiperSoft (www.wipersoft.com) is a security tool that provides real-time security from potential threats. Nowadays, many users tend to download free software from the Intern ...
Download|more


Is MacKeeper a virus? MacKeeper is not a virus, nor is it a scam. While there are various opinions about the program on the Internet, a lot of the people who so notoriously hate the program have neve ...
Download|more


While the creators of MalwareBytes anti-malware have not been in this business for long time, they make up for it with their enthusiastic approach. Statistic from such websites like CNET shows that th ...
Download|more
Quick Menu
Step 1. Delete Calipso.god@aol.com using Safe Mode with Networking.
Remove Calipso.god@aol.com from Windows 7/Windows Vista/Windows XP
- Click on Start and select Shutdown.
- Choose Restart and click OK.

- Start tapping F8 when your PC starts loading.
- Under Advanced Boot Options, choose Safe Mode with Networking.

- Open your browser and download the anti-malware utility.
- Use the utility to remove Calipso.god@aol.com
Remove Calipso.god@aol.com from Windows 8/Windows 10
- On the Windows login screen, press the Power button.
- Tap and hold Shift and select Restart.

- Go to Troubleshoot → Advanced options → Start Settings.
- Choose Enable Safe Mode or Safe Mode with Networking under Startup Settings.

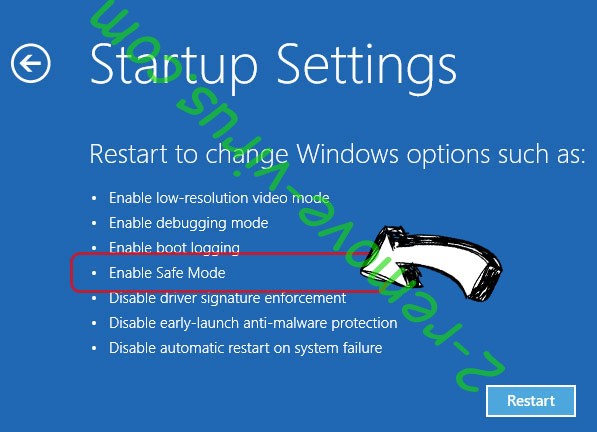
- Click Restart.
- Open your web browser and download the malware remover.
- Use the software to delete Calipso.god@aol.com
Step 2. Restore Your Files using System Restore
Delete Calipso.god@aol.com from Windows 7/Windows Vista/Windows XP
- Click Start and choose Shutdown.
- Select Restart and OK


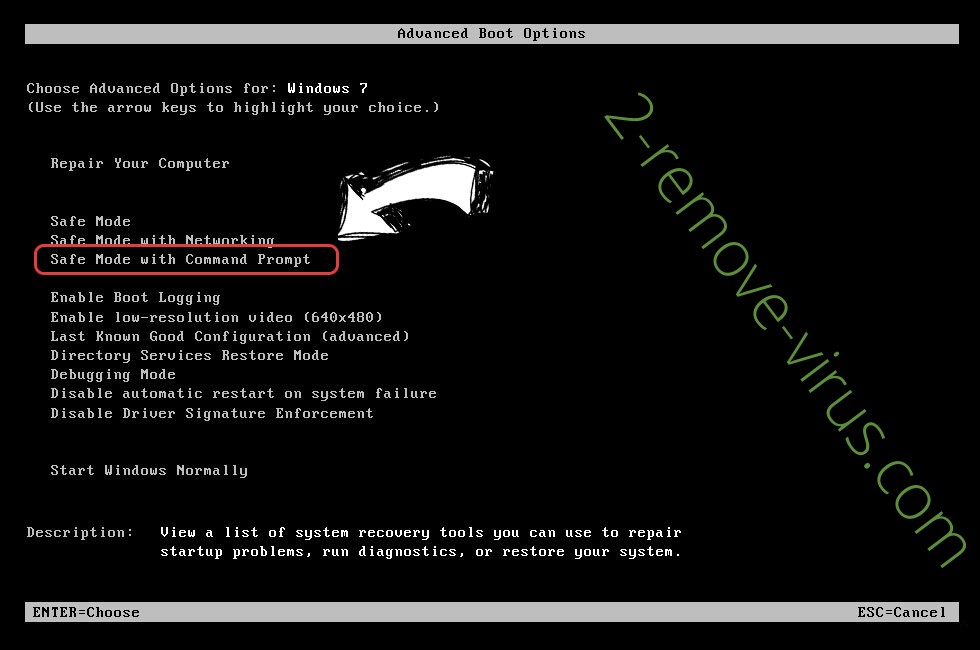
- When your PC starts loading, press F8 repeatedly to open Advanced Boot Options
- Choose Command Prompt from the list.

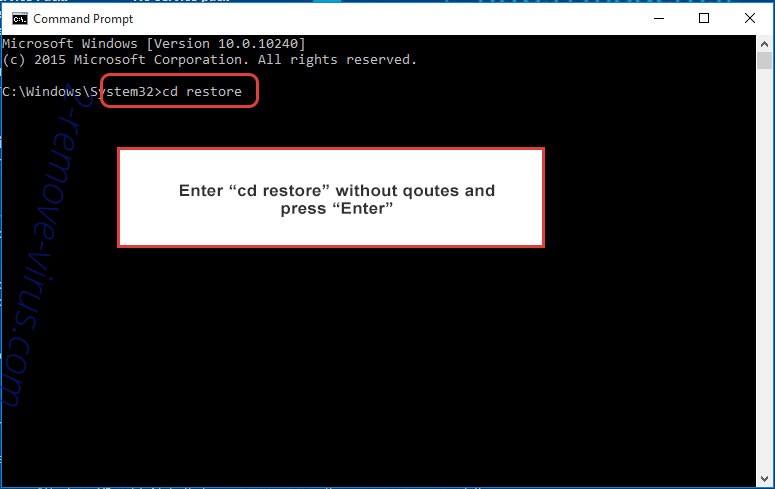
- Type in cd restore and tap Enter.

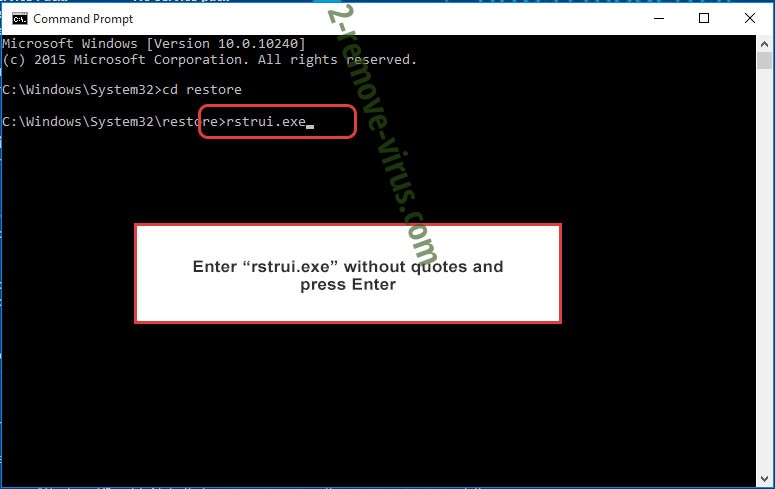
- Type in rstrui.exe and press Enter.

- Click Next in the new window and select the restore point prior to the infection.

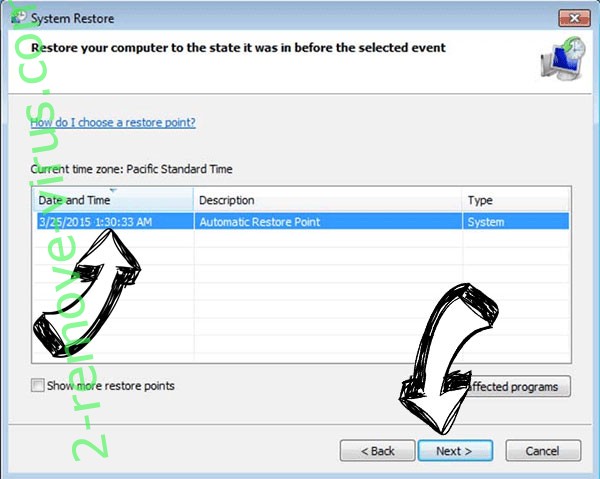
- Click Next again and click Yes to begin the system restore.

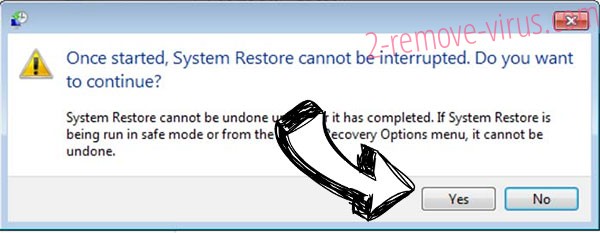
Delete Calipso.god@aol.com from Windows 8/Windows 10
- Click the Power button on the Windows login screen.
- Press and hold Shift and click Restart.


- Choose Troubleshoot and go to Advanced options.
- Select Command Prompt and click Restart.

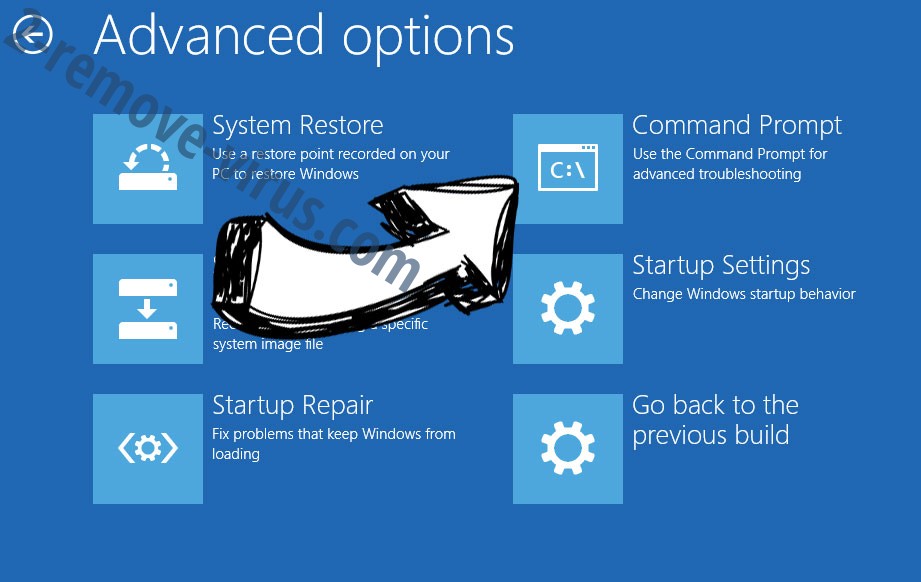
- In Command Prompt, input cd restore and tap Enter.


- Type in rstrui.exe and tap Enter again.


- Click Next in the new System Restore window.

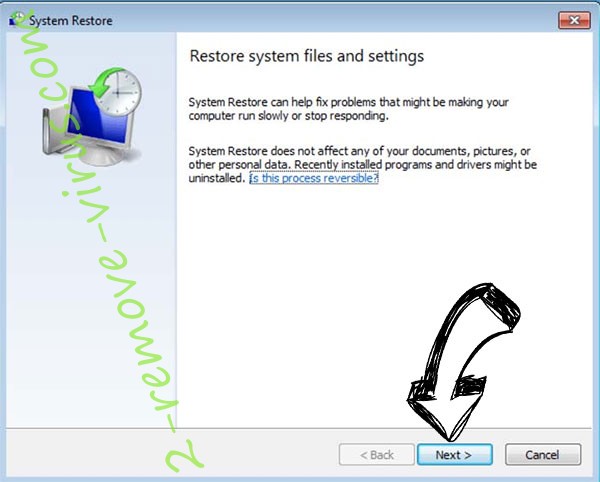
- Choose the restore point prior to the infection.


- Click Next and then click Yes to restore your system.


Site Disclaimer
2-remove-virus.com is not sponsored, owned, affiliated, or linked to malware developers or distributors that are referenced in this article. The article does not promote or endorse any type of malware. We aim at providing useful information that will help computer users to detect and eliminate the unwanted malicious programs from their computers. This can be done manually by following the instructions presented in the article or automatically by implementing the suggested anti-malware tools.
The article is only meant to be used for educational purposes. If you follow the instructions given in the article, you agree to be contracted by the disclaimer. We do not guarantee that the artcile will present you with a solution that removes the malign threats completely. Malware changes constantly, which is why, in some cases, it may be difficult to clean the computer fully by using only the manual removal instructions.
