Fruity trojan is a dangerous trojan infection that targets Windows computers. It’s a downloader-type infection, which means its main purpose is to open doors for other malware to enter the computer. When present on a computer, it will be able to download additional malware, including banking trojans and ransomware. It’s a stealthy infection so it may be difficult to notice without a good anti-virus program. It may also employ techniques to prevent detection by anti-virus programs.
Currently, Fruity trojan is used to spread the Remcos RAT infection. It’s a remote administration tool that would allow operators access to infected devices remotely. Such infections can do a significant amount of damage because operators can steal sensitive information (passwords, saved payment card details, etc.), and monitor what users are doing. Despite the fact that Fruity trojan is currently distributing the Remcos RAT infection, that can change at any time. It could later install additional malware, such as ransomware.
What makes infections like the Fruity trojan so dangerous is their stealth. Once it successfully infects a computer, it will not show any obvious signs of being present. It can stay hidden for a while, carrying out its programmed tasks. At the moment, its task is to install the Remcos RAT infection so it can steal users’ sensitive information. If Fruity trojan changes to distributing ransomware, for example, it would spell more trouble for infected users. Users’ files would be encrypted and potentially lost for good.
Some trojans can exhibit signs of being present. If users know what they are, they may be able to notice an infection in time even without an anti-virus program. Those signs include a suddenly slow computer without a reason, programs lagging or outright crashing, and unknown processes in your Task Manager using up a lot of your computer’s resources. However, these signs will not necessarily be visible, which is why having a reliable anti-malware program installed is so important.
If the Fruity trojan was detected on your computer, it’s possible that the Remcos RAT is also present. If that is the case, you need to change all of your passwords immediately. However, you first need to remove Fruity trojan, as well as Remcos RAT using anti-malware software.
How to avoid trojan infections
Fruity trojan is usually distributed via fake websites that promote seemingly useful tools like system optimizers. There are various ways users could end up on those fake websites, including clicking on unknown links and random redirects. Users may also encounter ads promoting these fake tools on various questionable websites. Some of those websites include atiflash.ru, aevga-precision.com, more-power-tool.com, srbpolaris.ru, and techpowerup-gpu-z.com.
The fake sites hiding Fruity trojan contain download links. If users click on the download link, they would be taken to MEGA, a file-hosting service website. It should be noted that when users download the ZIP file, extract and launch the executable, the program users wanted will actually install. However, alongside it, the Fruity trojan will also be set up. This is a clever trick because users may not notice anything unusual since they do get the program they wanted.
This situation is a great example of why users need to be very careful with where they download their programs from. Programs should only be downloaded from trusted sources, such as official websites and app stores. Users should certainly never download anything from ads or redirects. It’s also very important to research programs before installing them. All programs that conceal Fruity trojan are unknown, and a simple search with Google would reveal they should be avoided.
Trojans are also spread via email attachments, as well as torrents. Users need to be very careful with emails from unknown senders, especially if they contain attachments or links. All email attachments should be scanned with anti-virus software or VirusTotal before they’re opened. Users should also avoid downloading copyrighted content via torrents because malware can often be encountered there.
Fruity trojan removal
Trojan infections are very serious so it’s essential to deal with them right away before they can do any damage. And because they can be hard to notice without an anti-virus program, you need to have one installed at all times. The program would immediately detect and delete Fruity trojan as it’s trying to activate, preventing an infection. We do not recommend trying to remove Fruity trojan manually because you could end up causing additional damage unless you know exactly what to do.
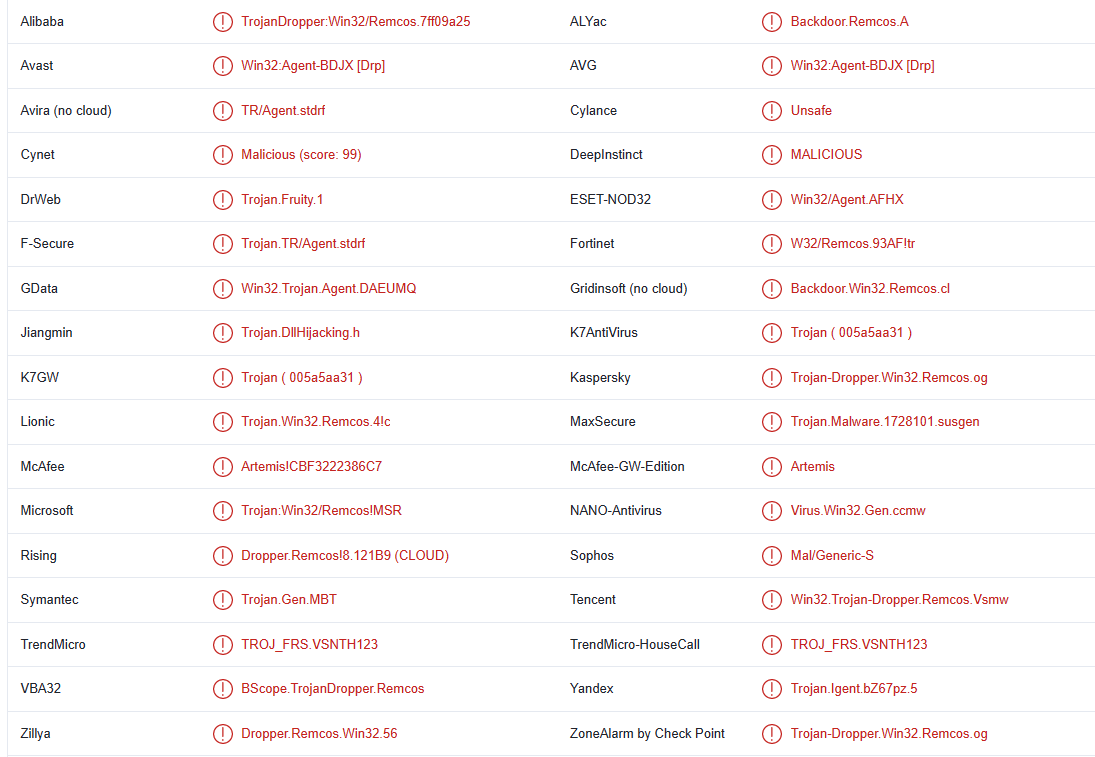
Fruity trojan is detected as:
- Win32:Agent-BDJX [Drp] by Avast/AVG
- Artemis!CBF3222386C7 by McAfee
- Trojan:Win32/Remcos!MSR by Microsoft
- TROJ_FRS.VSNTH123 by TrendMicro
- Win32/Agent.AFHX by ESET
- Trojan-Dropper.Win32.Remcos.og by Kaspersky
Quick Menu
Step 1. Uninstall Fruity trojan and related programs.
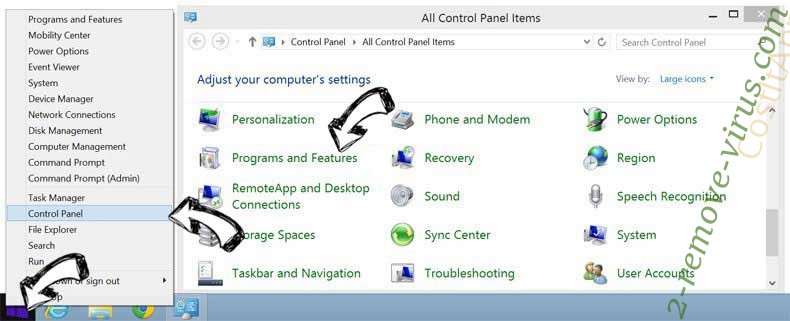
Remove Fruity trojan from Windows 8
Right-click in the lower left corner of the screen. Once Quick Access Menu shows up, select Control Panel choose Programs and Features and select to Uninstall a software.
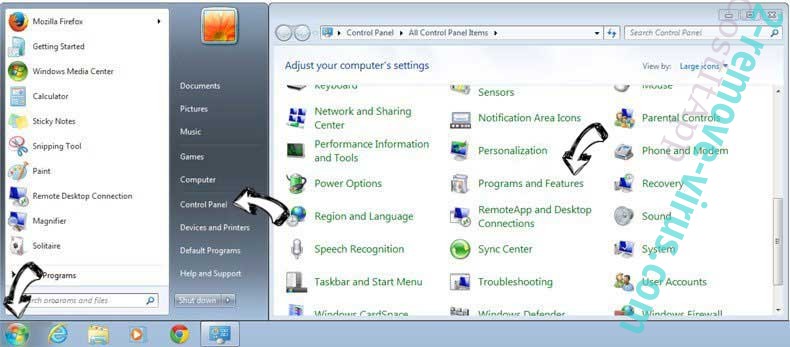
Uninstall Fruity trojan from Windows 7
Click Start → Control Panel → Programs and Features → Uninstall a program.
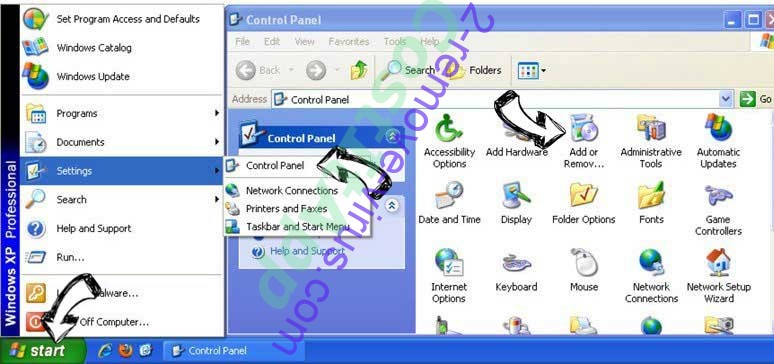
Delete Fruity trojan from Windows XP
Click Start → Settings → Control Panel. Locate and click → Add or Remove Programs.
Remove Fruity trojan from Mac OS X
Click Go button at the top left of the screen and select Applications. Select applications folder and look for Fruity trojan or any other suspicious software. Now right click on every of such entries and select Move to Trash, then right click the Trash icon and select Empty Trash.

Offers
Download Removal Toolto scan for Fruity trojanUse our recommended removal tool to scan for Fruity trojan. Trial version of provides detection of computer threats like Fruity trojan and assists in its removal for FREE. You can delete detected registry entries, files and processes yourself or purchase a full version.
More information about SpyWarrior and Uninstall Instructions. Please review SpyWarrior EULA and Privacy Policy. SpyWarrior scanner is free. If it detects a malware, purchase its full version to remove it.

WiperSoft Review Details WiperSoft (www.wipersoft.com) is a security tool that provides real-time security from potential threats. Nowadays, many users tend to download free software from the Intern ...
Download|more


Is MacKeeper a virus? MacKeeper is not a virus, nor is it a scam. While there are various opinions about the program on the Internet, a lot of the people who so notoriously hate the program have neve ...
Download|more


While the creators of MalwareBytes anti-malware have not been in this business for long time, they make up for it with their enthusiastic approach. Statistic from such websites like CNET shows that th ...
Download|more
Site Disclaimer
2-remove-virus.com is not sponsored, owned, affiliated, or linked to malware developers or distributors that are referenced in this article. The article does not promote or endorse any type of malware. We aim at providing useful information that will help computer users to detect and eliminate the unwanted malicious programs from their computers. This can be done manually by following the instructions presented in the article or automatically by implementing the suggested anti-malware tools.
The article is only meant to be used for educational purposes. If you follow the instructions given in the article, you agree to be contracted by the disclaimer. We do not guarantee that the artcile will present you with a solution that removes the malign threats completely. Malware changes constantly, which is why, in some cases, it may be difficult to clean the computer fully by using only the manual removal instructions.